Microsoft Security Copilot Logic Apps Connector
The Microsoft Security Copilot Logic Apps connector allows you to call into Copilot from an Azure Logic Apps workflow. This document provides an introduction to the connector action and its properties to get started integrating Security Copilot in your automation workflows.
The connector exposes 2 connector actions:
- Submit a Security Copilot prompt - Submit a natural language prompt to create a new Security Copilot investigation. After completion, the evaluation result will then be returned to your workflow.
- Submit a Security Copilot promptbook - Given a promptbook, invoke a new Security Copilot promptbook evaluation and return the output to your Azure Logic Apps workflow.
For more information, see Power Platform Connector Page.
Prerequisites
Tenant - Ensure that your tenant admin sets up access to Microsoft Security Copilot before using the connector.
User Authentication - This connector only supports delegated permissions via OAuth Authorization Code flow. The user that establishes connection to the connector when designing the Azure Logic Apps workflow must have access to Microsoft Security Copilot. Learn more about Microsoft Security Copilot Authentication.
Data access for enhanced interaction - It's important that the authenticated user can access data from various remote security products, including tasks like reading Defender incident reports and gathering multifactor authentication (MFA) details, among others.
Submit a Security Copilot prompt
Create and set up a new Logic Apps workflow in the Azure portal.
- The connector is available in both "Standard" and "Consumption" plan types.
Configure the initial trigger step and proceed to search for the Copilot action "Submit a Security Copilot prompt".
Fill in the parameters on the Copilot action.
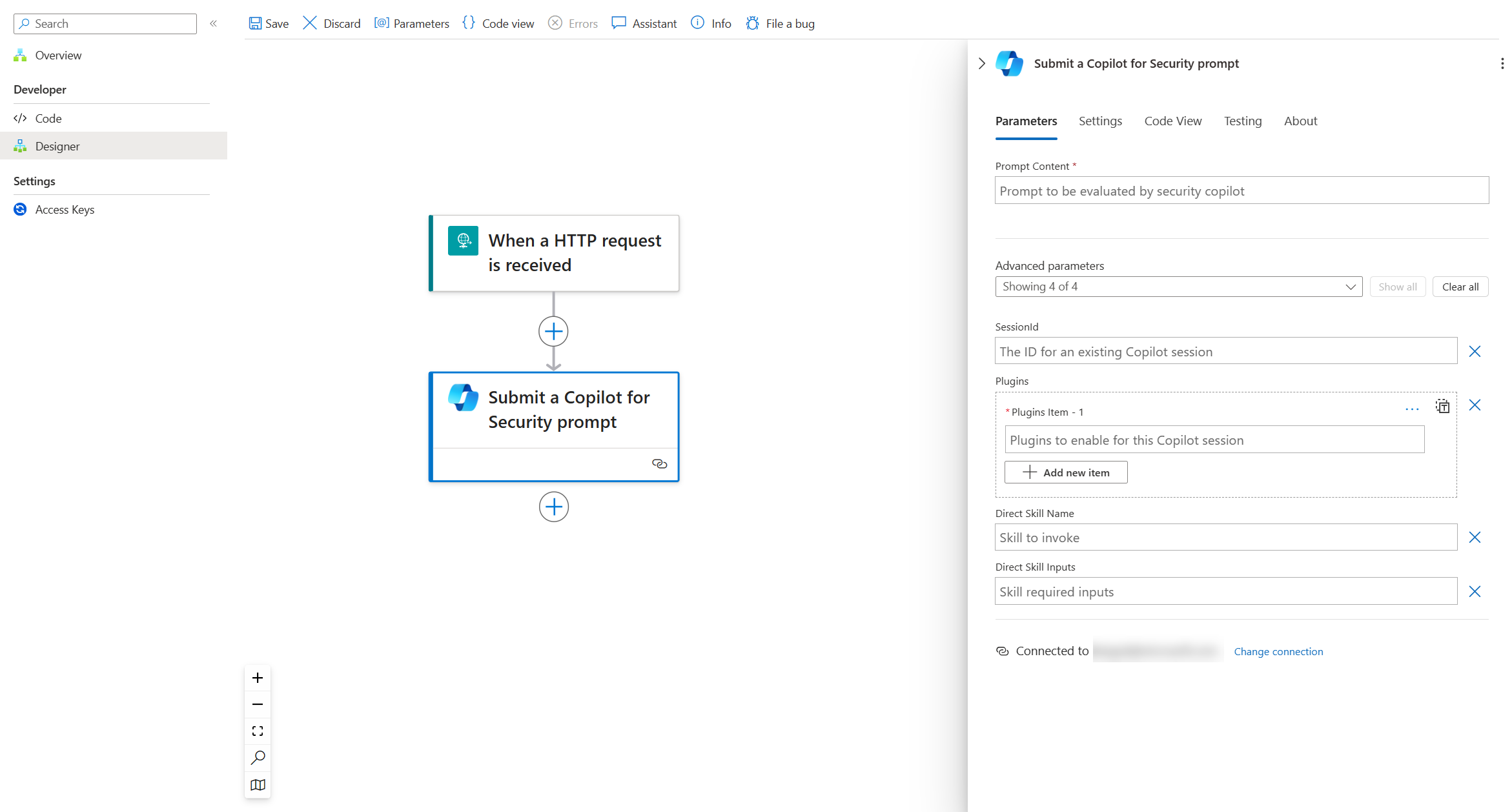
Reference the following descriptions for the Copilot Action Parameters
Prompt Content (Required): Enter the natural language prompt to be evaluated.
Session ID (Optional): Enter an existing Copilot sessionId for maintaining continuity in your tasks, allowing to ask prompts within the same investigation. If omitted, Copilot creates a new investigation.
Plugins (Optional): Enter a list of plugin names for your investigation, scoping down the potential plugins that Copilot can pick to execute and answer your natural language prompt. Useful to avoid plugin collisions.
Direct Skill Name (Optional): Enter a specific Copilot skill to execute. Convenient way to bypass the standard Copilot planner if you know a specific skill to trigger.
Direct Skill Inputs (Optional): Enter a JSON body containing key/value pairs for required skill parameters. Useful when providing a Direct Skill Name to execute.
Submit a Security Copilot promptbook
Create a new Azure Logic Apps workflow in the Azure portal.
- The connector is available in both "Standard" and "Consumption" plan types.
After setting up the Azure Logic App and configuring the initial trigger step, proceed to search for the Security Copilot action.

After choosing the new Security Copilot action, proceed to fill in the following information.

Promptbook Name (required): Select a promptbook from the dropdown list.
Promptbook Inputs (required): Inputs are displayed dynamically for promptbooks with input fields. Enter the specific inputs for each input field.
Note
You will need to ensure that required fields, such ash
<SENTINEL_INCIDENT_ID>,<THREATACTORNAME>, or<DEFENDER_INCIDENT_ID>are filled in the input fields. Otherwise, the Azure Logic App workflow will not run successfully.Session ID (optional): Enter an existing Security Copilot sessionId for maintaining continuity in your tasks, allowing to ask prompts within the same session. If omitted, Security Copilot will create a new session.