Communications
Better Compliance with Exchange Server 2007
Alan Maddison
At a Glance:
- Managed Folders
- Transport Rules
- Message Classification
- Journaling
Analysts estimate that as much as 75 percent of corporate documentation is created and communicated via e-mail. No doubt, a significant amount of your organization’s intellectual property lives on its messaging servers. This puts a lot of responsibility in the
hands of the administrators who maintain the messaging servers, which have come to house so much of your company’s critical data. Furthermore, the growing number of federal and local regulations (both in the United States and in other countries) that specify archiving and retention requirements for corporate data only make this job more complex and more critical.
The need to protect corporate assets and ensure regulatory compliance imposes a significant burden. In designing Exchange Server 2007, Microsoft has implemented a number of changes and new features to dramatically improve the compliance capabilities of Exchange while making the actual management easier. In this article, I take a look at the key changes in Exchange Server 2007 that will help with your regulatory compliance.
Understanding Compliance
Before I dive into Exchange Server 2007, I should discuss the requirements that are being addressed. There are generally three broad areas of compliance requirements: information retention, access control, and data integrity. For example, in the United States, SEC Rule 17A-4 specifies data retention policies for certain stock exchange members, brokers and dealers, and it requires financial organizations to be able to capture, index, archive, search, and retrieve their e-mail. Controlling access to data is incorporated into a number of well-known pieces of legislation, including the Health Insurance Portability and Accountability Act (HIPAA), the Gramm-Leach-Bliley Act (or GLB Act), and California Senate Bill 1386 (or SB 1386). HIPAA and the GLB Act regulate the security and confidentiality of personal data while SB 1386 mandates public disclosure of computer security breaches involving confidential data.
Furthermore, data integrity requirements have been incorporated into other important pieces of legislation, such as Sarbanes-Oxley (SOX), the PATRIOT Act, and Basel II. But these high-profile regulations are just a drop in the bucket. Some estimates put the number of regulations enforced world-wide at more than 35,000. Clearly there is motivation for companies to control the risk associated with how they retain information, control data access, and ensure data integrity. So how can you, as an administrator, manage this risk and what can you do to meet all these regulatory obligations?
The first step is to document compliance and retention policies. The next step is to implement and continually manage these policies. Exchange Server 2007 can help you enact these policies, through the use of managed folders, the Transport Rules agent, message classification, and the Journaling agent.
Managed Folders
Data retention (or records management) is a critical part of your compliance framework. Exchange Server 2007 has taken a big leap forward in how it allows administrators to manage data. In Exchange Server 2007, records management is based on three principles: obsolete messages are removed, required messages are retained, and users are responsible for classifying their own messages.
Most Exchange administrators are familiar with the Exchange Server 2003 Mailbox Manager policies, which could be applied to mailboxes. In Exchange Server 2007, managed folders provide a centrally managed way for administrators to create and deploy new default or custom folders that cannot be moved, renamed, or, in most cases, deleted. Using the SDK, it is also possible to create Web-based self-service applications that give users the ability to choose which folders should be added to their mailboxes.
As Figure 1 shows, the Exchange Management Console provides a wizard-based approach to folder creation. (This functionality is also exposed through the Exchange Management Shell New-ManagedFolder cmdlet.)
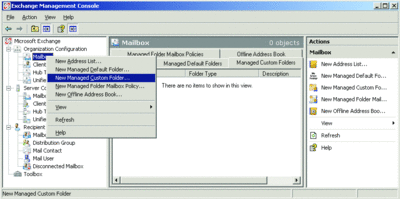
Figure 1** Using the Exchange Management Console to create a new folder **(Click the image for a larger view)
This launches the wizard shown in Figure 2. The process for creating the folders is very straightforward; you simply enter the name and description of the folder and then press the New button. Once the folder is complete, you will receive a confirmation.
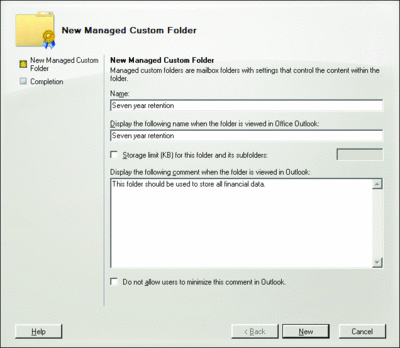
Figure 2** An intuitive wizard makes it easy to create a new managed folder **(Click the image for a larger view)
With a data retention policy in place, you need to provide users with a simple means to sort and store their messages, ensuring that the data is retained in compliance with your organization’s requirements. Imagine you need to deploy three custom folders to your users so that they can identify mail for three, five, or seven years of retention. Once you have created the managed folders, the next step is to apply content settings to each folder. You do this using the Managed Content Settings wizard.
The messaging administrator is in control of setting content expiration (which is measured in days) and the action that should be taken upon the content once it actually expires. There are five actions to choose from:
- Delete and allow recovery
- Mark as past retention limit
- Move to a managed custom folder
- Move to the deleted items folder
- Permanently delete
There are three parameters that you should pay particularly close attention to when configuring these settings. The first is the value for message expiration; since this is calculated in days, you should remember to account for leap years. Corporate management (not to mention a judge) will not appreciate content being deleted earlier than it should be, even if it is by just one day. The second parameter is when the expiration period starts. Typically this is the day the message was delivered to the mailbox, unless you are instructed otherwise by your legal team. The third parameter is the action that is performed once the content has expired. A best practice is to always permanently delete the item. The Content Settings also allow you to journal messages by forwarding them to an SMTP address.
Managed folders are applied to mailboxes using managed folder mailbox policies. The Exchange Management Console provides another wizard for creating these policies. The policies allow you to select and group multiple folders. This lets you link multiple folders to a single policy.
Typically, you would apply the managed folder mailbox policy during mailbox creation. Alternatively, you can use the Exchange Management Shell to apply a policy to an existing mailbox using the Set-Mailbox cmdlet. Say you want to apply a managed folder mailbox policy called retention to an e-mail account with the alias USER1. To do this, you would use the following command:
Set-Mailbox –Identity USER1
–ManagedFolderMailboxPolicy “retention”
Managed folders and the corresponding content settings provide a powerful mechanism for managing the retention and compliance process. Not only does it allow users to sort relevant e-mail and store data in folders that are managed centrally, but it also allows for journaling of these items to ensure that in the event of a discovery request or preservation order, you can easily comply with the court’s request.
Transport Rules
There are two Transport Rules agents in Exchange Server 2007. In terms of compliance, however, you are really only interested in the agent that runs on Hub Transport servers. This agent helps you apply policy-based compliance rules to messages flowing through your Exchange organization. (The Edge Transport Server Rules agent, on the other hand, helps you protect your organization against spam and viruses.)
Some of the common regulatory and compliance requirements administrators are responsible for implementing include:
- Limiting interaction between different groups of senders and recipients
- Preventing inappropriate content from entering or leaving the company
- Filtering confidential information
- Tracking or archiving messages that are sent to and received from specific users and groups
- Redirecting inbound and outbound messages for inspection before delivery
- Applying disclaimers
The Hub Transport server was chosen for this agent due to the role it plays in an Exchange 2007 topology. Changes to the topology in Exchange 2007 are significant and, as a result, Exchange is now much more tightly integrated with the Active Directory® topology. As mail flows through the organization, it will at some point be processed via a Hub Transport server. This Hub Transport server will query Active Directory for the current transport rule configuration and apply the rules to all the messages it handles.
Any transport rule configured on a Hub Transport server will be replicated to all other Hub Transport servers via the Active Directory service. You need to be aware of how your site and topology will impact replication and, in turn, you need to determine how quickly you can deploy an organization-wide rule.
You also need to keep in mind that a Hub Transport server maintains a recipient cache for recipient and distribution list lookup. The refresh interval, which is four hours by default, will affect the timing of rules being applied to your messages.
Transport rules on Hub Transport servers evaluate all meeting requests, regular messages, encrypted messages, and rights-protected messages that are sent between authenticated users. All e-mail messages that are sent anonymously are evaluated, regardless of message type, sender, and recipient.
Each transport rule consists of the following components: conditions, exceptions, and actions. Conditions are used to indicate which message attributes—such as headers, recipients, or senders—are used in the message identification process. Once a message meets all of the conditions for a particular rule, actions are applied unless the message matches a configured exception. Exceptions are optional. If configured, an exception will stop any messages that meet any one of the exception criteria from being processed by the transport rule. Actions, which are a required component for each transport rule, specify how a message should be processed. Figure 3 lists the available actions that can be applied based on transport rules that are configured on a Hub Transport server.
Figure 3 Available actions for transport rules on a Hub server
| Action | Action Name | Description |
| Log an event with message | LogEvent | Adds an event into the Application log of the local computer. |
| Prepend the subject with string | PrependSubject | Prepends a string to the start of the message subject field. |
| Apply message classification | ApplyClassification | Applies a message classification to the message. |
| Append disclaimer text | ApplyDisclaimer | Applies a disclaimer to the message. |
| Set the spam confidence level to value | SetScl | Sets the spam confidence level (SCL) on a message. |
| Set header with value | SetHeader | Creates a new message header field or modifies an existing message header field. |
| Remove header | RemoveHeader | Removes the specified message header field from a message. |
| Add a recipient in the To field addresses | AddToRecipient | Adds one or more recipients to the To address list of the message. The original recipients can see the additional address. |
| Copy message to addresses | CopyTo | Adds one or more recipients to the carbon copy (Cc) field of the message. The original recipients can see the original address. |
| Blind copy the message to addresses | BlindCopyTo | Adds one or more e-mail recipients to the blind carbon copy (Bcc) address list of the e-mail message. |
| Redirect message to addresses | RedirectMessage | Redirects the message to one or more recipients who are specified by the administrator. The message isn’t delivered to the original recipient or recipients, and no notification is sent to the recipients or the sender. |
| Send bounce message to sender with enhanced status code | RejectMessage | Deletes the message and sends a non-delivery receipt to the sender. The recipient doesn’t receive the message or notification. |
| Drop the message silently | DeleteMessage | Deletes the message. Notification is not sent to the recipient or to the sender. |
To create a transport rule, you can use the Exchange Management Console and the Rules Transport wizard, shown in Figure 4. Alternatively, you can use the Exchange Management Shell to script rules creation.
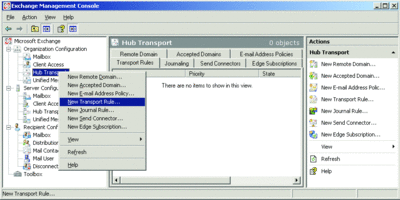
Figure 4** Launch the Rules Transport wizard to configure a transport rule on a Hub Transport server **(Click the image for a larger view)
Note that it’s also possible to use the SDK to write custom transport agents that process messages based on SMTP events within Exchange. This, however, is not for the faint of heart.
Message Classification
The new Message Classification tool uses metadata to describe the intended use or audience of a specific message. On the client-side, this metadata can be used by Outlook® Web Access (OWA) or Outlook 2007 to display a user-readable description of the classification. On the server side, the Transport Rules agents can act upon the message based on its classification.
The default message classifications included with Exchange Server 2007 are A/C (Attorney/Client) Privileged, Attachment Removed, Company Confidential, and Company Internal. However, many organizations will want to create their own classifications. You can create new classifications using the new-MessageClassification cmdlet in the Exchange Management Shell. For example, if you need to restrict access to financial data, you could create a message classification called Financial—Confidential:
new-MessageClassification –Name finance –DisplayName “Financial—Confidential”
-RecipientDescription “This message contains confidential financial data.”
–SenderDescription “Restricts recipients of messages that contain confidential financial data”
Note that while only three parameters are required—Name, DisplayName, and SenderDescription—you should at least add RecipientDescription to achieve a basic level of functionality. Figure 5 shows this new classification now listed in the OWA interface.
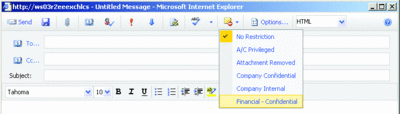
Figure 5** The list of message classifications includes the newly created Financial—Confidential **(Click the image for a larger view)
This command does not use the locale parameter and therefore would apply to all locales within your Exchange organization. If you support global operations, you will probably want to make your custom message classifications locale-specific.
In addition, you should remember to correctly set the permissions on the classifications. By default, all new message classifications are created with read permissions assigned to authenticated users. However, you should segment the message classifications so that users only have access to the message classifications that are appropriate to their roles. Also, note that each classification can have a relative priority to other message classifications. This priority specifies the ordering of descriptions and it determines which classifications are associated with a forwarded or replied message.
Once you have created the necessary classifications, the next step is to create transport rules that use the classifications. (These message classifications, of course, don’t have to be action-related—they can be merely informational.) As Figure 6 illustrates, you have many options when combining message classifications with transport rules. I’ve created a transport rule that monitors for messages classified as Financial. If a message is marked as such, the transport rule agent examines the recipients. If any of the recipients are not a member of the Financial Dept distribution group, the message is returned to the sender with a custom non-delivery message.
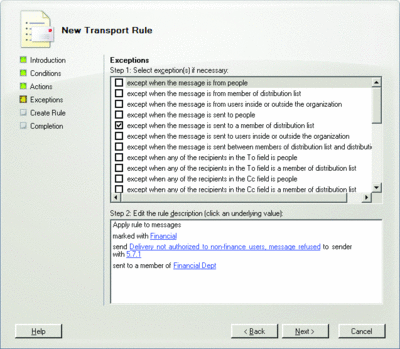
Figure 6** Creating a transport rule for messages classified as Financial **(Click the image for a larger view)
Message classification can also be used to enforce "ethical walls" in your organization. For instance, it is sometimes necessary to restrict communications between certain individuals and departments. Message classification can be used for this purpose.
Journaling Agent
When ensuring compliance, journaling can be a powerful, though sometimes challenging, weapon. Fortunately, Exchange Server 2007 offers much more flexible journaling capabilities. It now supports both standard journaling (at the mailbox database level) and the new premium journaling (per recipient), which enables journaling for individual users and distribution groups. This makes the process for complying with requests—such as holds or court-issued preservation orders—much simpler. In addition, you have more control over the impact journaling will have on storage and performance.
For example, one of the most flexible new options comes in the form of support for journaling based on dynamic distribution groups. Say your organization has an ongoing need to place a hold on the e-mail messages of certain individuals. Perhaps this is for an internal HR investigation or a court case. With a dynamic distribution group, the administrator can add and remove users to an established group that is already being journaled. This provides a quick and easy way to provision ad hoc journaling.
Using the Exchange Management Console and the Dynamic Distribution Group wizard, you have the option to select the user container and, as shown in Figure 7, to filter the included mailboxes based on the value of certain Active Directory attributes. Selecting one of the custom attributes, also shown in Figure 7, allows the administrator to control which users are being journaled by adding or removing this value.
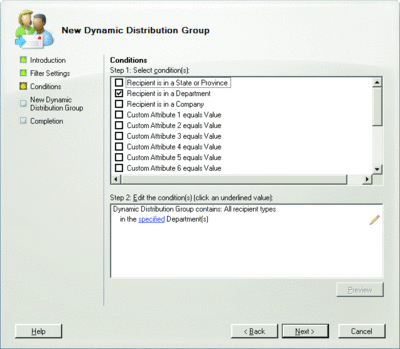
Figure 7** Using the Dynamic Distribution Group wizard to configure journaling rules **(Click the image for a larger view)
For an in-depth look at journaling in Exchange 2007, refer to David Strome’s December 2006 article "More Powerful Journaling in Exchange 2007". You can find additional information in "Overview of Journaling".
Alan Maddison is a Senior Consultant in the Microsoft technology practice of MTI Technology Corporation. His primary focus is on Active Directory, Exchange Server, and virtualization.
© 2008 Microsoft Corporation and CMP Media, LLC. All rights reserved; reproduction in part or in whole without permission is prohibited.