Report: Kernel System Calls
A kernel system call, or syscall, is an entry point via which usermode code can call functions in the Linux kernel. A syscall table is a mapping between the syscall ID and the kernel address of its implementation.
Report Data: Ia32 (32-bit) Syscalls
Following is the IA32 Syscall Table at the time the memory snapshot was taken of the centos 6 - 2.6.32-696.28.1.el6.x86_64 image from the samples gallery (requires authentication).
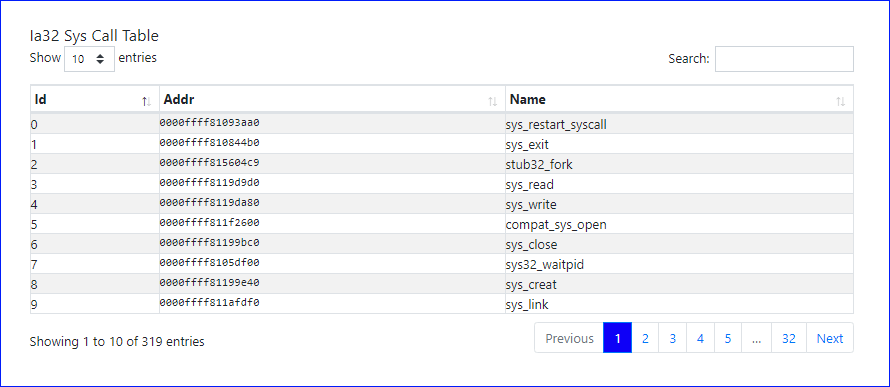
The following tables describes each column of the reported data.
| Column | Description | Notes |
|---|---|---|
| Id | Syscall ID | |
| Addr | Kernel memory address | |
| Name | Syscall name |
Report Data: (64-bit) Syscalls
Following is the syscall table at the time the memory snapshot was taken of the centos 6 - 2.6.32-696.28.1.el6.x86_64 image from the samples gallery (requires authentication).
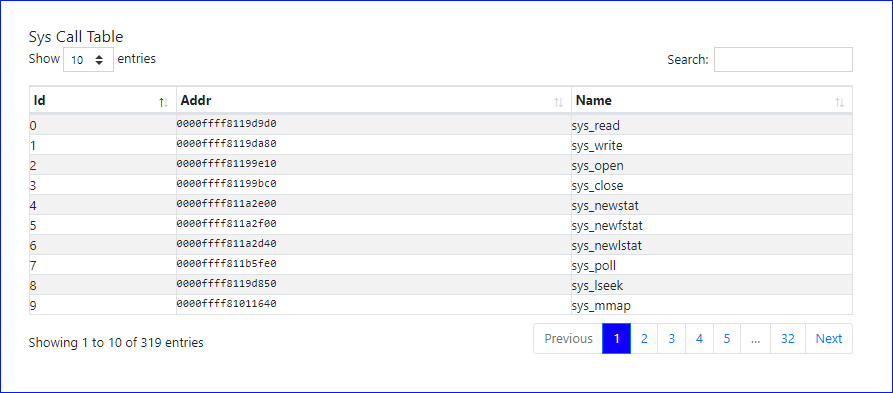
The following tables describes each column of the reported data.
| Column | Description | Notes |
|---|---|---|
| Id | Syscall ID | |
| Addr | Kernel memory address | |
| Name | Syscall name |
Forensic Hints
Patterns to look for:
Note that the Project Freta analysis engine infers the existence of rootkits and other hooks of these objects, and lists them in the Potential Rootkits report section.
This data cannot be obtained from a running Linux system, so an internal-external comparison is not possible.