The Cable GuyWireless Group Policy Settings for Windows Vista
Joseph Davies
This column includes prerelease information about Windows Server 2008 that is subject to change.
As an administrator, your job would probably be a bit easier if you could centrally configure and distribute wireless network settings to all the computers in your Active Directory network. Fortunately, Windows supports a special Group Policy extension for Computer Configuration that lets you do just that. It’s
called the Wireless Network (IEEE 802.11) Policies extension, supported by computers running Windows Vista™, Windows® XP, Windows Server® 2003, and Windows Server 2008.
Here’s how it works. Either when joining the domain, or when starting up (and on an ongoing basis after that), these operating systems automatically download the wireless settings in this Group Policy extension and apply them. You can configure wireless policies for a domain-based Group Policy object from the following node in the Group Policy Object Editor snap-in: Computer Configuration | Windows Settings | Security Settings | Wireless Network (IEEE 802.11) Policies.
Figure 1 shows the location of the Wireless Network (IEEE 802.11) Policies node for a Windows Server 2008 domain or for a Windows Server 2003 domain that has had its schema extended with the 802.11Schema.ldf and 802.3Schema.ldf schema extension files (described in microsoft.com/technet/network/wifi/vista_ad_ext.mspx).
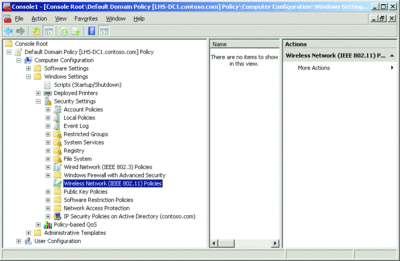
Figure 1** Wireless Network (IEEE 802.11) Policies node **(Click the image for a larger view)
By default, there are no Wireless Network (IEEE 802.11) Policies. To create a new policy, right-click Wireless Network (IEEE 802.11) Policies in the console tree and then click Create A New Windows XP Policy or click Create A New Windows Vista Policy. For each type of policy, you can only create a single policy, but each policy can contain settings for multiple wireless networks.
For the Windows XP policy, the policy settings are very similar to those described in my July 2003 column. However, there are new options for non-broadcast wireless networks, Wi-Fi Protected Access 2 (WPA2) authentication methods, and fast roaming settings for WPA2 authentication. To support these new settings, computers running Windows XP Service Pack 2 (SP2) must install the Wireless Client Update for Windows XP SP2 found at support.microsoft.com/kb/917021. Alternately, you can install Windows XP Service Pack 3.
The Windows Vista wireless policy contains policy settings specific to Windows Vista and Windows Server 2008 wireless clients. If both types of wireless policies are configured, Windows XP wireless clients will only use their own policy settings and the Windows Vista wireless clients will only use their own policy settings. If there are no Windows Vista policy settings, Windows Vista wireless clients will use the Windows XP settings. This article describes the settings that can be configured with the Windows Vista wireless policy.
On the General tab of a Windows Vista wireless network policy, you can configure a name and description for the policy, specify whether the WLAN AutoConfig service is enabled, and configure the list of wireless network profiles and their settings in preferred order (see Figure 2). You can also export a profile as an XML file by selecting the profile and clicking Export. To import an XML file as a wireless profile, click Import and specify the file’s location.
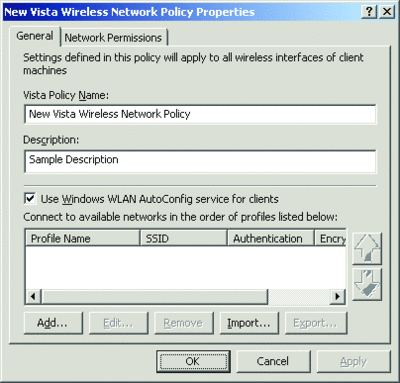
Figure 2** Wireless network policy properties **(Click the image for a larger view)
Figure 3 shows the Network Permissions tab for a Windows Vista wireless network policy with its default settings. This tab is new for Windows Vista and allows you to specify wireless networks by name and either allow or deny access to them. For example, you can create an Allow list containing wireless network names, also known as Service Set Identifiers (SSID), to which a Windows Vista wireless client is allowed to connect. This is useful for network administrators who want an organization’s laptop computers to connect to a specific set of wireless networks, which might include the organization’s wireless network and Internet service providers.
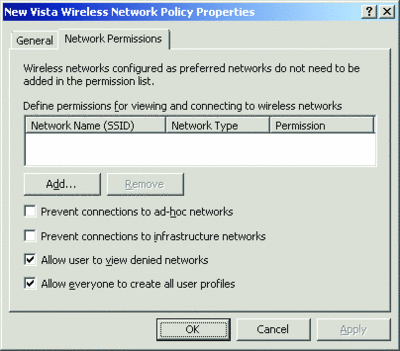
Figure 3** Network Permissions tab **(Click the image for a larger view)
With a deny list, you can specify by name the set of wireless networks to which the wireless client is not allowed to connect. This is useful to prevent managed laptop computers from connecting to other wireless networks that are within range—for example, when an organization occupies a floor of a building and there are other wireless networks of other organizations on adjoining floors. You can also prevent managed laptop computers from connecting to known unsecured wireless networks using a deny list. To create either list or specify individual wireless networks to grant or deny access, click Add to add a wireless network by name and specify whether it is allowed or denied.
On the Network Permissions tab, there are also settings to prevent connections to either ad hoc or infrastructure-mode wireless networks. You can also allow users to view the wireless networks that have been configured as denied and enable any user to create an all-user profile. An all-user profile can be used to connect to a specific wireless network by any user with an account on the computer. If this setting is disabled, only users in the Network Administrators group or Network Operators group can create all-user wireless profiles on the computer.
Wireless Network Profile Properties
To manage a wireless network profile from the General tab of the Windows Vista wireless policy, either select an existing profile and click Edit or click Add and then specify whether the new wireless profile is for an ad hoc or infrastructure-mode wireless network.
To create a new wireless profile, begin on the Connection tab by naming the profile and creating a list of wireless network names to which it applies (see Figure 4). You can add new names by typing the name in Network Name(s) (SSID) and clicking Add. You can also specify whether the wireless client using this profile will automatically attempt to connect to the wireless networks named in the profile when in range (subject to the preference order of the list of wireless profiles on the General tab for the Windows Vista policy). Additionally, you can indicate whether to automatically disconnect from this wireless network if a more preferred wireless network comes within range, and indicate that the wireless networks in this profile are non-broadcast networks (also known as hidden networks).
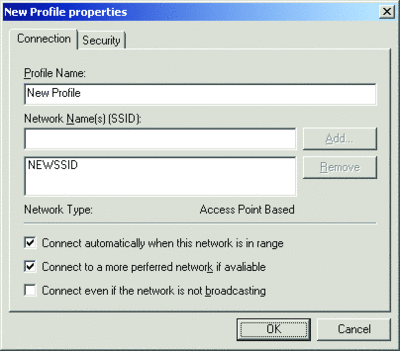
Figure 4** Connection tab **(Click the image for a larger view)
From the Security tab, shown in Figure 5, you can configure the authentication and encryption methods for the wireless networks in the profile. The choice of encryption methods depends on your choice of authentication method. The choices for each are listed in Figure 6.
Figure 6 Security methods
| Authentication Methods |
| Open |
| Shared |
| Wi-Fi Protected Access (WPA)-Personal |
| WPA-Enterprise |
| WPA2-Personal |
| WPA2-Enterprise |
| Open with 802.1X |
| Encryption Methods |
| Wired Equivalent Privacy (WEP) |
| Temporal Key Integrity Protocol (TKIP) |
| Advanced Encryption Standard (AES) |
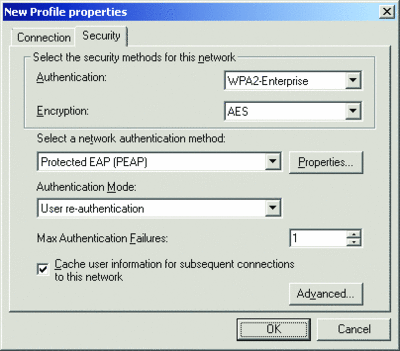
Figure 5** Security tab **(Click the image for a larger view)
If you decide to select WPA-Enterprise, WPA2-Enterprise, or Open with 802.1X as the authentication method, you can also configure the network authentication method (the Extensible Authentication Protocol [EAP] type), the authentication mode (user re-authentication, computer authentication, user authentication, or guest authentication), the number of times authentication attempts can fail before authentication is abandoned, and whether to cache user information for subsequent connections. This last setting specifies that when the user logs off, the user credential data is removed from the registry. So, when the next user logs on, he will be prompted for his credentials (such as user name and password).
To configure advanced security settings for the WPA-Enterprise, WPA2-Enterprise, or Open with 802.1X authentication methods, click Advanced. Figure 7 shows the default Advanced security settings dialog box.
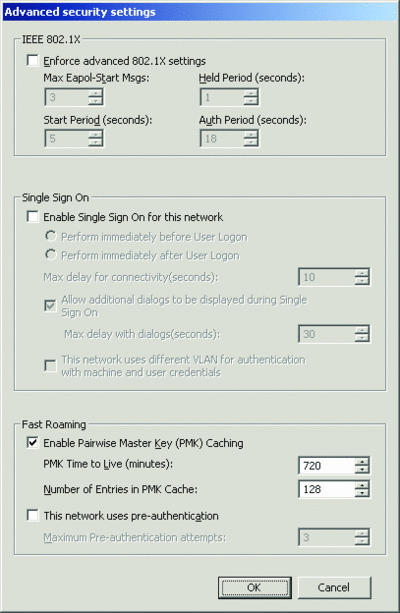
Figure 7** Advanced security settings dialog box **(Click the image for a larger view)
In the IEEE 802.1X section, you can specify the number of successive EAP over LAN (EAPOL)-Start messages that are sent out when no response to the initial EAPOL-Start messages is received, and the time interval between the retransmission of EAPOL-Start messages when no response to the previously sent EAPOL-Start message is received. You can also set the period for which the authenticating client will not perform any 802.1X authentication activity after it has received an authentication failure indication from the authenticator, and the interval for which the authenticating client will wait before retransmitting any 802.1X requests after end-to-end 802.1X authentication has been initiated.
Single sign-on (SSO) allows you to configure when 802.1X authentication occurs relative to the user logon and to integrate user logon and 802.1X authentication credentials on the Windows logon server. In the SSO section, there are settings to perform wireless authentication immediately before or after the user logon process and to specify the number of seconds of delay for connectivity before the process begins. You can also indicate whether to prompt the user for additional input fields if the authentication method requires the user to type additional credentials and how long to display those fields, and whether the wireless networks for this profile use a different virtual LAN (VLAN) for computer or user authentication.
In the Fast Roaming section, you can configure Pairwise Master Key (PMK) caching and preauthentication options. The Fast Roaming section only appears when you select WPA2-Enterprise as the authentication method. With PMK caching, wireless clients and wireless access points (APs) cache the results of 802.1X authentications. Therefore, access is much faster when a wireless client roams back to a wireless AP to which the client already authenticated. You can configure a maximum time to keep an entry in the PMK cache and the maximum number of entries. With preauthentication, a wireless client can perform an 802.1X authentication with other wireless APs in its range while it is still connected to its current wireless AP. If the wireless client roams to a wireless AP with which it has preauthenticated, access time is substantially decreased. You can configure the maximum number of times to attempt preauthentication with a wireless AP.
A final check box allows you to specify whether to perform AES encryption in a Federal Information Processing Standard (FIPS) 140-2 certified mode. FIPS 140-2 is a U.S. government computer security standard that specifies design and implementation requirements for cryptographic modules. Windows Server 2008 and Windows Vista are FIPS 140-2 certified. When you enable FIPS 140-2 certified mode, Windows Server 2008 or Windows Vista will perform the AES encryption in software, rather than relying on the wireless network adapter. This check box only appears when you select WPA2-Enterprise as the authentication method on the Security tab.
For more information about wireless support in Windows, see microsoft.com/wifi. For more information about Windows Group Policy, see the resources at microsoft.com/gp.
Joseph Davies is a technical writer with Microsoft and has been teaching and writing about Windows networking topics since 1992. He has written eight books for Microsoft Press and is the author of the monthly TechNet Cable Guy column.
© 2008 Microsoft Corporation and CMP Media, LLC. All rights reserved; reproduction in part or in whole without permission is prohibited.