ToolboxNew Products for IT Pros
Greg Steen
The opinions expressed in this column are solely those of the author and do not necessarily reflect the opinions of Microsoft. All prices were confirmed at the time of writing, and are subject to change.
Audit Tool
ObserveIT Express
observeit-sys.com/ObserveIT-Express.asp
Having an easy-to-access, searchable, and visual audit tool can be an invaluable asset for troubleshooting, compliance, and audit protection as well as provide both a deterrent for system abuse and some proof for prosecution if the need arise. One such offering is ObserveIT Express from ObserveIT Ltd., which describes its solution as a "people-audit" tool.
ObserveIT Express is the free edition of the company's flagship product. It allows you to record and replay the past 24 hours of user sessions and monitor up to five servers. You can monitor any Windows NT, 2000, 2003 or XP system with ObserveIT, but at this writing, it's not yet available for Windows Vista. You'll need to enable mixed-mode authentication on your SQL server where the ObserveIT data and configuration information is stored.
Once you have the central application server on your host and agents installed on the servers you want to monitor, you simply connect to the Web console to view the recorded sessions and events on the monitored servers. All the data from the sessions is compressed and secured on the backend SQL Server database. The Web console UI is a tabbed interface with Server Diary, User Diary, Search, Reports, and Configuration Settings views.
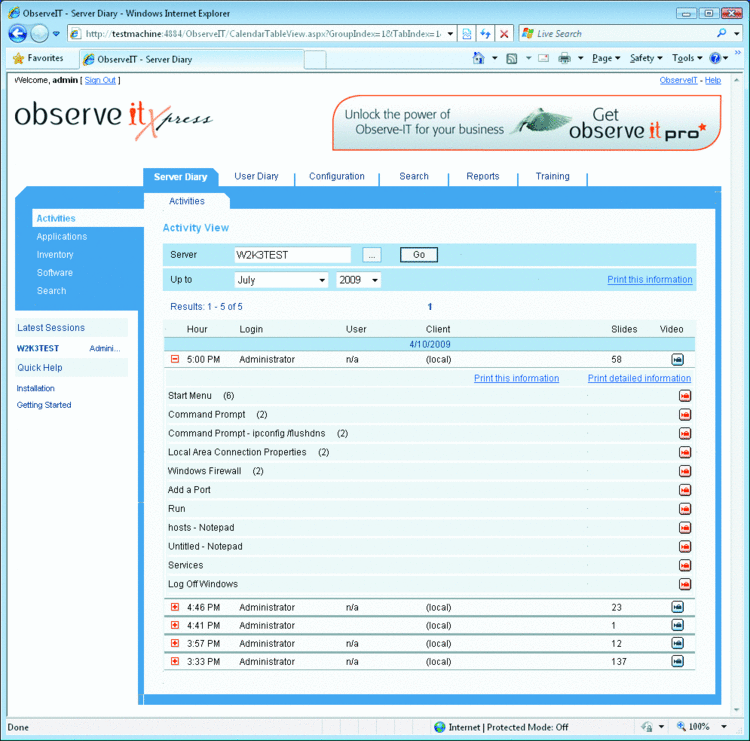
The Server Diary view lets you pick a monitored server and shows you a chronological view of the sessions on that machine, including information on users and session durations and links to slideshow video of the actual session. You'll see exactly what each user did in each session, including details on actions taken, such as commands run from a command prompt, services that were restarted or programs that were launched.
The User Diary view shows you a similar view by user account, regardless of which machines individual users connected to. If you're concerned about a particular action that was executed, you can go to the Search view and type in keywords such as "iisreset" or "command prompt;" the tool will bring back all sessions that included that particular action type. The Reports view groups by application, displaying statistics on particular application events. The Configuration view lets you tweak the installation to your needs, although with the free edition you can't change much. If you want more than the defaults, you'll need to upgrade to the product's full version.
So if you're looking for a quick solution for auditing your Windows sessions, you may want to consider adding ObserveIT Express to your IT toolbox.
If you need more than 24 hours' worth of replay, want to tie the product into your current auditing or monitoring tools such as Microsoft System Center Operations Manager, want to configure which applications and what users should be monitored, or need real-time alerting of user action, consider upgrading to the ObserveIT Pro edition, which starts at $500 per agent plus $5,000 for a perpetual license to the management console and Web front end for your environment.
Price: Basic version, free; Pro edition, $500 per agent plus $5,000 for perpetual license.
ObserveIT Express
Information Tracking
Mouse Tracks 2009 Enterprise Edition
gritware.com/Help_Desk_Software.aspx
Tracking information is among the key operational activities of the systems engineer. Whether you are working on the NOC or on the help desk or are the "IT guy," you probably use, or have the need for, an inventory- and asset-management system and a help-desk ticketing system. And the larger your organization grows, the more critical those systems become to ensuring a smooth workflow and happy end users. One easy-to-use and relatively low-cost option for your environment is Gritware LLC's Mouse Tracks 2009 Enterprise Edition.
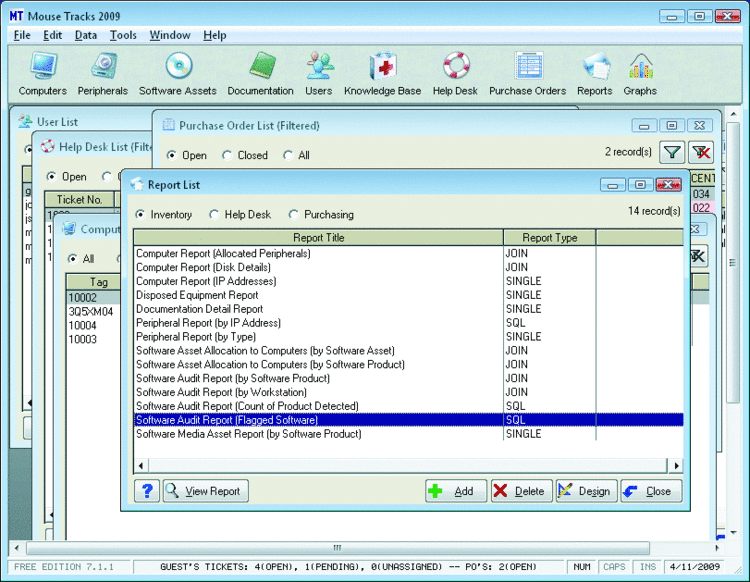
The application is split into a simple and logically laid out WinForm front-end application with either a SQL server or Access database as the data repository. At its heart, the application is a data-entry and reporting application, and the top section of the UI has a row of buttons for each of the different features. Each of the different views allows you to add, edit, delete, import, and duplicate the records for that section. You can also filter the view to isolate the rows that most interest you.
The Computers button takes you to the Computers List view, which provides an overview of the machines that you've added to the system, including asset tags, locations, computer names, operating systems, and when each machine was last audited. From here, you can launch the Audit Wizard, which reaches out to your domain via LDAP query (or simple host name) to pull the machine information such as CPU, network, BIOS, software, peripherals, and video information into the repository.
The Peripherals and Software buttons will show you any imported or added peripherals and software, again with asset tags as you have them assigned and with other pertinent details. That allows you to quickly look up who has what where in your environment. The Software Asset list also groups your different software packages by licenses, so you can see whether your purchased license count matches your actual license count. In addition to the standard data add/remove/update functions, the application's Users view also lets you directly import your user base from Active Directory. From here, you can also select which users have access to the Mouse Tracks software.
If you need to keep track of books as assets, the Documentation view lets you assign asset tags, descriptions, locations, and other details to help you accomplish that task—and "check out" books or documents to users. And the Purchase Orders view lets you manage vendor contacts and create purchase orders, including terms, messages, and shipping information. It also allows you to mark individual items on each P.O. as received so that you know when items arrived for later auditing. In addition to asset management, Mouse Tracks also offers a set of tools for your help-desk functions, including a Knowledge Base and Help-Desk Ticketing system.
The Knowledge Base is searchable and organized by type so you can find a solution while you're talking with a customer. The Help Desk function lets you assign tickets to technicians and track the time needed to resolve each issue. In addition, the Help Desk view lets you define custom fields so that you can keep track of any extra details you may need.
Finally, the Graphs and Reports views let you "pretty up" and aggregate the data you have in your Mouse Tracks system for auditing and presentation (for instance, for when you're putting together license requests or next year's budget). You can even design and create your own graphs and reports to customize the views as needed, using templates or even custom SQL to get the data you need to do so.
Mouse Tracks 2009 Enterprise Edition starts at $795 for a three-user license. But for smaller environments, you might want to consider the slightly limited Standard Edition, which supports up to 15 named users—it starts at $345 for one named user. And if it is just you running the environment, you may even be able to get by with the free edition, which is limited to one user and 20 audited computers. Both the standard and the free editions are also restricted to an Access database backend. Volume discounts and free trials are also available.
Price: Starts at $795 for a three-user license.
MouseTracks 2009 Enterprise Edition
Book Review
Windows Server 2008 Security Resource Kit
microsoft.com/learning/en/us/Books/11841.aspx
Many new security features and best-practice rules of thumb have been introduced with the Windows Server 2008 family of products. Jesper M. Johansson's Windows Server 2008 Security Resource Kit is designed to help you get up to speed on these new features and security in general. Written with numerous contributing Microsoft Most Valuable Professional (MVPs) and the Microsoft Security Team, the book is part of the familiar Resource Kit series from Microsoft Press.
The book is split into three well-defined sections: Part I, Windows Security Fundamentals; Part II, Implementing Identity and Access (IDA) Control Using Active Directory; and Part III, Common Security Scenarios. The book's structure allows you to either read it end to end for an overall understanding or access individual chapters directly—though, as you would expect, the later chapters build on the fundamentals of the first part of the book.
The book's first part starts on the ground floor of Windows security, covering how "objects" are protected from the various "subjects" via authentication and authorization as well as audited to provide as history of actions. You'll then cover the nuts and bolts of those authentication and authorization protocols in the Windows world, including NTLM, Kerberos, password hashing, and password cracking.
Next, you'll learn about protecting objects with the various tools available in the OS while also covering user rights, ACLs, and the Security Descriptor Definition Language. The next chapter dives into the sometimes dreaded, but protective, User Account Control (UAC), offering best practices and describing how it works "under the covers." Then you'll address remote access to resources and how to secure objects with Network Access Protection (NAP) and the Windows Firewall with Advanced Security and, in doing so, IPSec and the Routing and Remote Access Services (RRAS).
Services are at the heart of any operating system, and the next chapter will teach you about safeguarding this significant attack surface on your machines by learning how they can be attacked and how you can protect against such attacks through service "hardening" and security. Arguably one of the most powerful features of Windows security, Group Policy can be an incredibly potent way to fine-tune and protect en masse in your environment, and the book's chapter on that subject will help you learn how to do just that.
Then, wrapping up Part I, you'll learn how to create and observe the different audit trails at your disposal with Windows Server 2008 so that you can see exactly who did what when.
Part II delves into IDA with two in-depth chapters. The first covers the new user interface to Active Directory Domain Services (AD DS), the importance of Read-Only Domain Controllers (RODC), and AD DS auditing. The second chapter covers what's new with Windows Server 2008 PKI and certificate services in general in the new server OS.
Part III jumps into the real-world practicality of all you've learned in the previous chapters, applying the security features and techniques through common security scenarios. In this section's six chapters, you'll learn how to secure the different types of server roles now that the "install all by default" has been reversed in the Windows server system. You'll also see different techniques for managing server updates across your environments and learn how to identify and mitigate the various security dependencies in your infrastructure. The use of branch offices is still growing in many companies, and the next chapter shows you the new features and techniques to help you protect those remote locations. The final two chapters address small-business concerns and the basics of application security.
The book comes with a great companion CD that contains a set of management scripts and utilities and a bonus chapter entitled "Implementing Active Directory Rights Management Services." If you're looking to get up to speed on the enhancements and features found in the latest Windows Server operating system, take a look at the Windows Server 2008 Security Resource Kit.
Space Saver
Duplicate File Remover
Typical shared folders and network storage tend to lend themselves to have multiple copies of the same documents, photos, ISOs, and executables. If you're concerned about space and would like to consolidate those files by removing all those unneeded duplicates, there are many tools out there to help you do so. But how do you ensure that that those extra files are truly duplicates? Going by file names alone would, of course, lead to some angry end users. One tool out there to help you safely clean up all those duplicates is the Duplicate File Remover from Object Rescue.
At launch (after you stop giggling at the application's mascot of a sheep armed with a bazooka), you define your search. The utility lets you pick what types of files you're concerned with—documents, photos, music, video—or you can define your own search based upon file type, size, creation date, and folder exclusions. Note that you can also opt to avoid hidden and system files.
Then, you pick the drive, folder, or network share you wish to search, and Duplicate File Remover builds a list from the selected search areas to determine which files are duplicates. Another plus: the utility will also report on which files it wasn't able to access due to security or other exclusion reasons.
Once that process is complete the application scans the files based on the selected metrics and sorts them into groups, setting one as the primary file and marking the rest as duplicates. Depending upon what action you want to take with the results, you can also use the quick toggle buttons at the top of the user interface to check all duplicates, check or uncheck a selected group, or uncheck all the items before you start.
Then you can delete marked files, copy them, or move them to another location (great for verification, in case a file was incorrectly identified as a duplicate). Or you can create a hard link from the original to the duplicates if you need to maintain the folder/file structure but want to gain back the disk space (and ensure that there's only one file to update and manage).
At the bottom of the UI, the utility also gives you overview statistics such as the total number of files, the number of duplicates found, and the space those duplicates take up on your drive. Finally, when you're done, you can generate an HTML report as an audit trail of what actions you took.
Price: $29.95 for a single user license.
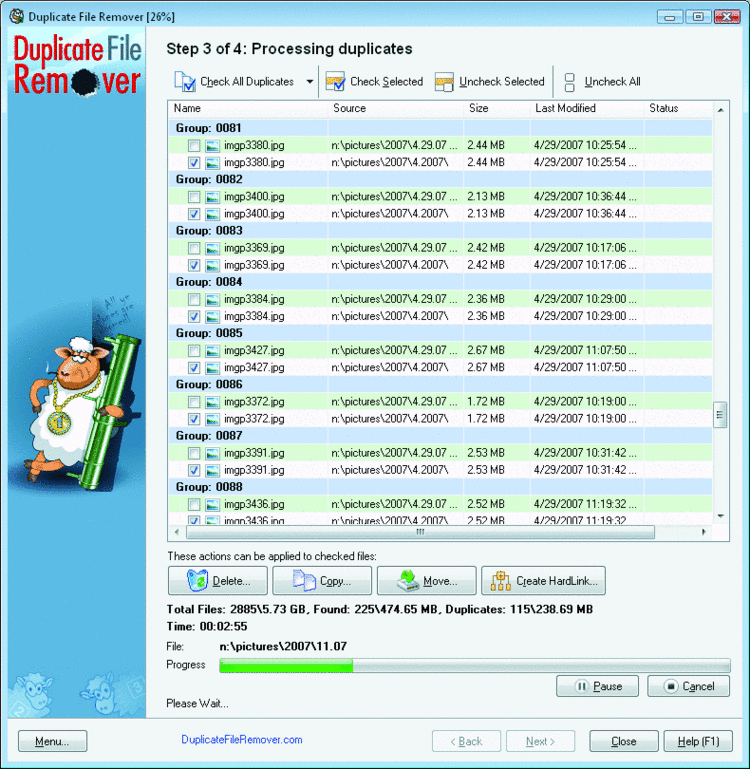
Figure 3 Duplicate File Remover
If you have a favorite tool or utility you would like to see featured here, please write to the author at tntools@microsoft.com.
Greg Steen is a technology professional, entrepreneur, and enthusiast. He is always on the hunt for new tools to help make operations, QA, and development easier for the IT professional.