ToolboxNew Products for IT Pros
Greg Steen
Monitor Remote Connections
RecordTS
Have you ever wished you had an eye into your Terminal Server or Remote Desktop sessions? Maybe you want to know what was going on before your Remote Desktop session seemed to take down your Web site. Maybe you have an issue on your Terminal Server that you just can’t seem to replicate. Perhaps you’re concerned about security of intellectual property. Or it could be that you need to make a quick log or presentation on how you configured your SharePoint® server in a test environment. If any of these scenarios sound familiar, you should check out RecordTS from TSFactory. (TSFactory was formed by Cláudio Rodrigues, a Microsoft MVP for Terminal Services.)
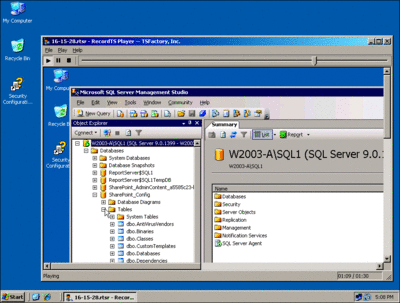
RecordTS is available in two editions: Terminal Server and Remote Desktop. The right edition for you will depend on what types of connections you want to monitor. As the product Web site attests, RecordTS acts as a "security camera" into Terminal Server or Remote Desktop sessions. The software basically acts as a proxy between Terminal Services and the end-user session, allowing it to record every movement and action taken in a session.
The intuitive installation uses a simple wizard in which you point the application to the data directory where you would like to store saved sessions. The application installs an MMC snap-in (which lets you configure the service), the RecordTS service, and a session playback utility for watching recorded sessions. After opening the MMC snap-in, right-clicking on the service folder brings up a property screen where you can configure settings such as which port you want the service to run on. (This particular setting is useful if you have shifted your Terminal Services sessions to a nonstandard port.) On the Storage tab, you can set the Default Storage Folder to a local folder or a UNC path.
You can also configure the directory structure of the stored sessions. For example, you might use the domain, user, and date and time to organize the data being saved. And, perhaps the most important setting if you are storing sessions on a local disk, you can tell the service what to do if the disk runs out of space. You can choose to either not allow new connections and disconnect current sessions (the choice for the highly security conscious) or you can select to turn off session recording (the option you’ll want if you don’t want to disrupt productivity).
Under the Security tab, you can specify if you want to digitally sign all the recorded sessions by selecting an existing certificate or creating a self-signed certificate. This is worth doing if you plan to use the tool for auditing or liability purposes. On the Users tab, you can specify users who should have their sessions recorded or ones who shouldn’t.
All in all, RecordTS can be an invaluable tool for security and auditing, and its uses can be much broader, such as allowing you to record a how-to presentation. I know I find it a handy addition to my toolbox.
Price: RecordTS Remote Desktop Edition starts at $495. RecordTS Terminal Services Edition starts at $995.
Host Monitoring
Advanced Host Monitor
If you ever find yourself in a position of providing operational support for a mission-critical infrastructure, there is one sleep aid you can’t do without: a good, reliable host monitor. Even if you have a rock-solid hardware set and a stable and reliable application stack with no single points of failure, you’ll still want a full-featured host monitor to tell you when that redundant system has to kick in.
Advanced Host Monitor, from KS-Soft, touts having 58 different test methods and 30 alert methods. You can check for such items as process information, user sessions, average load, memory, and so on. The application provides Windows®-specific tests, Linux/UNIX tests, and platform-independent checks. Unlike the Windows tests, the Linux/UNIX tests require the installation of a Remote Monitoring Agent on the client.
There is also a Windows Management Instrumentation (WMI) monitoring test. You can browse for the correct query with the embedded WMI Explorer, which lets you easily navigate to and choose the appropriate item, as well as execute the query to verify that it will get you the data you need.
Advanced Host Monitor also has a number of database-related tests such as an ODBC query test, which verifies the availability of an ODBC data source, runs a query, and verifies the result against a known value. You can also check a host’s ability to accept incoming sessions for SQL Server™, MySQL, Oracle, Postgres, Sybase, and Interbase database servers.
There are a number of disk and file-related tests to help you keep tabs on free space, quotas, folder or file availability, and the availability of UNC shares. In addition, you get the standard network-related tests: general TCP/UDP checks, mail tests (for SMTP, POP3, and IMAP), mail relay checks, HTTP content and timing tests, and so on. You can also create monitor test interdependencies to cascade your checks, a useful option. Tests can also be scheduled on what is termed regular and irregular schedules, allowing you to be quite granular with your testing patterns.
Some of the alerting methods include sending messages to SMS, ICQ, e-mail, an event log, or a pop-up window. They can also trigger other events, such as starting or stopping services, rebooting the machine, or executing an external program.
With both the Professional and Enterprise editions of Advanced Host Monitor, you get the KS-Soft IP-tools—a set of 19 TCP/IP-related network utilities that includes port/protocol scanners and an SNMP trap watcher, which allows you to receive and process SNMP trap messages. In addition, both versions have a log analyzer and reporting component that allow you to trend historical monitoring data for your uptime reports and performance analysis reviews.
The interface itself provides a great way to get a quick overview of a number of tests simultaneously. With it, you can easily scan for issues on your monitored hosts.
Price: $599 for the Enterprise edition. $275 for the Professional edition.
Disk Cleanup
WinDirStat
Much like your house or apartment, file storage locations tend to become cluttered over time with material that had purpose at one time, but now is just taking up valuable space. A little spring cleaning can do a lot of good, but, unlike your home, a directory tree structure doesn’t give you obvious visual clues as to where to start removing the clutter. Fortunately, there is a great visualization tool that can help you see what files are taking up space in your environment.
The GPL program WinDirStat, a Windows-based tool inspired by the Linux KDE kdirstat, shows you the files on selected drive as a set of different colored squares. The size of the squares represent the size of the files, letting you easily spot those unneeded behemoths of old ISO or ZIP files.
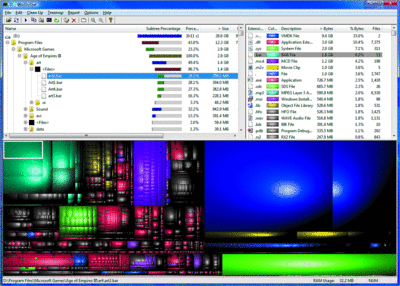
After you select your local drive (or a set of local drives), the program scans the directory tree, creating an in-memory map of the files. It then displays the visualization in the bottom pane of the GUI. Clicking on a colored square in the bottom pane navigates the Windows Explorer-like top pane to the location of the file. That top pane gives you useful stats like the file size, the date of the last change to that file, and other attributes. In addition, you see what percentage of the sub-tree is taken up by that file.
A very cool touch, colors are specific to file types, and clicking on a detected file type in the top-right will highlight all files of that type in the bottom pane. This is handy, for example, when you need to identify all those hidden MP3s your users have on the file server. You can also see what percentage of bytes those files comprise on the partition.
Price: Free download.
Book Review
Enemy at the Water Cooler
Almost all businesses need to be connected to the Internet, and most are aware of the dangers presented by nearly constant attempts from the outside to compromise the connection points that segment the "outside" from the "inside" of their information infrastructure. However, many businesses overlook a potentially more damaging threat that exists within the organization. The power of these so-called insider threats is nicely illustrated in Enemy at the Water Cooler: Real-Life Stories of Insider Threats and Enterprise Security Management Countermeasures by Brian Contos (Syngress, 2006).
Contos offers real-world stories of past attacks and the impact they had on the companies involved. He claims that security is an ongoing process that consists of a "merger of people, process, and technology." With this book, he tries to illustrate the potential power of Enterprise Security Management (ESM) software solutions to mitigate insider threats.
As ArcSight’s Chief Security Officer, Contos relies heavily on the presentation of the company’s own ESM software solution, but that doesn’t detract from the overall value. The book lacks deep technical details, but you get a good idea of where to enhance your own security process in your organization by seeing where other organizations have failed and by understanding what an effectively implemented ESM solution can do to reduce exposure to an inside attack.
In the background chapter, "Cyber Crime and Cyber Criminals 101," Contos offers an overview of some of the different types of attackers to be aware of and their motivations. You also get a brief synopsis of some of their techniques, such as buffer overflows, code-packing, and Warhol Threats.
The following chapter delves deeper into the specifics of insider threats, including the ways in which an insider can damage a business, the concept of managing risk, and ways to address threats from a technical perspective. The technical perspective gives a brief overview of least privilege, strong authentication, access control, and incident detection and management. This paves the way to a discussion of ESM software solutions. Again, the book tends to deal only with the ArcSight product, but the key feature breakdown is applicable to any system.
The book provides a number of case scenarios from a cross-section of industries and environments, detailing different types of insider threats and how they were detected (and sometimes mitigated). These case studies may shed light onto some of your own business practices and perhaps offer solutions for reducing the risk of insider attacks in your environment.
Price: $49.95.
Write to Toolbox
If you have a favorite tool or utility you would like to see featured here, please write to the author at tntools@microsoft.com.
Greg Steen is a technology professional, entrepreneur, and enthusiast. He is always on the hunt for new tools and methods to help make operations and development easier for IT professionals.
© 2008 Microsoft Corporation and CMP Media, LLC. All rights reserved; reproduction in part or in whole without permission is prohibited.