Describe what is cybersecurity
People, organizations, and governments are routinely falling victim to cyberattacks. We constantly hear references to concepts like cybersecurity, cyberattacks, cybercriminals, and more. This can all sound daunting and difficult to grasp. To protect yourself and those around you, you'll need to have a basic understanding of these concepts.
What is a cyberattack?
A cyberattack is commonly defined as an attempt to gain illegal access to a computer or computer system to cause damage or harm. But only thinking of computers or computer systems, in a traditional sense, is limiting. The reality is that a cyberattack can occur on almost any modern digital device. The impact can range from an inconvenience for an individual to global economic and social disruption.
An attacker can use people, computers, phones, applications, messages, and system processes to carry out an attack. Individuals, organizations, institutions, and governments can be victims of an attack. These attackers might:
- Lock data and processes, and demand a ransom.
- Remove vital information to cause serious harm.
- Steal information.
- Publicly expose private information.
- Stop vital business processes and systems from running, to cause disruption and malfunction.
With cyberattacks continuously evolving, it's important for you to remember that attackers don't exclusively need a computer to carry out an attack. Also, attacks can vary widely in their nature and scope. Any digitally connected device or entity can be used as part of an attack, or be subject to an attack.
What is a cybercriminal?
A cybercriminal is anyone who carries out a cyberattack. Cybercriminals can be:
- A single person or a group of people.
- An organization for hire.
- A government entity.
Cybercriminals can be located anywhere, including embedded inside an organization or institution, to cause damage from within.
What is cybersecurity?
Cybersecurity refers to technologies, processes, and training that help protect systems, networks, programs, and data from cyberattacks, damage, and unauthorized access. Cybersecurity enables you to achieve the following goals:
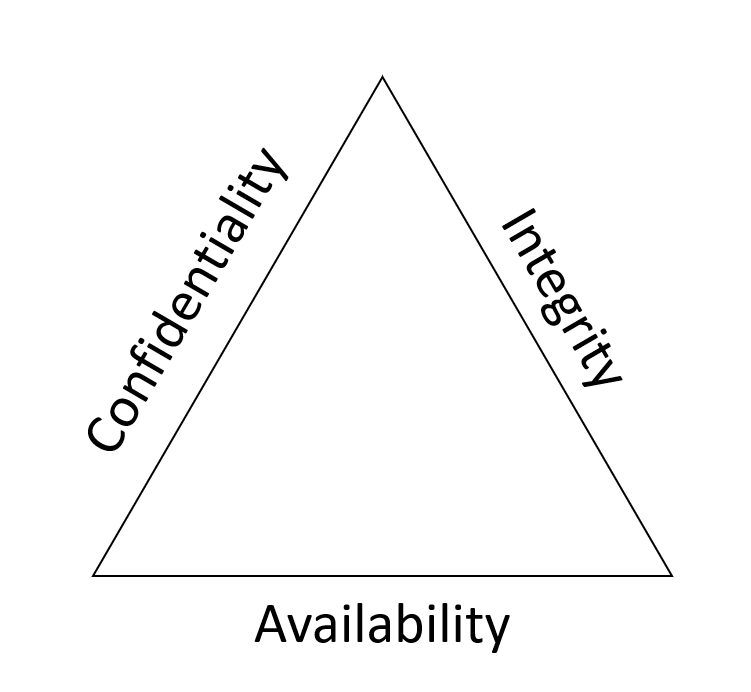
- Confidentiality: Information should only be visible to the right people.
- Integrity: Information should only be changed by the right people or processes.
- Availability: Information should be visible and accessible whenever needed.
This is commonly referred to as the Confidentiality, Integrity, Availability (CIA) model in the context of cybersecurity. Throughout the rest of this module, you'll learn about the types of attacks that cybercriminals use to disrupt these goals, and cause harm. You'll also see some basic threat mitigation strategies.