Security WatchMalware Inspection at the Perimeter
Yuri Diogenes, Mohit Saxena, and Jim Harrison
Contents
How Malware Inspection Works
Configuring TMG Malware Inspection Feature
Setting Policy for Web Access
Update Center
Testing and Monitoring
Conclusion
The new Microsoft Forefront Threat Management Gateway Medium Business Edition (TMG MBE), available as part of Essential Business Server and as a standalone product, provides significant improvements for the Microsoft Firewall service operation. One of the most important features of this new firewall is the capability to inspect HTTP traffic that crosses it for malware. By using this new feature, you will be able to:
- Improve your ability to protect your internal network against malware coming from the Internet.
- Keep the perimeter updated with the latest malware signatures by using TMG Update Center.
- Keep an eye on suspicious traffic via real-time monitoring of log entries and get post-mortem malware statistics using the new set of reports.
This approach lets you mitigate potential threats in HTTP traffic crossing the perimeter, adding a new layer of security to your anti-malware solution. The need for client and server antivirus is not eliminated, but because this inspection is performed before the client workstation receives the data, the malware threat is greatly minimized.
This is especially useful if you have unmanaged computers on your network, such as guest computers. With Forefront TMG, you ensure that if those computers try to download a suspicious file, the file will be blocked even if the unmanaged computer is not running antivirus software.
How Malware Inspection Works
When a user accesses a Web site and tries to download a file, TMG will intercept that traffic and check whether or not the rule that allows that user to access the target site has the malware inspection feature enabled on it. If it does, TMG will start the inspection. (Obviously, if this feature is not enabled, TMG will not scan the traffic.) Figure 1 summarizes the basic flow of the malware inspection as the client is downloading a file:
- Client sends an HTTP request to the target Web site to download a file.
- Forefront TMG receives the request, determines whether or not any rule matches and, if this rule has malware inspection enabled, scans the request for malware.
- If the request is valid and clean, Forefront TMG then sends the request to the destination server.
- The destination server receives the request and responds accordingly.
- Forefront TMG receives the response from the destination server and processes it first through the proxy engine.
- If the rule specifies malware inspection, the proxy engine sends the body of the HTTP request to the Malware Inspection Filter. Responses smaller than 64KB are accumulated in memory. (Based on the Internet statistics, approximately 98% of downloads are smaller than 64KB and can be scanned without disk I/O.) The Malware Inspection Filter accumulates the content, timing the download and inspection, then returns the control to the proxy engine.
- If the content is allowed, Forefront TMG sends the original file to the user. If the file is infected and TMG cannot clean the file, TMG sends an HTML page to the user saying that the content was blocked.

Figure 1 Malware inspection flow
During the accumulation (Step 6), TMG improves the user experience using one of the following content delivery methods:
- HTML progress page, which shows dynamic progress indication and allows the user to download the content from the TMG machine when scanning completes.
- Standard trickling, in which Forefront TMG initially sends the content at a very slow rate to the client and then, when the scanning is complete, sends the data at the highest possible rate.
- Fast trickling, in which the parameter you define is a number indicating the trade-off between the user experience (less buffering on Forefront TMG and more scans) and performance (more buffering on Forefront TMG and less scans). This is usually used for media files played by online players (not for media streaming).
To maintain the standards found in other Microsoft security solutions, the malware protection feature in TMG takes advantage of the same Malware Protection Engine (MPE) that is used in Forefront Client Security, Windows Defender, and One Care. Later in this column, we will demonstrate how to keep the definitions up-to-date using Update Center.
Configuring TMG Malware Inspection Feature
To configure malware inspection, you need to enable it first at a global level and then also at the rule level. The first step is to go to the Web Access Policy node and click on Configure Malware Inspection on the Tasks pane, as shown in Figure 2.
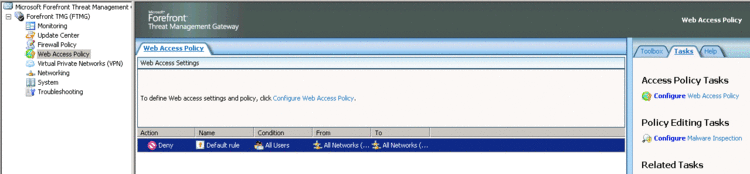
Figure 2 Web access settings
When you do, a dialog box appears that lets you enable malware inspection globally, as shown in Figure 3. This dialog box also contains other settings for malware inspection that are pre-populated with default settings. Some of these settings can be controlled at the access rule level while some can only be set globally.
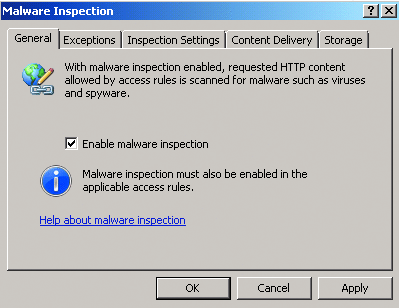
Figure 3 Configuring malware inspection at the global level
The Exceptions tab in Figure 4 allows you to control which sites will be exempted from malware inspection. You can also do this through policy settings, but configuration using this dialog overrides any access rule: if the site is listed here, it will not be inspected for malware even if defined for inspection at the rule level. Such global settings are useful for Web sites hosted by organizations in their DMZ for their internal users or for any other trusted, frequently used site.
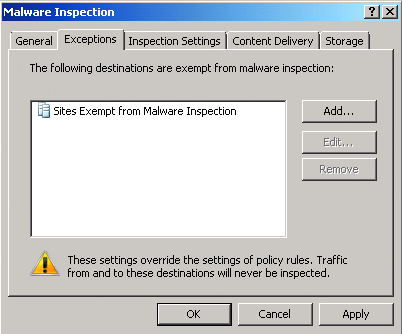
Figure 4 Site exceptions
The Inspection Settings tab shown in Figure 5 lets you specify what kind of content will be blocked. You can define the default action for this type of content, such as whether Forefront TMG should attempt to clean infected content and then send it to the end user or whether the content will be completely blocked with no attempt to clean it.
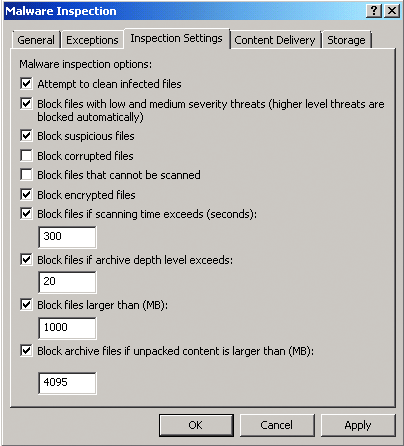
Figure 5 Setting inspection parameters
You can also choose to block suspicious, corrupted, or encrypted files or files that cannot be scanned. And you can set file size limits to preserve bandwidth and prevent users from downloading large files or files that take too long for inspection. Note that these are global settings and are not exposed in the rule.
The Content Delivery tab, shown in Figure 6, allows you to configure the user experience during file download, including specifying whether an end user will receive a trickled response or a progress notification page for files that take longer than 10 seconds (configurable in COM) to download and scan. (No notification occurs if the process takes 10 seconds or less.)
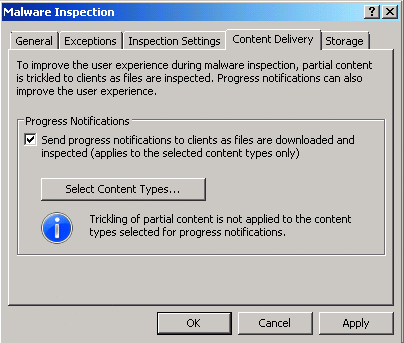
Figure 6 Specifying how content is delivered
You can also select what type of content will receive a progress notification as opposed to a trickled response by clicking on Select Content Types and adding or removing content types from that dialog box. This is a global setting and is not exposed in the rule.
The Storage tab defines the folder where the files will be temporarily accumulated while being scanned and served to the end user. The default folder is the %SystemRoot%\Temp, but this can be changed. Again, this is a global setting and is not exposed in the rule.
Forefront TMG malware inspection performance for content that must be accumulated to disk will improve when this folder is located on a different spindle than the drives used for OS paging or Forefront TMG logging. It is important to exclude this folder from being scanned if you have antivirus software on the TMG Server so that the files are not locked for scanning by the antivirus software while in use by Forefront TMG Server. For best practices on what folders to exclude, please refer to "Considerations When Using Antivirus Software on ISA Server."
Setting Policy for Web Access
The Forefront TMG administrator can configure rules controlling user access to the Internet via either the Web Access Policy or the Firewall Policy. When using the Web Access Policy, the rules explicitly allow only the HTTP and HTTPS protocols, and they let administrators allow or deny user access to Web sites. This can also be achieved through Access Rule under the Firewall Policy, where you can manually allow HTTP and HTTPS access based on source, destination, and user. Note that in an Access Rule, the Malware Inspection option is visible only if the selected protocols include the Web protocols.
To enable malware inspection at the rule level, you can check the box "Inspect content downloaded from Web servers to clients," which you will find on the Web Access Default Rule Properties dialog. Be aware that this inspection applies only to HTTP content that is downloaded by the rule. Malware inspection needs to be enabled globally first before it can be applied at the rule level.
Update Center
Forefront TMG maintains the definitions of known viruses, worms, and other malware. To keep these important definitions up-to-date, Forefront TMG has built in a centralized mechanism called the Update Center that allows the administrator to configure the update frequency as well as the automatic update action. The Update Center can be accessed from the Forefront TMG console.
The Definition Updates panel shows the status of the last update and the time when the last check for new updates was performed. The Tasks pane on the right side is where you can configure update parameters. Figure 7 shows the various options for definition updates that can be accessed by clicking on Configure Update Settings in the Tasks pane.
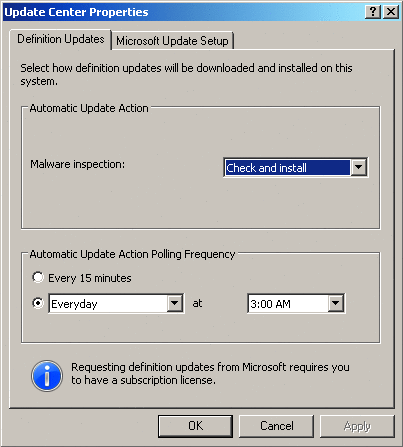
Figure 7 Definitions update window
By default, Forefront TMG uses the Automatic Updates agent to pull updates from the Microsoft Update service in order to refresh the antimalware definitions. The update agent uses the machine's default update server selection; therefore, if the machine uses updates from Windows Server Update Services (WSUS), the agent will also get updates from WSUS, otherwise it will get them directly from Microsoft Update. These transactions are recorded in the %systemroot%\windowsupdate.log file (as are the regular Windows Updates).
The frequency settings in the Forefront TMG Update Center do not override the Windows Update settings. These settings are completely separate; therefore, Windows downloads software updates while Forefront TMG only downloads signatures.
You can force Forefront TMG to look for updates by clicking on Check for Updates in the Task pane. If new updates are detected and installed, an informational alert will appear in the Alerts tab, as shown in Figure 8. As you can see, the bottom part of the window shows details about the update as well as the versions of the files that were updated.
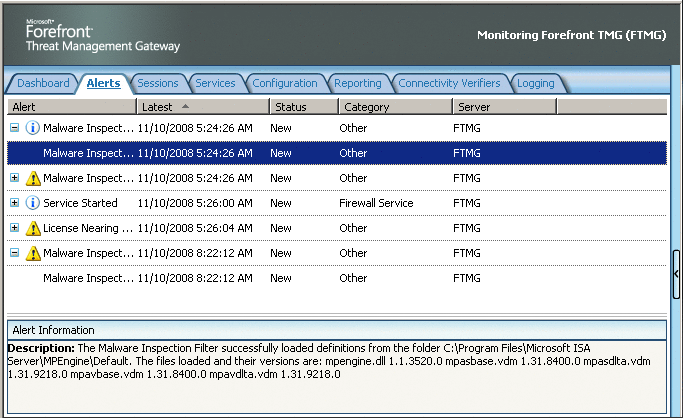
Figure 8 Malware Inspection Filter alert
Testing and Monitoring
After configuring the inspection and Update Center settings, the next step is to test the functionality. Let's assume that you have a client workstation that accesses the Internet through Forefront TMG and wants to download a file from a Web site. The first step, before the file download starts, is to configure the monitoring in Forefront TMG by filtering the IP address of the client workstation that is trying to access the external resource, as show in Figure 9.
Figure 9 Monitoring the client workstation that is trying to download a file
For this example, suppose the client is sending a HTTP GET to files.fabrikam.com/suspicious.exe. Then Forefront TMG evaluates the request, and after detecting that the file in the request is suspicious, it writes a Failed Connection Attempt event to the log (see Figure 10).
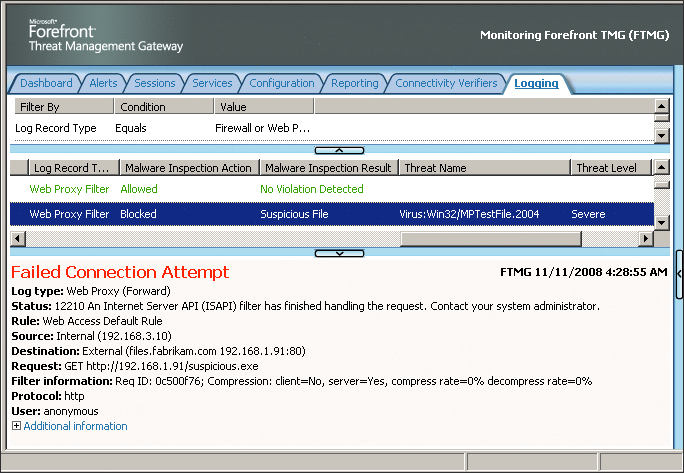
Figure 10 Suspicious file detected
Notice that in the Malware Inspection Result column, this file is categorized as suspicious; the Threat Name column indicates the malware name, and the Threat Level is severe. The details pane for the error shows more information about why the connection attempt failed.
The user who was trying to download this file also experiences this error but receives a more descriptive and friendly message explaining that "access to suspicious files is blocked due to security policy settings" (as shown in Figure 11). This approach allows the user to understand what is happening and why the file he is trying to access was not available.
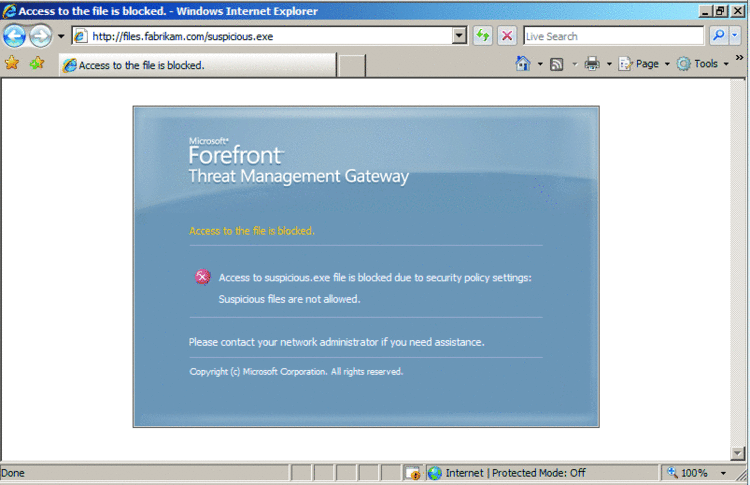
Figure 11 A more user-friendly error message
Conclusion
Our main goal in this column was to explain how using the malware inspection feature of the Microsoft Forefront TMG can improve edge security. This feature gives you a centralized view of any suspicious traffic that potentially crosses your firewall and allows you to take actions based on the results of the inspection. While this is an important approach toward a more secure environment, there are always concerns about how this may impact the user experience while browsing the Web.
The Microsoft Forefront TMG also addresses these concerns in such a way that the scan process can be more transparent to the end user. For more information, review the Forefront TMG Documentation at the Microsoft Forefront Edge Security TechCenter.
Yuri Diogenes (MCSE+S, MCTS, MCITP, Security+, Network+, CCNP) works for Microsoft as Security Support Engineer on the ISA Server/IAG Team. He also writes articles for ISA Server Team Blog and TechNet Magazine. Yuri is a co-author of the Forefront Community Page called "Tales from the Edge."
Mohit Saxena is the Technical Lead for Microsoft ISA Server Support Team. He leads a team of Support Engineers and Escalation Engineers to provide support for customers on break fix issues, bugs, and design change requests.
Jim Harrison joined the ISA Server Sustained Engineering team as a QFE tester in January 2003. He is now an avid ISA server supporter and systems implementer and the co-author of the Forefront Community Page called "Tales from the Edge."
Yuri, Mohit, and Jim are writing the next Microsoft Press book about Microsoft Forefront Threat Management Gateway (TMG); the book will be available in 2009.