Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Overview
By default in Microsoft 365, any member user in Microsoft Entra ID can use common tools to connect to the tenant and view/download user details and directory information. This article explains how to block several common tools that might be used for this purpose.
Blocking PowerShell
To block the PowerShell App ID, follow the instructions:
Block PowerShell for everyone except me
This script blocks PowerShell for everyone in the tenant, except the person running the script. Use with caution to ensure you don't block users (for example, IT admins) who will need access.
Download the PowerShell script located here and save in c:\temp
Launch PowerShell and run the cmd:
Set-Location c:\temp
Type the cmd and press enter
.\Block-PowerShell_for_everyone_except_me.ps1
If attempting to authenticate using the Azure AD v2 PowerShell module, they receive an error similar to what’s shown:

Block PowerShell for everyone except a list of admins
This script blocks PowerShell for everyone in the tenant, except for a list of users specified in the CSV file. Double check your list is correct.
Download the PowerShell script located here and the sample CSV file located here, and save both in c:\temp
Open the CSV and update the UserPrincipalName list with every admin that requires PowerShell access. Once updated, save and close the CSV file.
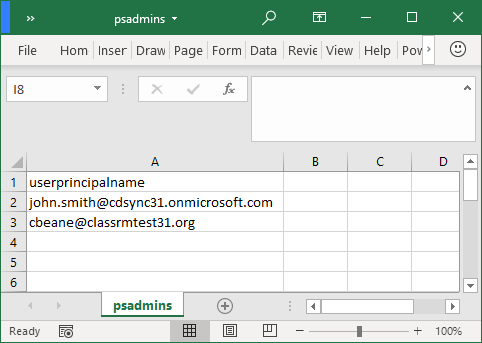
Launch PowerShell and run the cmd:
Set-Location c:\temp
Type the cmd and press enter.
.\Block-PowerShell_for_everyone_except_a_list_of_admins.ps1
Block Microsoft Graph PowerShell for everyone except me
This script blocks the Microsoft Graph PowerShell module for everyone in the tenant, except the person running the script. Use with caution.
Download the PowerShell script located here and save in c:\temp
Launch PowerShell and run the cmd:
Set-Location c:\temp
Type the cmd and press enter
.\Block-PowerShell_for_everyone_except_me.ps1
If anyone attempting to authenticate using the MS Graph PowerShell module, they receive an error similar to:
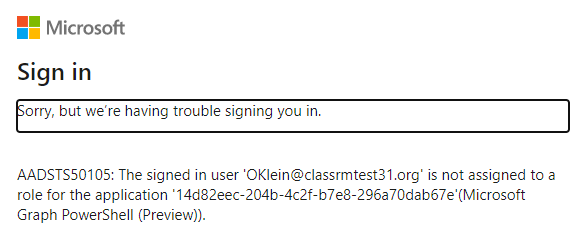
Block Microsoft Graph PowerShell for Everyone except a list of users
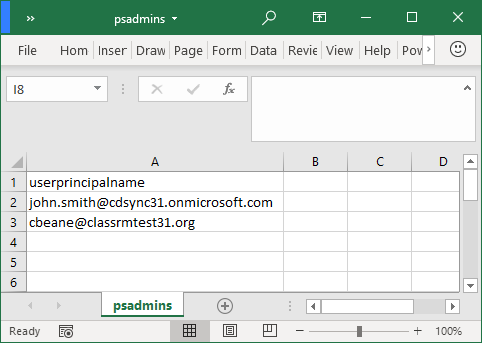
This script blocks Microsoft Graph PowerShell module for everyone in the tenant, except for a list of users specified in the CSV file. Use with caution.
Download the PowerShell script located here and the sample CSV file located here, and save both in c:\temp
Open the CSV and update the UserPrincipalName list with every admin that requires PowerShell access. Once updated, save and close the CSV file.
Launch PowerShell and run the cmd:
Set-Location c:\temp
Type cmd and press enter
.\Block-MS_Graph_module_for_everyone_except_a_list_of_admins.ps1
Blocking MS Graph Explorer
To block MS Graph Explorer for targeted users, follow the instructions to set up Conditional Access Policy.
Conditional Access in Microsoft Entra ID requires Microsoft Entra ID P1.
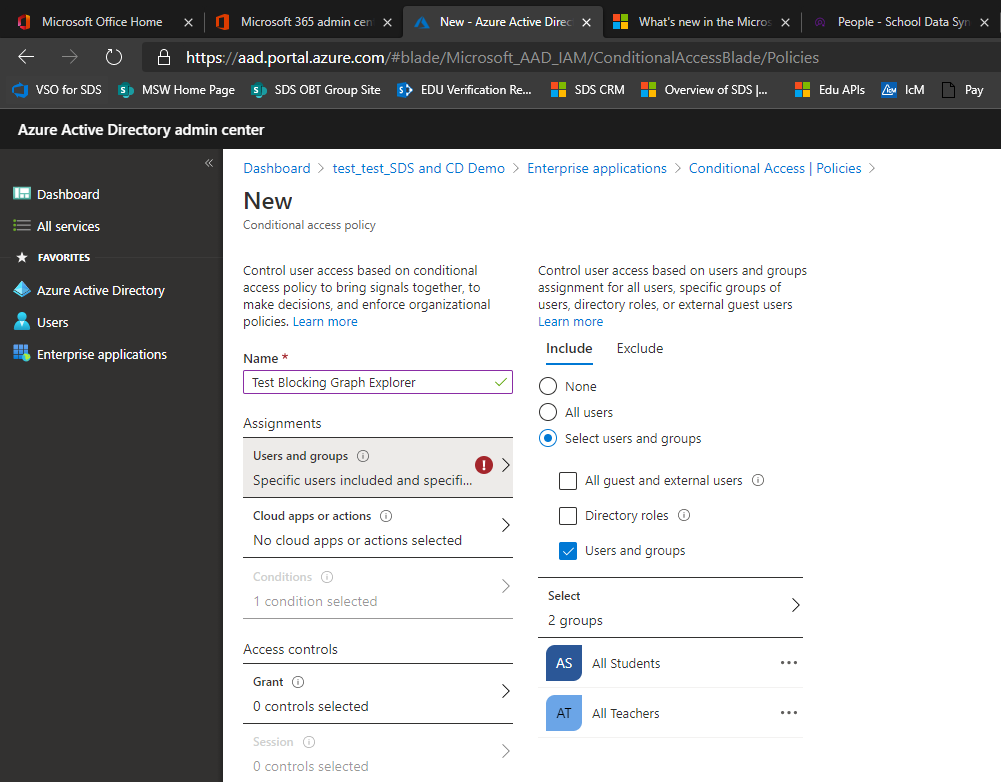
Go to Conditional Access in the Microsoft Entra admin center.
Select New Policy.
Provide a name for the policy like Block Graph Explorer.
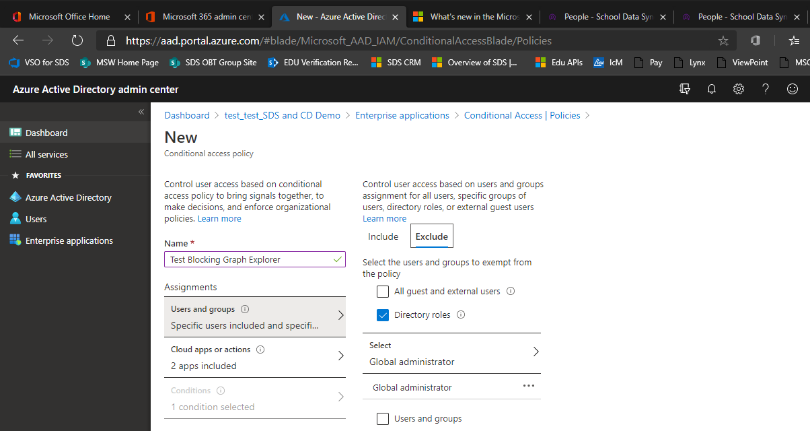
Select the users to apply the policy against, and admins to exclude from the policy.
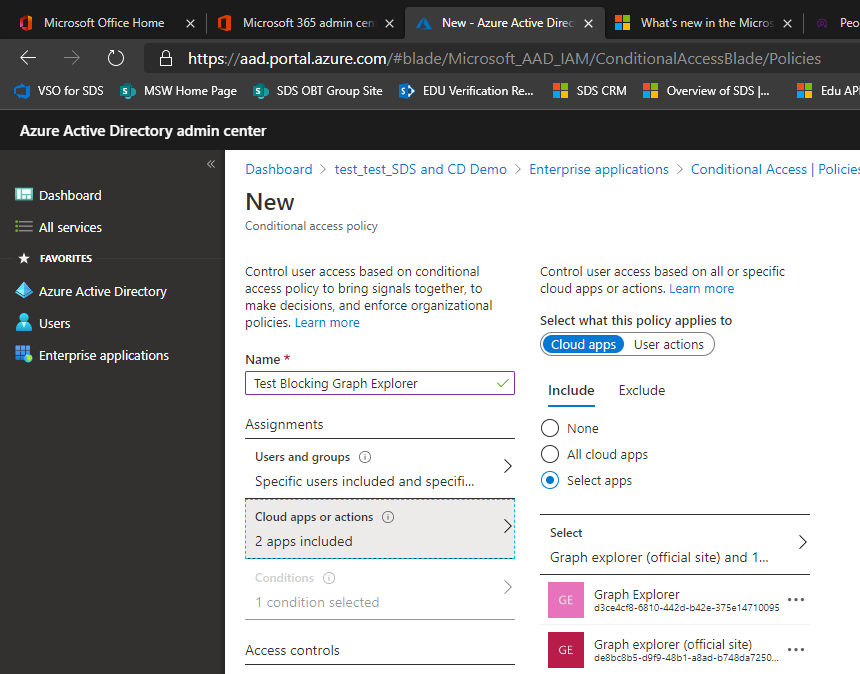
Select the Graph Explorer apps.
Select the Block Access Option and Switch the policy to On.
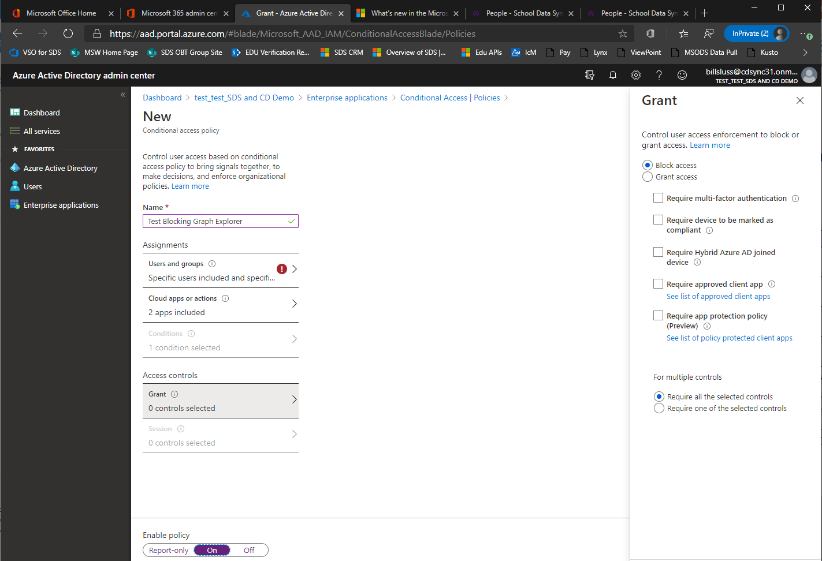
Select Create.
Blocking the MSOL Module
To block the MSOL PowerShell Module for end users, follow the instructions:
Note
If not done already, you will need to consent to delegated Directory.AccessAsUser.All before making this PATCH call.
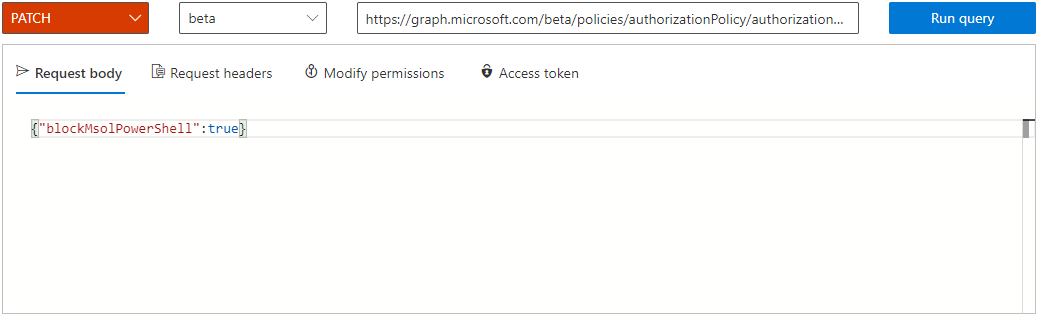
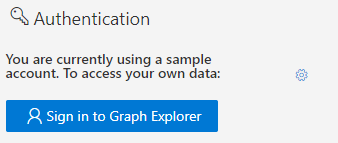
Log into MS Graph Explorer.
Select the sign-in button on the left-hand navigation pane.
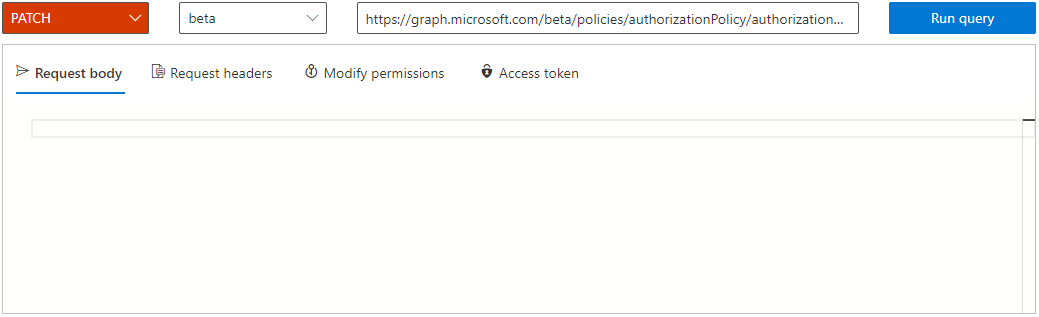
In the Query builder, select PATCH from the first dropdown menu, and select beta second dropdown menu.
In the bar with the URL, enter the string listed:
https://graph.microsoft.com/beta/policies/authorizationPolicy/authorizationPolicyIn the Request Body text block, enter the code and select Run query.
{"blockMsolPowerShell": true}
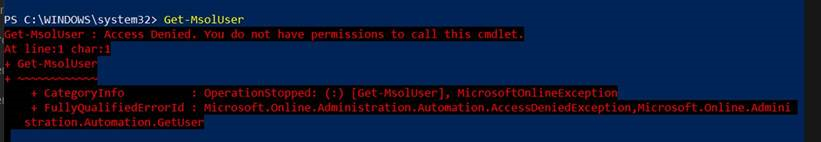
Once "blockMsolPowerShell" is set to true, users will get this error if they try to call any MSOL cmdlets:
Blocking Exchange Online PowerShell
To block the access to PowerShell in Exchange Online, follow the instructions at the link:
Enable or disable access to Exchange Online PowerShell
Control access to Intune PowerShell
By default, once an IT admin consents for the Microsoft Intune PowerShell Microsoft Entra Application for access to a tenant, all users are granted access. Users who are granted access to the Microsoft Intune PowerShell application are still limited by their permissions from Microsoft Entra roles or Intune role-based access control, but with access to PowerShell could perform bulk exports of data. You can easily change the App Registration so that only specific users can use Microsoft Intune PowerShell.
Limit access
To limit user access, you can change the application to require user assignment. To do this:
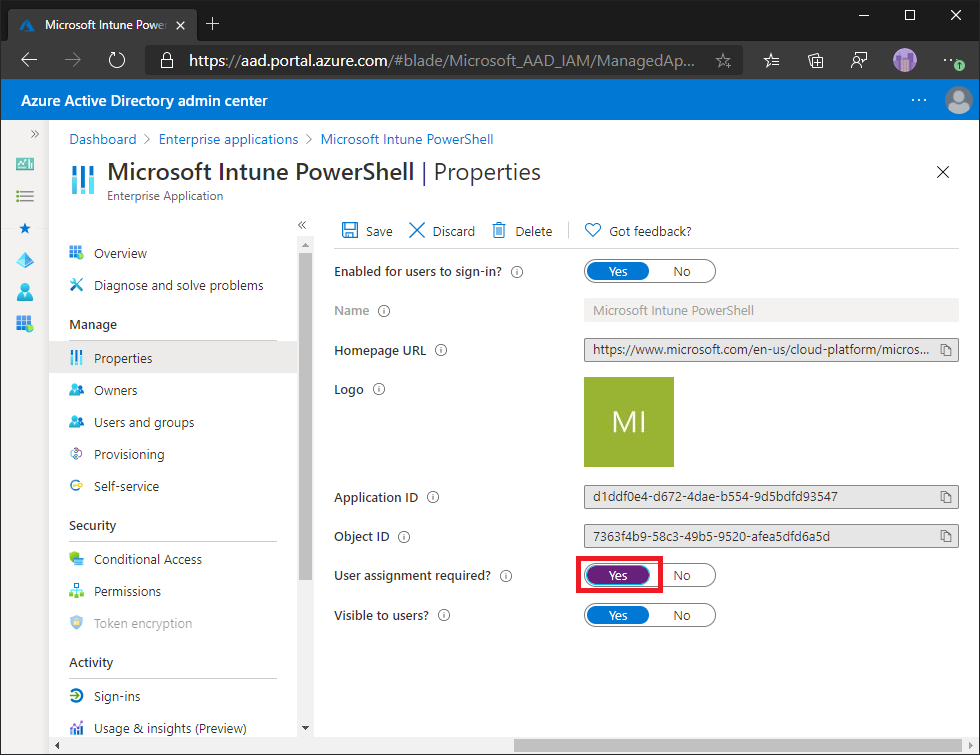
Open the Microsoft Entra Admin Console.
Select on Enterprise Applications.
Find and select on Microsoft Intune PowerShell in the list.
Select Properties.
Change User assignment required? to Yes.
Select Save.
Add or remove users
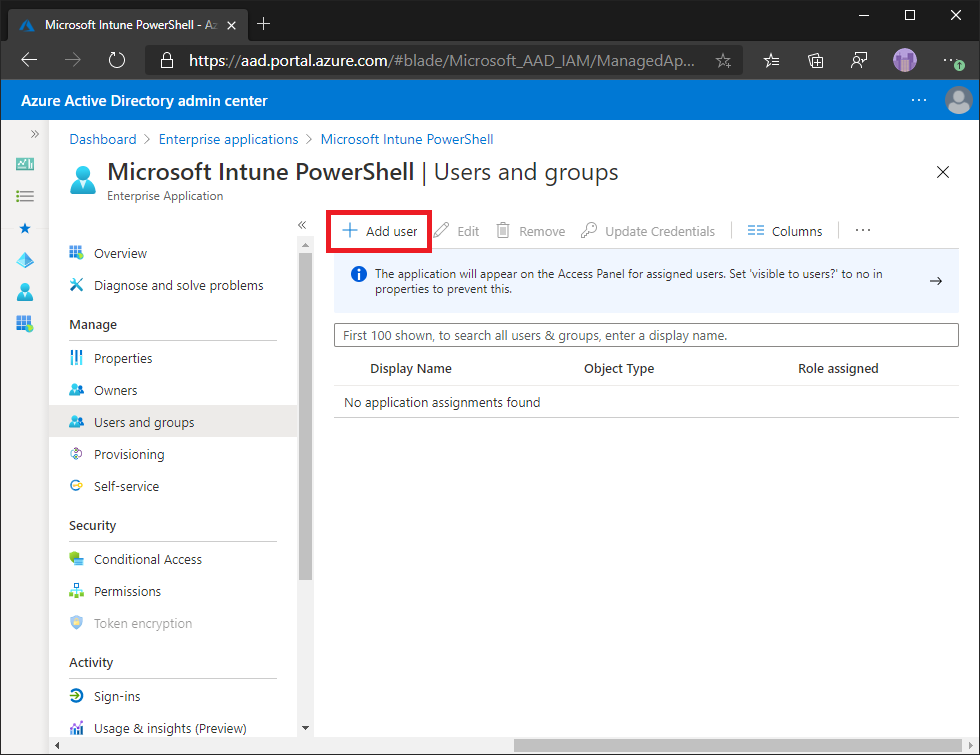
To add or remove users of the Microsoft Intune PowerShell application:
Open the Microsoft Entra Admin Console.
Select on Enterprise Applications.
Find and select on Microsoft Intune PowerShell in the list.
Select Users and groups.
Modify access as required.