Create a logging and monitoring baseline
Logging and monitoring are critical requirements when you try to identify, detect, and mitigate security threats. A proper logging policy can ensure that you can determine when a security violation has occurred. The policy also can potentially identify who is responsible. Azure activity logs provide data about external access to a resource, and they provide diagnostic logs, so you have information about the operation of a specific resource.
Note
An Azure activity log is a subscription log that provides insight into subscription-level events that occurred in Azure. By using the activity log, you can determine the what, who, and when for any write operations that occurred on the resources in your subscription.
Logging policy recommendations
The following sections describe the security recommendations in CIS Microsoft Azure Foundations Security Benchmark v. 3.0.0 to set logging and monitoring policies on your Azure subscriptions. Included with each recommendation are the basic steps to complete in the Azure portal. You should complete these steps for your own subscription and by using your own resources to validate each security recommendation. Keep in mind that Level 2 options might restrict some features or activity, so carefully consider which security options you decide to enforce.
Ensure that a diagnostic setting exists - Level 1
The Azure activity log provides insight into subscription-level events that occurred in Azure. This log includes a range of data, from Azure Resource Manager operational data to updates on Azure Service Health events. The activity log previously was called an audit log or an operational log. The Administrative category reports control-plane events for your subscriptions.
Each Azure subscription has a single activity log. The log provides data about resource operations that originated outside Azure.
Diagnostic logs are emitted by a resource. Diagnostic logs provide information about the operation of the resource. You must enable diagnostic settings for each resource.
Sign in to the Azure portal. Search for and select Monitor.
In the left menu, select Activity log.
In the Activity log menu bar, select Export activity logs.
If no settings are shown, select your subscription, and then select Add diagnostic setting.
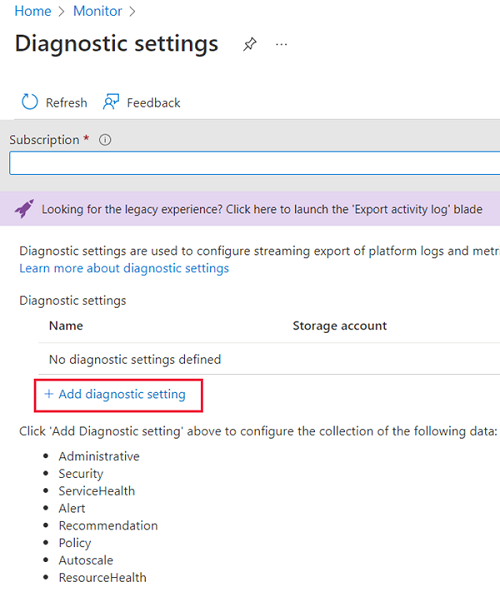
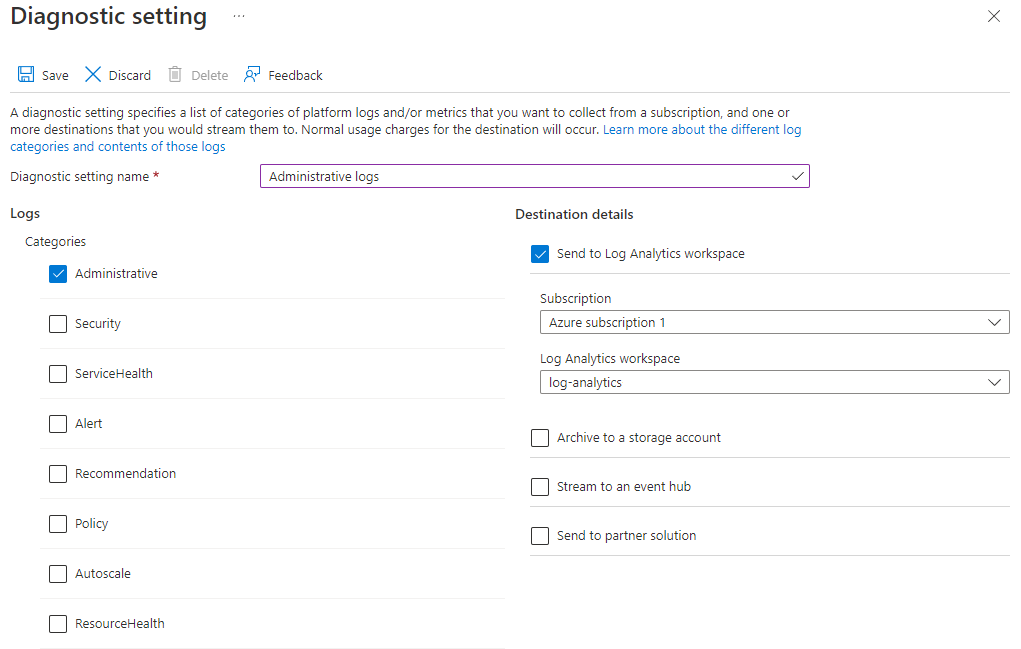
Enter a name for your diagnostic setting, and then select log categories and destination details.
In the menu bar, select Save.
Here's an example of how to create a diagnostic setting:
Create an activity log alert for creating a policy assignment - Level 1
If you monitor policies that are created, you can see which users can create policies. The information might help you detect a breach or misconfiguration of your Azure resources or subscription.
Sign in to the Azure portal. Search for and select Monitor.
In the left menu, select Alerts.
In the Alerts menu bar, select the Create dropdown, and then select Alert rule.
In the Create an alert rule pane, select Select scope.
In the Select a resource pane, in the Filter by resource type dropdown, select Policy assignment (policyAssignments).
Select a resource to monitor.
Select Done.
To finish creating the alert, complete the steps that are described in Create an alert rule from the Azure Monitor Alerts pane.
Create an activity log alert for creating, updating, or deleting a network security group - Level 1
By default, no monitoring alerts are created when NSGs are created, updated, or deleted. Changing or deleting a security group can allow internal resources to be accessed from improper sources or for unexpected outbound network traffic.
Sign in to the Azure portal. Search for and select Monitor.
In the left menu, select Alerts.
In the Alerts menu bar, select the Create dropdown, and then select Alert rule.
In the Create an alert rule pane, select Select scope.
In the Select a resource pane, in the Filter by resource type dropdown, select Network security groups.
Select Done.
To finish creating the alert, complete the steps that are described in Create an alert rule from the Azure Monitor Alerts pane.
Create an activity log alert for creating or updating a SQL Server firewall rule - Level 1
Monitoring for events that create or update a SQL Server firewall rule provides insight into network access changes, and it might reduce the time it takes to detect suspicious activity.
Sign in to the Azure portal. Search for and select Monitor.
In the left menu, select Alerts.
In the Alerts menu bar, select the Create dropdown, and then select Alert rule.
In the Create alert rule pane, select Select scope.
In the Select a resource pane, in the Filter by resource type dropdown, select SQL servers.
Select Done.
To finish creating the alert, complete the steps that are described in Create an alert rule from the Azure Monitor Alerts pane.
