Examine secure communications using virtual networks
Azure Virtual Network is a service that provides the fundamental building block for your private network in Azure. An instance of the service (a virtual network) enables many types of Azure resources to securely communicate with each other, the internet, and on-premises networks. These Azure resources include virtual machines (VMs).
A virtual network is similar to a traditional network that you'd operate in your own datacenter. But it brings extra benefits of the Azure infrastructure, such as scale, availability, and isolation.
Key scenarios that you can accomplish with a virtual network include:
- Communication of Azure resources with the internet.
- Communication between Azure resources.
- Communication with on-premises resources.
- Filtering of network traffic.
- Routing of network traffic.
- Integration with Azure services.
Communicate with the internet
All resources in a virtual network can communicate outbound with the internet, by default. You can also use a public IP address, NAT gateway, or public load balancer to manage your outbound connections. You can communicate inbound with a resource by assigning a public IP address or a public load balancer.
When you're using only an internal standard load balancer, outbound connectivity isn't available until you define how you want outbound connections to work with an instance-level public IP address or a public load balancer.
Communicate between Azure resources
Azure resources communicate securely with each other in one of the following ways:
Virtual network: You can deploy VMs and other types of Azure resources in a virtual network. Examples of resources include App Service Environments, Azure Kubernetes Service (AKS), and Azure Virtual Machine Scale Sets.
Virtual network service endpoint: You can extend your virtual network's private address space and the identity of your virtual network to Azure service resources over a direct connection. Examples of resources include Azure Storage accounts and Azure SQL Database. Service endpoints allow you to secure your critical Azure service resources to only a virtual network.
Virtual network peering: You can connect virtual networks to each other by using virtual peering. The resources in either virtual network can then communicate with each other. The virtual networks that you connect can be in the same, or different, Azure regions.
Communicate with on-premises resources
You can connect your on-premises computers and networks to a virtual network by using any of the following options:
Point-to-site virtual private network (VPN): Established between a virtual network and a single computer in your network. Each computer that wants to establish connectivity with a virtual network must configure its connection. This connection type is useful if you're just getting started with Azure, or for developers, because it requires few or no changes to an existing network. The communication between your computer and a virtual network is sent through an encrypted tunnel over the internet.
Site-to-site VPN: Established between your on-premises VPN device and an Azure VPN gateway that's deployed in a virtual network. This connection type enables any on-premises resource that you authorize to access a virtual network. The communication between your on-premises VPN device and an Azure VPN gateway is sent through an encrypted tunnel over the internet.
Azure ExpressRoute: Established between your network and Azure, through an ExpressRoute partner. This connection is private. Traffic doesn't go over the internet.
Filter network traffic
You can filter network traffic between subnets by using either or both of the following options:
Network security groups: Network security groups and application security groups can contain multiple inbound and outbound security rules. These rules enable you to filter traffic to and from resources by source and destination IP address, port, and protocol.
Network virtual appliances: A network virtual appliance is a VM that performs a network function, such as a firewall or WAN optimization. To view a list of available network virtual appliances that you can deploy in a virtual network, go to Azure Marketplace.
Route network traffic
Azure routes traffic between subnets, connected virtual networks, on-premises networks, and the internet, by default. You can implement either or both of the following options to override the default routes that Azure creates:
Route tables: You can create custom route tables that control where traffic is routed to for each subnet.
Border gateway protocol (BGP) routes: If you connect your virtual network to your on-premises network by using an Azure VPN gateway or an ExpressRoute connection, you can propagate your on-premises BGP routes to your virtual networks.
Integrate with Azure services
Integrating Azure services with an Azure virtual network enables private access to the service from virtual machines or compute resources in the virtual network. You can use the following options for this integration:
Deploy dedicated instances of the service into a virtual network. The services can then be privately accessed within the virtual network and from on-premises networks.
Use Azure Private Link to privately access a specific instance of the service from your virtual network and from on-premises networks.
Access the service over public endpoints by extending a virtual network to the service, through service endpoints. Service endpoints allow service resources to be secured to the virtual network.
Connect privately to an Azure container registry using Azure Private Link
You can limit access to a registry by assigning virtual network private IP addresses to the registry endpoints and using Azure Private Link. Network traffic between the clients on the virtual network and the registry's private endpoints traverses the virtual network and a private link on the Microsoft backbone network, eliminating exposure from the public internet. Private Link also enables private registry access from on-premises through Azure ExpressRoute, private peering, or a VPN gateway.
You can configure DNS settings for the registry's private endpoints, so that the settings resolve to the registry's allocated private IP address. With DNS configuration, clients and services in the network can continue to access the registry at the registry's fully qualified domain name, such as myregistry.azurecr.io.
Note
Private endpoint configuration is available in the Premium container registry service tier.
Set up private endpoint
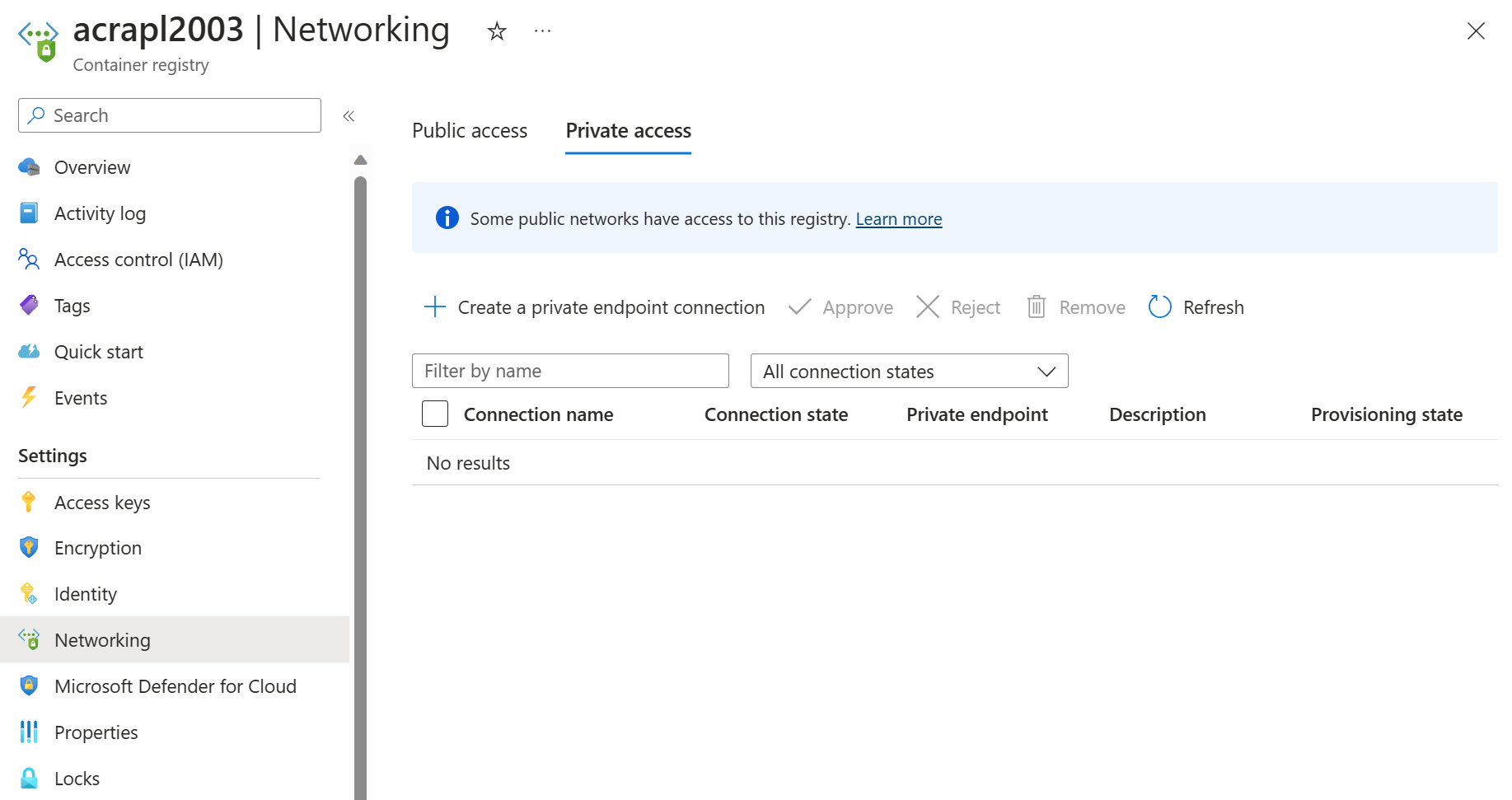
In the portal, navigate to your container registry.
Under Settings, select Networking.
On the Private access tab, select + Create private endpoint connection.
On the Basics tab of the Create a private endpoint page, enter or select the following information:
- Subscription: Select your subscription.
- Resource group: Enter the name of an existing group or create a new one.
- Name: Enter a name.
- Region: Select a region.
Select Next: Resource.
On the Resource tab of the Create a private endpoint page, enter or select the following information:
- Connection method: For this example, select Connect to an Azure resource in my directory.
- Subscription: Select your subscription.
- Resource type: Select Microsoft.ContainerRegistry/registries.
- Resource: Select the name of your registry.
- Target subresource: Select registry.
Select Next: Configuration.
On the Configuration tab of the Create a private endpoint page, enter or select the information:
- Virtual network: Select the virtual network for the private endpoint.
- Subnet: Select the subnet for the private endpoint.
- Integrate with private DNS zone: Select Yes.
- Private DNS Zone: Select (New) privatelink.azurecr.io