Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Human-operated ransomware continues to maintain its position as one of the most impactful cyberattack trends world-wide and is a significant threat that many organizations have faced in recent years. These attacks take advantage of network misconfigurations and thrive on an organization's weak interior security. Although these attacks pose a clear and present danger to organizations and their IT infrastructure and data, they are a preventable disaster.
The Microsoft Incident Response team (formerly DART/CRSP) responds to security compromises to help customers become cyber-resilient. Microsoft Incident Response provides onsite reactive incident response and remote proactive investigations. Microsoft Incident Response leverages Microsoft's strategic partnerships with security organizations around the world and internal Microsoft product groups to provide the most complete and thorough investigation possible.
This article describes how Microsoft Incident Response investigated a recent ransomware incident with details on the attack tactics and detection mechanisms.
See Part 1 and Part 2 of Microsoft Incident Response's guide to combatting human-operated ransomware for more information.
The attack
Microsoft Incident Response leverages incident response tools and tactics to identify threat actor behaviors for human operated ransomware. Public information regarding ransomware events focuses on the end impact, but rarely highlights the details of the operation and how threat actors were able to escalate their access undetected to discover, monetize, and extort.
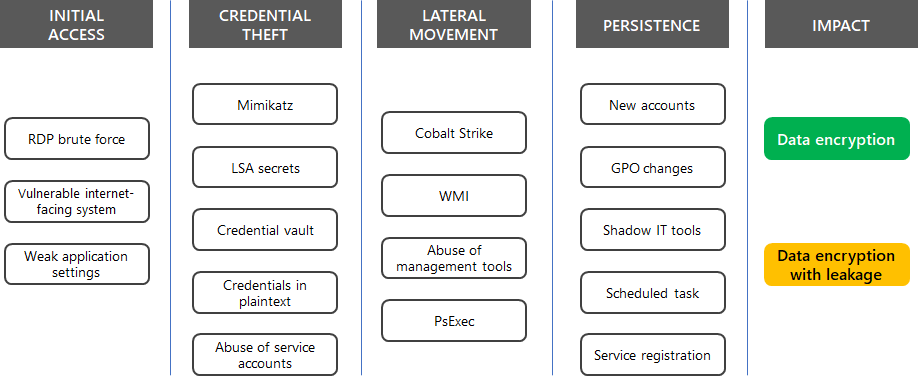
Here are some common techniques that attackers use for ransomware attacks based on MITRE ATT&CK tactics.
Microsoft Incident Response used Microsoft Defender for Endpoint to track the attacker through the environment, create a story depicting the incident, and then eradicate the threat and remediate. Once deployed, Defender for Endpoint began detecting successful logons from a brute force attack. Upon discovering this, Microsoft Incident Response reviewed the security data and found several vulnerable Internet-facing devices using the Remote Desktop Protocol (RDP).
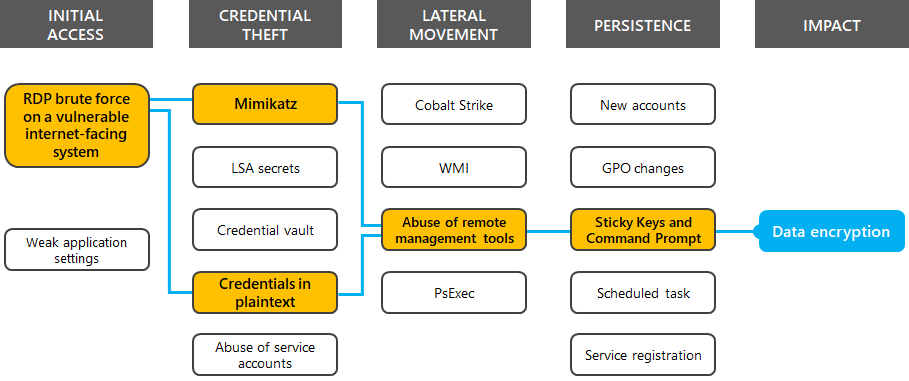
After initial access was gained, the threat actor used the Mimikatz credential harvesting tool to dump password hashes, scanned for credentials stored in plaintext, created backdoors with Sticky Key manipulation, and moved laterally throughout the network using remote desktop sessions.
For this case study, here is the highlighted path that the attacker took.
The following sections describe additional details based on the MITRE ATT&CK tactics and include examples of how the threat actor activities were detected with the Microsoft Defender portal.
Initial access
Ransomware campaigns use well-known vulnerabilities for their initial entry, typically using phishing emails or weaknesses in perimeter defense such as devices with the enabled Remote Desktop service exposed on the Internet.
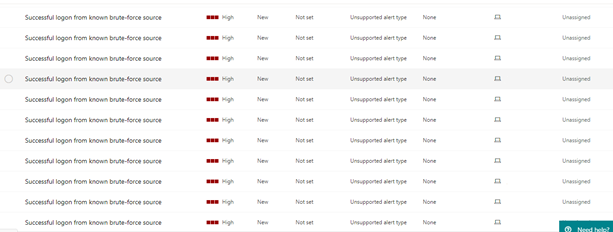
For this incident, Microsoft Incident Response managed to locate a device that had TCP port 3389 for RDP exposed to the Internet. This allowed threat actors to perform a brute-force authentication attack and gain the initial foothold.
Defender for Endpoint used threat intelligence to determine that there were numerous sign-ins from known brute-force sources and displayed them in the Microsoft Defender portal. Here's an example.
Reconnaissance
Once the initial access was successful, environment enumeration and device discovery began. These activities allowed the threat actors to identify information about the organization's internal network and target critical systems such as domain controllers, backup servers, databases, and cloud resources. After the enumeration and device discovery, the threat actors performed similar activities to identify vulnerable user accounts, groups, permissions, and software.
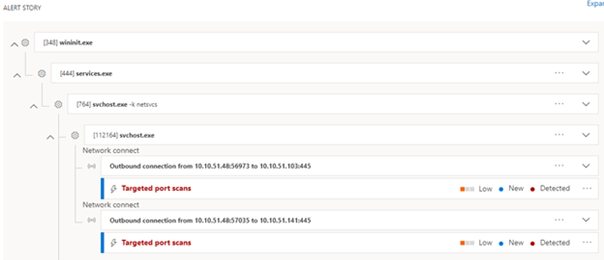
The threat actor leveraged Advanced IP Scanner, an IP address scanning tool, to enumerate the IP addresses used in the environment and perform subsequent port scanning. By scanning for open ports, the threat actor discovered devices that were accessible from the initially compromised device.
This activity was detected in Defender for Endpoint and used as an indicator of compromise (IoC) for further investigation. Here's an example.
Credential theft
After gaining initial access, the threat actors performed credential harvesting using the Mimikatz password retrieval tool and by searching for files containing “password” on initially compromised systems. These actions enabled the threat actors to access additional systems with legitimate credentials. In many situations, threat actors use these accounts to create additional accounts to maintain persistence after the initial compromised accounts are identified and remediated.
Here's an example of the detected use of the Mimikatz in the Microsoft Defender portal.
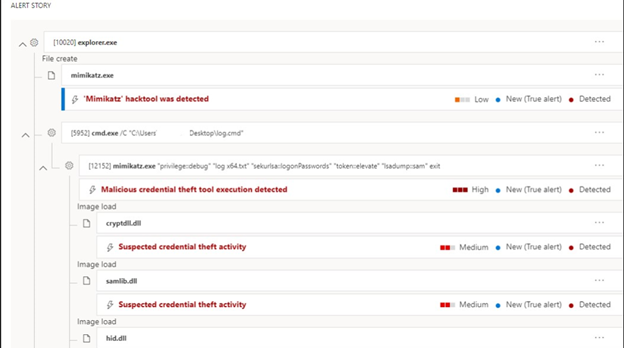
Lateral movement
Movement across endpoints can vary between different organizations, but threat actors commonly use different varieties of remote management software that already exists on the device. By utilizing methods of remote access that the IT department commonly uses in their day-to-day activities, threat actors can fly under the radar for extended periods of time.
Using Microsoft Defender for Identity, Microsoft Incident Response was able to map out the path that the threat actor took between devices, displaying the accounts that were used and accessed. Here's an example.
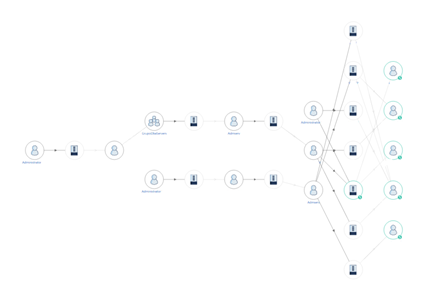
Defense evasion
To avoid detection, the threat actors used defense evasion techniques to avoid identification and achieve their objectives throughout the attack cycle. These techniques include disabling or tampering with anti-virus products, uninstalling or disabling security products or features, modifying firewall rules, and using obfuscation techniques to hide the artifacts of an intrusion from security products and services.
The threat actor for this incident used PowerShell to disable real-time protection for Microsoft Defender on Windows 11 and Windows 10 devices and local networking tools to open TCP port 3389 and allow RDP connections. These changes decreased the chances of detection in an environment because they modified system services that detect and alert on malicious activity.
Defender for Endpoint, however, cannot be disabled from the local device and was able to detect this activity. Here's an example.
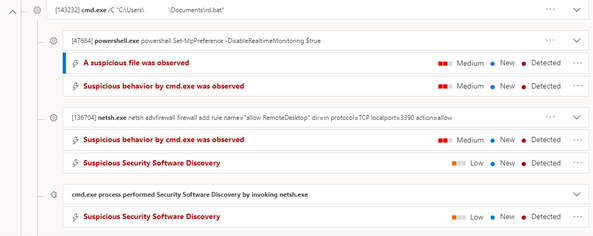
Persistence
Persistence techniques include actions by threat actors to maintain consistent access to systems after efforts are made by security staff to regain control of compromised systems.
The threat actors for this incident used the Sticky Keys hack because it allows for remote execution of a binary inside the Windows operating system without authentication. They then used this capability to launch a Command Prompt and perform further attacks.
Here's an example of the detection of the Sticky Keys hack in the Microsoft Defender portal.
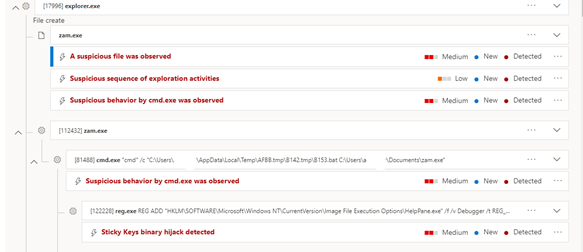
Impact
Threat actors typically encrypt files using applications or features that already exist within the environment. The use of PsExec, Group Policy, and Microsoft Endpoint Configuration Management are methods of deployment that allow an actor to quickly reach endpoints and systems without disrupting normal operations.
The threat actor for this incident leveraged PsExec to remotely launch an interactive PowerShell Script from various remote shares. This attack method randomizes distribution points and makes remediation more difficult during the final phase of the ransomware attack.
Ransomware execution
Ransomware execution is one of the primary methods that a threat actor uses to monetize their attack. Regardless of the execution methodology, distinct ransomware frameworks tend to have a common behavioral pattern once deployed:
- Obfuscate threat actor actions
- Establish persistence
- Disable windows error recovery and automatic repair
- Stop a list of services
- Terminate a list of processes
- Delete shadow copies and backups
- Encrypt files, potentially specifying custom exclusions
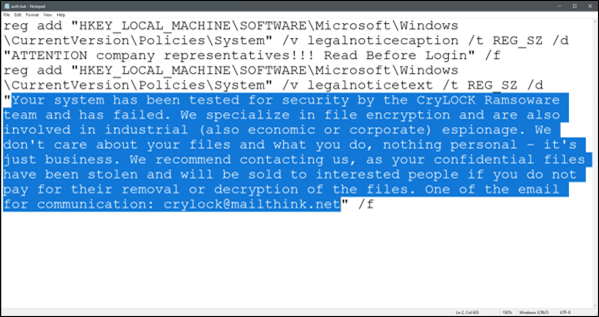
- Create a ransomware note
Here's an example of a ransomware note.
Additional ransomware resources
Key information from Microsoft:
- The growing threat of ransomware, Microsoft On the Issues blog post on July 20, 2021
- Human-operated ransomware
- Rapidly protect against ransomware and extortion
- 2021 Microsoft Digital Defense Report (see pages 10-19)
- Ransomware: A pervasive and ongoing threat threat analytics report in the Microsoft Defender portal
- Microsoft Incident Response ransomware approach and best practices
Microsoft 365:
- Deploy ransomware protection for your Microsoft 365 tenant
- Maximize Ransomware Resiliency with Azure and Microsoft 365
- Recover from a ransomware attack
- Malware and ransomware protection
- Protect your Windows 10 PC from ransomware
- Handling ransomware in SharePoint Online
- Threat analytics reports for ransomware in the Microsoft Defender portal
Microsoft Defender XDR:
Microsoft Defender for Cloud Apps:
Microsoft Azure:
- Azure Defenses for Ransomware Attack
- Maximize Ransomware Resiliency with Azure and Microsoft 365
- Backup and restore plan to protect against ransomware
- Help protect from ransomware with Microsoft Azure Backup (26 minute video)
- Recovering from systemic identity compromise
- Advanced multistage attack detection in Microsoft Sentinel
- Fusion Detection for Ransomware in Microsoft Sentinel
Microsoft Security team blog posts:
3 steps to prevent and recover from ransomware (September 2021)
A guide to combatting human-operated ransomware: Part 1 (September 2021)
Key steps on how Microsoft Incident Response conducts ransomware incident investigations.
A guide to combatting human-operated ransomware: Part 2 (September 2021)
Recommendations and best practices.
-
See the Ransomware section.
Human-operated ransomware attacks: A preventable disaster (March 2020)
Includes attack chain analyses of actual attacks.
Norsk Hydro responds to ransomware attack with transparency (December 2019)