Understand Microsoft Online Services incident response phase 1 - preparation
Now that you know the teams responsible for incident response, we will explore each phase of the incident response process.
Preparation enables rapid response when an incident occurs and may even prevent incidents in the first place. Microsoft dedicates significant resources to preparing for security incidents.
Training
Each employee working at Microsoft is required to take training appropriate to their role regarding security incident response. Initial training occurs when a new employee begins working at Microsoft, and annual refresher training takes place every year thereafter. The training is designed to provide the employee with an understanding of Microsoft's fundamental approach to security. Upon completion of the training, all employees can:
- Define a security incident.
- Explain their role and responsibility to report security incidents.
- Describe how security response teams respond to security incidents.
- How to escalate a potential security incident to the appropriate security response team.
- Articulate special concerns regarding privacy, particularly customer privacy.
- Access additional information about security, privacy, and escalation contacts.
In addition to general security training, employees involved in incident response receive supplementary role-based security training.
Maintaining the on-call engineers (OCEs)
All service operations teams, including security response teams, maintain an on-call rotation to ensure there are resources available 24x7x365. The on-call rotation includes backups for availability and escalation points to ensure accountability. The OCEs and their on-call times are centrally listed for each service team within the same dashboard where incidents are managed. Our on-call rotations enable Microsoft to mount an effective incident response at any time or scale, including widespread or concurrent events.
OCEs use Secure Admin Workstations to access the production environment, and their access is time-bound and scoped to the tasks required for incident response.
Tools and resources
Microsoft security response teams are responsible for maintaining all tools and resources associated with security incident response. These include online help resources designed to quickly inform on-call engineers of proper procedures and how to escalate potential issues quickly and securely. Incident response resources also include custom tools, scripts, and processes to help the security response teams address a variety of security issues and attack types. OCEs must complete yearly training and obtain up-to-date background checks to maintain eligibility for access to incident response tools and resources.
Incident response testing
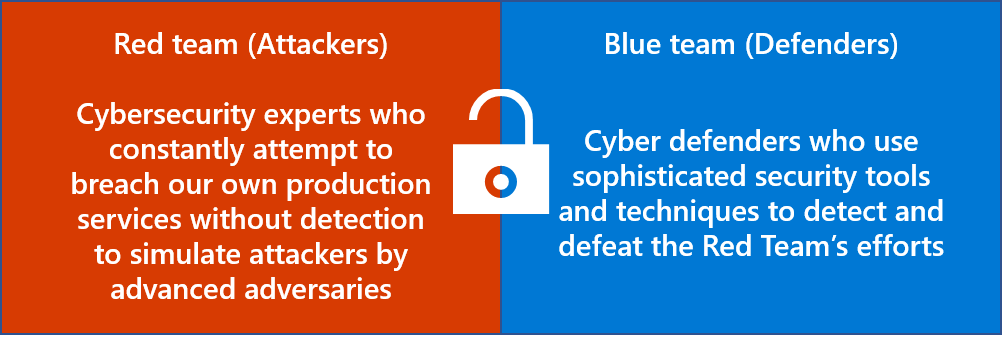
Microsoft regularly tests, reviews, and updates its incident response plan to account for changes to the environment and new security threats. Our incident response testing methodology uses real-time, unpredictable attacks from internal teams of security penetration testers that we call the Red Team. The Red Team uses a variety of techniques to attempt to compromise Microsoft Online Services systems without detection. Red Team efforts simulate real-world attacks and test the capabilities of Microsoft's security response teams.
In the context of internal penetration testing, Microsoft's security response teams are known as the Blue Team. The Blue Team uses the incident response process to detect and respond to Red Team attacks as if they were genuine security incidents. Customer data is never the target of penetration testing, but these exercises help to ensure Microsoft Online Services are prepared to detect, prevent, and respond to new kinds of security threats.
In addition to ongoing internal penetration testing, Microsoft conducts a variety of other incident response exercises, including ‘capture the flag' events, one-off tabletop exercises, and other impromptu or organized events. These exercises supplement ongoing internal penetration testing to ensure all teams are adequately prepared to fulfill their responsibilities in the event of a real security incident.
Protection of evidence
The data collected during an incident response is often sensitive and must remain secure. Microsoft's security response teams are responsible for ensuring adequate encryption and information protection for all incident-related communications and documentation. This includes using secured evidence lockers for storage of forensic evidence collected during investigations. The team follows approved processes for handling forensic evidence, including chain of custody, to ensure all incident-related evidence remains secure and unmodified.