Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
When developers build SharePoint Framework solutions, they might need to connect to an API that's secured through Microsoft Entra ID. Developers can specify which Microsoft Entra applications and permissions their solution requires, and an administrator can manage the permission request from API access in the SharePoint admin center.
Learn more about building SharePoint Framework solutions that connect to Azure-AD secured APIs.
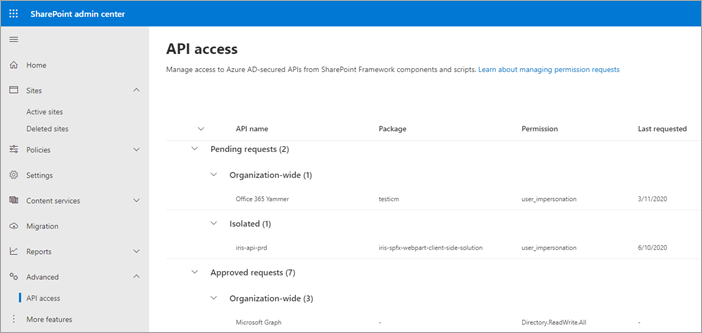
The API access page shows pending and approved requests. It also shows which requests apply to any SharePoint Framework component or custom script in your organization (organization-wide) and which requests apply to only the specific component (isolated).
Note
The admin role that's required to approve permissions depends on the API. To approve permissions to any of the third-party APIs registered in the tenant, the application administrator role is sufficient. To approve permissions for Microsoft Graph or any other Microsoft API, the Global Administrator role is required. The API access page is not available for people signed in with the global reader role.
Approve a pending request
Select the request, and then select Approve to see details about the request.
In the Approve access panel, select Approve.
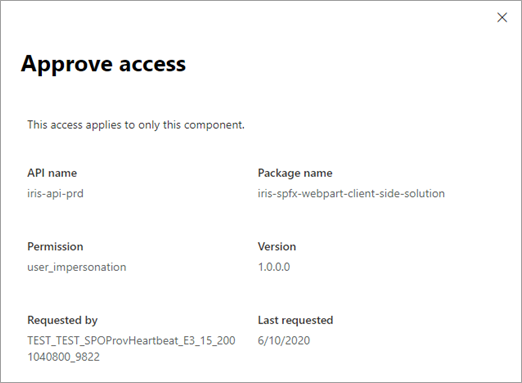
After you approve a request, it moves to the Approved requests list.
Note
Permissions of type delegated are added to the SharePoint Online Client Extensibility Web Application Principal in Microsoft Entra ID.
If you try to approve a permission request for a resource that already has some permissions granted (for example, granting additional permissions to the Microsoft Graph), the requested scopes are added to the previously granted permissions.
Reject a pending request
Select the request, and select Reject.
Select Reject again to confirm.
Rejecting access doesn't remove the app from the Apps site. If the app is used on any sites, it might not work as expected. After you reject the request, it's removed from the page and the developer will need to issue a new request with the same resource and scope.
Remove access to a previously approved request
Select the request, and then select Remove access.
Select Remove again to confirm.
When you remove access, solutions and custom scripts that rely on the permission might not work as expected. After you remove access, the request is removed from the page and the developer will need to issue a new request with the same resource and scope.
Manage access by using Microsoft PowerShell
You can also use PowerShell to manage permission requests.
- To view pending requests, use the cmdlet Get-SPOTenantServicePrincipalPermissionRequests.
- To approve a request, use the cmdlet Approve-SPOTenantServicePrincipalPermissionRequest.
- To reject a request, use the cmdlet Deny-SPOTenantServicePrincipalPermissionRequest.
- To remove access to a previously approved request, use the cmdlet Revoke-SPOTenantServicePrincipalPermission.