Front Door Premium with VM and Private Link service
This template deploys a Front Door Standard/Premium with a virtual machine web server origin. Front Door uses a private endpoint, configured with Private Link service, to access the web application.
Sample overview and deployed resources
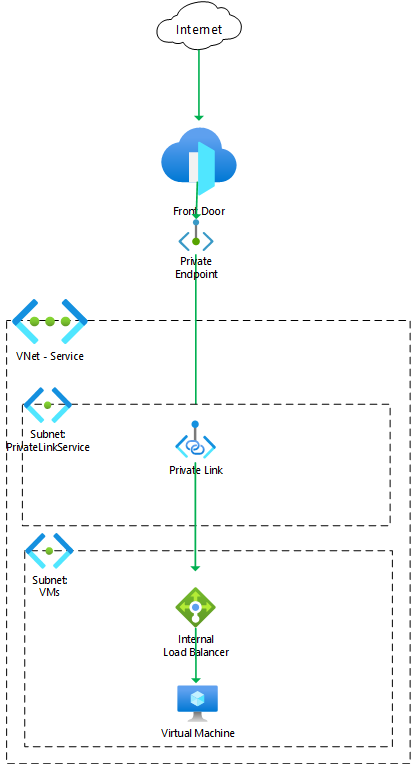
This sample template creates a virtual machine (VM), Private Link service, and a Front Door profile, and uses a private endpoint to access the VM-hosted web app.
The following resources are deployed as part of the solution:
Networking
- Virtual network, with subnets for the VMs and internal load balancer (
VMs) and for Private Link service (PrivateLinkService). - Internal load balancer to sit in front of the VM.
- Private Link service to make the load balancer accessible to Front Door through a private endpoint.
Compute
- Virtual machine, added to the load balancer.
- Virtual machine extension to deploy and enable IIS.
Front Door Standard/Premium
- Front Door profile, endpoint, origin group, origin, and route to direct traffic to the VM.
- This sample must be deployed using the premium Front Door SKU, since this is required for Private Link integration.
The following diagram illustrates the components of this sample.
Deployment steps
You can click the "deploy to Azure" button at the beginning of this document or follow the instructions for command line deployment using the scripts in the root of this repo.
Usage
Connect
Once you have deployed the Azure Resource Manager template, you need to approve the private endpoint connection. This step is necessary because the private endpoint created by Front Door is deployed into a Microsoft-owned Azure subscription, and cross-subscription private endpoint connections require explicit approval. To approve the private endpoint:
- Open the Azure portal and navigate to the Private Link service deployed as part of this sample.
- Click the Private endpoint connections tab.
- Select the private endpoint that is awaiting approval, and click the Approve button. This can take a couple of minutes to complete.
After approving the private endpoint, wait a few minutes before you attempt to access your Front Door endpoint to allow time for Front Door to propagate the settings throughout its network.
You can then access the application through the Front Door endpoint. The application's hostname is emitted as an output from the deployment - the output is named frontDoorEndpointHostName. You should see the default IIS welcome page. If you see an error page, wait a few minutes and try again.
You cannot access the VM directly because it is not exposed to the internet.
Notes
- In this sample, HTTPS connections terminate at Front Door, and connections from Front Door through to the virtual machine are made using HTTP.
- In this sample, the
Hostheader of requests from Front Door will be the hostname of the Front Door endpoint. With a default website on IIS this works successfully since theHostheader is effectively ignored. In more complex scenarios you may need to send specificHostheader values based on what the web server expects or understands.
Tags: Microsoft.Resources/deployments, Microsoft.Network/virtualNetworks, Microsoft.Network/loadBalancers, Microsoft.Compute/virtualMachines/extensions, CustomScriptExtension, Microsoft.Network/networkInterfaces, Microsoft.Compute/virtualMachines, Microsoft.Network/privateLinkServices, Microsoft.Cdn/profiles, Microsoft.Cdn/profiles/afdEndpoints, Microsoft.Cdn/profiles/originGroups, Microsoft.Cdn/profiles/originGroups/origins, Microsoft.Cdn/profiles/afdEndpoints/routes

