Compare spam and malware
- 4 minutes
While spam and bulk email are often a nuisance, they typically don’t carry a payload that causes harm to a user’s system. They just get in the way of a user’s productivity. However, attackers responded by taking a typically innocuous feature such as spam and bulk email and turned it into an attack vehicle. In this case, it's malware, which can cause great harm to an organization. The term "malware" is short for "malicious software." Organizations typically receive malware in email as either an attachment or an embedded link to a malicious web site or file.
Malware usually works in two stages:
- Stage 1. The user opens an infected attachment or visits an infected web site. The malware then uses code to exploit a user’s computer using macros and JavaScript to plant a payload such as a virus or Trojan horse.
- Stage 2. The infected attachment or site delivers the payload.
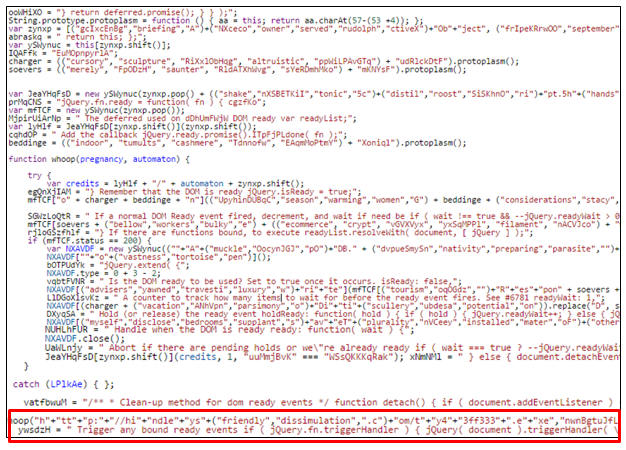
Example of malware
To the untrained eye, the sample code in the following image looks harmless enough. However, the two lines at the bottom of the image force the user’s browser to redirect to a malicious web site.
Knowledge check
Choose the best response for the following question.