The Desktop FilesShared Computing with Windows SteadyState
Wes Miller
I know if you've been anywhere near a computer lab in the last 10 years or so, you're familiar with this problem. It was something I first saw when I was in college. At the time, the labs were open all hours of the day (with your student ID) and were effectively unattended once you were in the library. The student gamers of that era
would come in and make modifications to the key Windows® and MS-DOS® files to run their games. The end result was a machine that might run their game well, but didn't run Windows well, if at all. We've all experienced it at some point—the shared-use computer that has been beaten down to the point that trying to use it is no longer an effective use of time.
Recently I took a vacation to South Padre Island here in Texas. The hotel I stayed at had three computers in a "guest computer room" running Windows XP. Everyone running on these Windows systems was an administrator and they had no policies in place—meaning each of these poor computers had been abused pretty heavily by visitors installing rogue software and removing or changing core apps—most likely not the experience the hotel had intended. Whether in a lab or a hotel, the truth is that shared-use computers in a public environment are put through a punishing life that often bests what some home computers see.
Solutions to the Problem
Getting and Using SteadyState
Windows SteadyState is available as a free download from go.microsoft.com/fwlink/?LinkId=104721. More information about SteadyState is available from microsoft.com/windows/products/winfamily/sharedaccess.
Windows SteadyState will run on any system that can run Windows XP. The most significant improvement over the SCT is that SteadyState does not require a second partition to function as SCT did for Windows Disk Protection.
The following table provides an overview of the system requirements for SteadyState. Note that SteadyState does need an NTFS-formatted file system, though any version of Windows XP is supported. SteadyState does not currently work with Windows Vista®.
| Component | Requirement |
| Processor | 300 MHz or higher (233 MHz minimum). |
| Memory | 128MB of RAM or higher (64MB minimum; may limit performance and some features). |
| Hard disk | Minimum of 1.5GB of available hard disk space without Windows Disk Protection, or a minimum of 4.0GB of available hard disk space with Windows Disk Protection. |
| Operating system | Windows XP Home Edition, Windows XP Professional. or Windows XP Tablet PC Edition. Windows XP SP2 must be installed. |
| Supported localized languages | English, Dutch, French, Italian, Japanese, Portuguese Brazilian, Simplified Chinese, and Spanish. |
| File system | NTFS formatted file system. |
| Access | Administrator level access. |
If you've been reading my column for the past year, or if you're familiar with Windows deployment in general, you might be thinking, "big deal—I'll just re-image the systems." But those of you who have lived that life know it's not always that simple. Hitting the big red reimage button every day or every week doesn't really scale.
Years ago, a friend and I looked into starting a cybercafé. This was back in 1995 when it was still a somewhat unique idea. My biggest concern was actually ensuring system reliability and availability. Unfortunately, the options at that time were largely all reimaging or slightly more robust solutions; there wasn't anything plug-and-play to solve the problem.
Breaking down the issue, when securing shared-use computers, you want to be able to do three things:
- Ensure that users run only as non-administrators. This should always be the case on shared computers.
- Put policy into place so the systems are as secure as possible. That way, there's a low potential of users being able manipulate areas of the system they shouldn't have access to.
- Be able to roll back any random changes made by users. Even if users are running as non-administrators, they can still make rogue changes to menus, favorites, and so on.
Fortunately, Microsoft has been working for several years on a toolset designed to help in just this scenario.
History of SteadyState
A little over a year ago, Microsoft released the Windows Shared Computing Toolkit (SCT). Available as a free download for Windows Genuine Advantage verified systems, the toolkit was designed specifically with libraries, cybercafés, labs, and other shared computing environments in mind. You may have seen coverage of the SCT back in the July 2006 issue of TechNet Magazine (technetmagazine.com/issues/2006/07/UtilitySpotlight).
A new version, now renamed Windows SteadyStateTM (microsoft.com/windows/products/winfamily/sharedaccess), shipped in June 2007. The new version was renamed in part because the toolset changed significantly between versions. It still performs the same tasks that I'll drill into in a moment, but the team focused on overall ease of use in the newest release. As a result, SteadyState is integrated tightly into a new console, and is easier to install and manage. It is more powerful and flexible, and it supports Active Directory® integration for one of its key components—meaning increased flexibility in several entirely new enterprise scenarios. It also now supports Windows Update integration so SteadyState has the intelligence to know when to turn Windows Disk Protection off to apply updates on its own. This reduces the management overhead you have to dedicate to your SteadyState-managed systems.
Features of SteadyState
Windows SteadyState consists of four key components: Computer Restrictions locks down per-computer security and configuration options; Windows Disk Protection caches (and reverts) changes to the Windows system partition; User Account Manager creates, edits, imports, or exports a user; and finally, User Restrictions and Settings locks down per-user security and configuration options.
One immediate improvement you'll notice over the Shared Computing Toolkit is the user help. A startup guide helps you get SteadyState up and running. Then SteadyState offers four key tasks to dive deeper into (mirroring the key features I outlined above):
- Set Computer Restrictions (Computer Restrictions).
- Schedule Software Updates. (Allows you to specify whether SteadyState automatically applies Windows Updates. This is recommended, since it handles dealing with Windows Disk Protection for you, and also updates the signatures of several popular Antivirus programs.)
- Protect the Hard Disk (Windows Disk Protection).
- Add User (User Account Manager).
Under Add User you'll find User Restrictions and Settings, which gives you a per-user configuration option.
Computer and User Restrictions and Settings
If you are familiar with Windows Group Policy, you are already familiar with the Set Computer Restrictions and User Restrictions and Settings aspects of SteadyState. Rather than forcing SteadyState administrators to use the Group Policy Object Editor (GPEdit.msc), which is not a feature that is available on Windows XP Home Edition (though SteadyState is supported on it), SteadyState bubbles up several key security and configuration options that are common in the shared computing scenario.
Figure 1 shows the configuration screen for Set Computer Restrictions. Note that these are all generic settings that will apply to the entire computer. These settings are primarily selected to minimize the security risks to the system—and in the case of USB drive access, the ability to remove things from the system. (When you look at per-user settings, you'll see a way to block read access to some or all drives, too.)
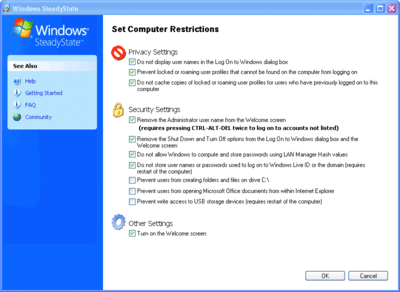
Figure 1** Computer restrictions in SteadyState **(Click the image for a larger view)
It's important to note that the USB setting is only active while running under the actual Windows installation where SteadyState is configured. In order to secure against offline attacks, you should properly configure the BIOS to block booting from USB or CD devices and password-protect the BIOS itself.
Of course, this is not foolproof. Remember the third law from the "10 Immutable Laws of Security" (microsoft.com/technet/archive/community/columns/security/essays/10imlaws.mspx): "If a bad guy has unrestricted physical access to your computer, it's not your computer anymore." A dedicated individual with enough time and the right tools can often bypass a BIOS password.
Windows Disk Protection
If you've ever used Windows XP Embedded from a CD, or Windows PE 2.0, what I'm about to describe is going to sound familiar, and for good reason—they have a shared history. Windows Disk Protection works to provide a full "undo" of the Windows system partition by saving all changes made to the system partition to a cache on the same partition. This aspect of SteadyState is critical, since it is the component that allows you to undo the changes made by users of the system over time.
Windows Disk Protection is useful primarily if you want to ensure that over time you can rapidly roll back (either after an unscheduled restart or at a scheduled interval) to the initial deployed state of the system. It has four modes you can set in the dialog shown in Figure 2:
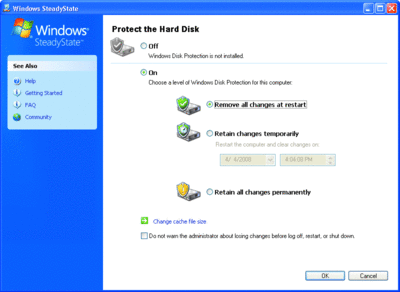
Figure 2** Configuring Windows Disk Protection **(Click the image for a larger view)
Off Windows Disk Protection is completely disabled, and all changes are written to disk normally.
On—Discard changes at reboot Windows Disk Protection is enabled, and every time you restart the computer, all changes will be discarded. In essence, this means the system will revert to exactly where it was when you checked and saved this option.
On—Discard changes at set time Almost identical to the previous options except changes are discarded at a set time, not at the next restart. This would be a logical choice if you wanted to discard changes daily or weekly.
On—Retain changes permanently Conceptually confusing with Off, but the difference here is that this is a temporary mode. For example, you could use this mode if you want to apply application updates, install new applications, or configure the system. This is not a mode you would generally run in for any significant length of time.
Note that Windows Disk Protection requires a reboot to change between any of these modes.
Schedule Software Updates
The Schedule Software Updates setting is handy in that SteadyState now has the ability to turn Windows Disk Protection off or on automatically for you. If you allow SteadyState to handle your updates, it sets Windows Disk Protection to keep the changes during the update and then returns Windows Disk Protection to what was previously set. I definitely recommend this setting since it eliminates one chore on your management task list.
The following security software is supported via the update feature in Software Updates: Computer Associates eTrust 7.0, McAfee VirusScan, Windows Defender, and TrendMicro 7.0.
User Account Manager
The Add User option lets you configure new users for the system. Figure 3 shows the options available for your new user: name, password, an image to represent the user, and the location of the user profile. Once you've created users, you can set User Restrictions and Settings for each of these local accounts. The nice thing is that once you've added and configured an account on your system, you can export it and then import it to another system as needed (or to archive it).
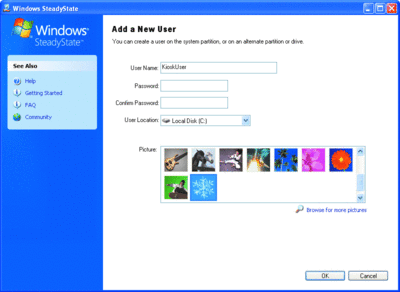
Figure 3** Adding user accounts **(Click the image for a larger view)
A handy aspect of the User Account Manager is that user profiles can be created on a secondary partition via the User Location menu shown in Figure 3. Usually profiles must be created on the Windows partition unless you manually specified a different Documents and Settings location during setup via an unattend.txt file. This approach is particularly useful with SteadyState since it discards changes made to the Windows system partition when Windows Disk Protection is enabled. If you want to have a user's profile remain consistent through Windows Disk Protection cache purges, you can simply specify the user's profile to be stored on another local partition when creating the user via User Account Manager.
This process works by rebooting to clear the Windows Disk Protection cache, applying the updates and then rebooting again to restart Windows Disk Protection. In addition to Windows Update, SteadyState will update the signature files for several popular antivirus applications that are supported (see the "Getting and Using SteadyState" sidebar). If your application is not supported or you need to run another updater, you can take care of the update manually—just ensure that Windows Disk Protection is disabled when you do so, or the signature update will be lost.
User Restrictions and Settings
Once you've selected a user, SteadyState breaks down User Restrictions into four categories. These are derived from Group Policy settings and will probably seem familiar to you.
The General settings control user profiles and forced logoff configurations. This includes settings for locking the profile and setting timeout intervals for logging out after either a configured duration of use or idle time.
The Windows Restrictions settings, shown in Figure 4, control Windows-specific configuration items. Examples include removing access to Windows user interface items such as components of the Start Menu, and Windows Explorer functionality. The ability to block access to specific drives by drive letter is also available, as is the ability to disable CD burning.
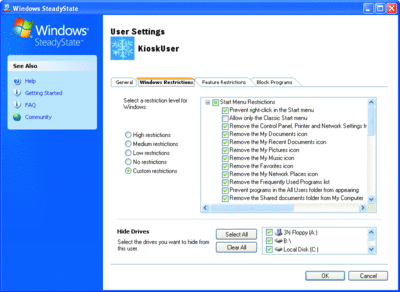
Figure 4** Windows-specific user restrictions **(Click the image for a larger view)
The Feature Restrictions tab, shown in Figure 5, controls granular access to most Internet Explorer® functionality, allows you to set the Internet Explorer home page, and to control Microsoft® Office functionality to a degree—largely around controlling the ability for Visual Basic® for Applications (VBA) scripts to be executed.
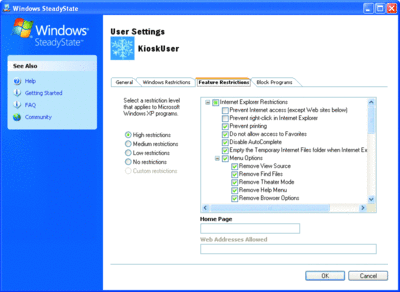
Figure 5** Feature restrictions **(Click the image for a larger view)
The Block Programs settings (see Figure 6) control the ability to run specific applications—basically you create a blacklist. This is populated with several common applications, and you can add others. Note that these items are blocked based on a definition of their path. If a user is allowed to move an application somewhere else on the system, the path rule won't apply any longer. Correctly applied file and directory ACLs and access restrictions to the system in other ways will prevent the easy ability to do this, however.
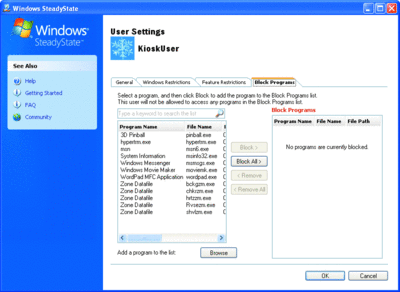
Figure 6** Blocking programs from executing **(Click the image for a larger view)
Another important new capability of SteadyState is based on the preconfigured templates that specify Restriction Levels related to both Windows Restrictions and Feature Restrictions. The templates make it easier to get a baseline configuration working depending on your desired level of feature/function lockdown. Of course you have the ability to build custom templates as well.
Limitations of SteadyState
SteadyState does a great job of helping an organization stabilize its shared computing systems. For a commercial tool, it would be good. For a free tool, it's very admirable. But, remember, it doesn't do everything.
Shared computing systems are easy targets for attack or even non-intentional abuse. You should ensure that these systems are isolated from information they don't need to be able to access. While SteadyState also has the ability to block access to applications, these enforcements are handled via Software Restriction Policies. And as Mark Russinovich noted a few years back, there are techniques whereby a savvy user can craft an app that looks benign, but even as a Limited User will still allow them to bypass these policies (blogs.technet.com/markrussinovich/archive/2005/12/12/circumventing-group-policy-as-a-limited-user.aspx). Short of blocking all device access and Internet access, this is a vulnerability you'll need to bear in mind. Always remember Law #3 ...
Obviously, SteadyState is just one component of a well-configured shared computing system. Regular application of updates via Windows Update and proper configuration of Windows Firewall (or another firewall) are important. Also, be sure to install and configure antivirus, anti-spyware, and other security countermeasures necessitated by analyzing the potential risks to the computer. Likewise, control access to the computer—if you can't control that, control what the computer can see. And don't store confidential data locally.
Finally, when qualifying your platform, make sure your testing includes using SteadyState (with Windows Disk Protection enabled, unless you plan to not use it) and all additional software you plan to run on the system. You will want to ensure that the software and SteadyState work optimally together.
Support for SteadyState
The user feedback I've seen for SteadyState is very positive. There are a few minor gotchas I've heard of so far, some involving the order in which you need to add users. Many of these gotchas (along with other tips and tricks) are covered in the very active Windows SteadyState Community (conveniently linked to from several places in the SteadyState application and documentation) at forums.microsoft.com/windowstoolsandutilities.
I'd also recommend before starting that you review the SteadyState handbook, which is available at go.microsoft.com/fwlink/?LinkId=104722. It provides quite a few tips and tricks to using SteadyState successfully.
Wrap-Up
SteadyState provides a great package of functionality for any Windows XP system for which you need to control access to—and it's free! The dramatically improved Windows Disk Protection functionality and user interface enhancements mean easier deployment and easier overall management of your shared-access systems.
Whether your needs are for computer lab systems, visitor or employee shared-access kiosks, training rooms, or any other shared computing needs, SteadyState can help you get—and keep—the systems up and running easier. And it won't require you to do any more weekly reimaging just to jumpstart a system over again. That's a huge improvement in my book.
Wes Milleris a Technical Product Manager at Initiate Systems (InitiateSystems.com) in Austin, Texas. Previously, he worked at Winternals Software and as a Program Manager for Microsoft. Wes can be reached at technet@getwired.com.
© 2008 Microsoft Corporation and CMP Media, LLC. All rights reserved; reproduction in part or in whole without permission is prohibited.