Plan to implement Microsoft Purview Data Loss Protection
Microsoft Purview Data Loss Prevention (DLP) helps organizations maintain compliance with regulatory requirements. It also helps them protect their sensitive data from potential data breaches, whether they store their data on-premises, in the cloud, or share it with third-party vendors.
To help organizations achieve these goals, Microsoft Purview DLP provides a range of features, including:
- Automated discovery and classification of sensitive data.
- Continuous monitoring and tracking of sensitive data.
- Integration with other Microsoft services, such as Microsoft Entra Protection and Microsoft Cloud App Security.
- Customizable policy creation to enforce data protection measures.
- Real-time alerts and reports on potential data breaches.
Note
Azure Active Directory (Azure AD) is now Microsoft Entra ID. Learn more.
Implementing these features takes a coordinated planning effort. This training unit focuses on how organizations should plan to implement Microsoft Purview DLP.
Multiple starting points
Every organization plans for and implements Microsoft Purview DLP differently. Why? Because every organization's business needs, goals, resources, and situation are unique to them. However, there are elements that are common to all successful DLP implementations. This unit presents the best practices that organizations use in their DLP planning.
Many organizations choose to implement DLP to comply with various governmental or industry regulations. Organizations also implement data loss prevention to protect their intellectual property. But the starting place and ultimate destination in the DLP journey vary from one organization to another.
Organizations can start their DLP journeys in various ways. For example:
- From a platform focus, they want to protect information in Teams Chat and Channel messages or on Windows devices.
- They know what sensitive information they want to prioritize protecting, like health care records. Given this information, they may go straight to defining policies to protect it.
- They may not know what their sensitive information is, where it is, and who is doing what with it. As such, they start with discovery and categorization and take a more methodical approach.
- They may not know what their sensitive information is, where it is, or who is doing what with it. Even without this information, they may still move straight to defining policies. From there, they use those outcomes as a starting place and then refine their policies from there.
- They want to implement the full Microsoft Purview Information Protection stack. As such, they intend to take a longer, more methodical approach to DLP implementation.
These examples are just some ways in which customers can approach DLP. It doesn't matter where an organization starts from. Microsoft Purview DLP is flexible enough to accommodate various types of information protection journeys - from their start, to a fully realized data loss prevention strategy.
Overview of the Microsoft Purview DLP planning process
There are different aspects of the Microsoft Purview DLP planning process. The following sections examine each of these considerations.
Identify stakeholders
When an organization implements DLP policies, it can apply them across large portions of the company. In doing so, it's essential that the IT department doesn't develop a broad ranging plan on their own. Failure to do so always results in negative consequences. Instead, an organization must identify the stakeholders across departments who can:
- Describe the regulations, laws, and industry standards the organization is subject to.
- Determine the categories of sensitive items requiring protection.
- Identify the business processes that would require a DLP policy.
- Identify the risky behavior the company wants to limit.
- Prioritize which data to protect first based on the sensitivity of the items and risk involved.
- Outline each DLP policy match event review and remediation process.
In general, these needs tend to be 85% regulatory and compliance protection, and 15% intellectual property protection. Here are some suggestions on roles to include in an organization's planning process:
- Regulatory and compliance officers
- Chief risk officer
- Legal officers
- Security and compliance officers
- Business owners for the data items
- Business users
- IT
Describe the categories of sensitive information to protect
Once an organization identifies the DLP stakeholders, they should then describe:
- The categories of sensitive information they want to protect.
- The business processes that use the data found in these categories.
For example, DLP may define the following categories:
- Financial
- Medical and health information
- Privacy
- Custom
Set goals and create an implementation plan
Once the stakeholders define which sensitive information needs protection and the location of the data:
- The stakeholders can set their protection goals.
- The IT department can develop an implementation plan.
An organization's implementation plan should include:
- Mapping out its starting state and desired end state and the steps to get from one to the other.
- How it addresses discovery of sensitive items.
- Policy planning.
- The steps required to implement the plan.
- How it addresses any prerequisites.
- How it tests policies before moving to enforcement.
- How it trains its end users.
- How it tests and tunes its policies.
- How it reviews and updates its data loss prevention strategy based on changing regulatory, legal, industry standard or intellectual property protection and business needs.
Map out path from start to desired end state
Why is it essential for an organization to document how it's going to get from its starting state to the desired end state? Because documentation is key to communicating with its stakeholders and setting the project scope.
The following diagram displays a set of steps that organizations commonly use to deploy Microsoft Purview DLP. You can use this outline to frame your DLP adoption path and then fill in the details.
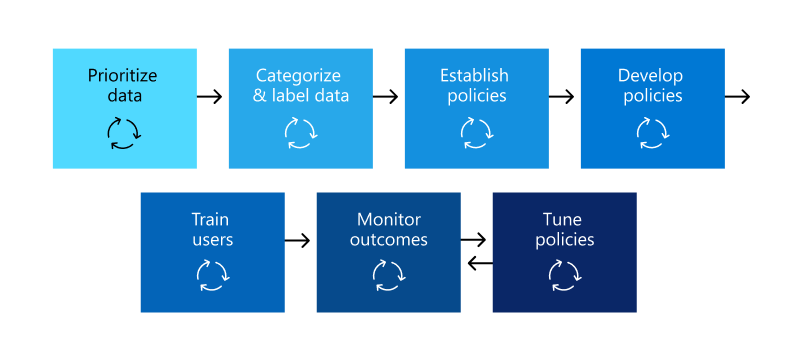
Sensitive item discovery
There are multiple ways to discover what an organization's sensitive items are and their location. An organization may have sensitivity labels already deployed. Or, it decided to deploy a broad DLP policy to all locations that only discovers and audits items. To learn more, see Know your data.
Policy planning
As organizations begin their DLP adoption, they can use the following questions to focus their policy design and implementation efforts.
| Question | Answer | Example |
|---|---|---|
| What laws, regulations and industry standards must your organization comply with? | Because many organizations come to DLP with the goal of regulatory compliance, answering this question is a natural starting place for planning their DLP implementation. But, as the IT implementer, you probably can't answer it. Instead, our legal team and business executives must provide the answer. | Your organization is subject to U.K. financial regulations. |
| What sensitive items does your organization want to protect from leakage? | Once an organization knows where it stands in terms of regulatory compliance needs, it can determine: - The sensitive items to protect from leakage. - How it wants to prioritize policy implementation to protect them. This information helps it choose the most appropriate DLP policy templates. Microsoft Purview comes with preconfigured DLP templates for Financial, Medical and health, and Privacy. An organization can also build its own template using the Custom template feature. As an organization designs and creates its actual DLP policies, knowing the answer to this question also helps it choose the correct sensitive information type. |
To get started quickly, you pick the U.K. Financial Data policy template. This template includes the credit card number, EU debit card number, and SWIFT code sensitive information types. |
| Where are the sensitive items and what business processes use them? | An organization uses items that contain sensitive information every day while doing business. An organization must know where it stores instances of that sensitive information. It must also know what business processes use this data. Knowing this information helps the organization choose the right locations in which to apply its DLP policies. You can apply DLP policies to the following locations: - Exchange email - SharePoint sites - OneDrive accounts - Teams chat and channel messages - Windows 10 and 11 Devices - Microsoft Defender for Cloud Apps - On-premises repositories |
Your organizations' internal auditors are tracking a set of credit card numbers. They keep a spreadsheet of them in a secure SharePoint site. Several of the employees make copies and save them to their work OneDrive for Business site. They sync this site to their Windows 10 and 11 devices. One of them pastes a list of 14 credit card numbers in an email and tries to send it to the outside auditors for review. You want to apply the policy to the secure SharePoint site, all the internal auditors' OneDrive for Business accounts, their Windows 10 and 11 devices, and Exchange email. |
| What is your organization's tolerance for leakage? | Different groups in your organization may have different views on what's an acceptable level of sensitive item leakage and what's not. Achieving the perfection of zero leakage may come at too high a cost to the business. | Your organizations' security group, along with the legal team, both feel there should be no sharing of credit card numbers with anyone outside the organization. It insists on zero leakage. But, as part of its regular review of credit card number activity, the internal auditors must share some credit card numbers with third-party auditors. If your DLP policy prohibits all sharing of credit card numbers outside the organization, a significant business process disruption ensues. The organization must also incur an added cost to mitigate the disruption so that internal auditors can complete their tracking. However, this extra cost is unacceptable to the executive leadership. To resolve this situation, there must be an internal conversation to determine an acceptable level of leakage. Once an organization agrees to that level, the policy can provide exceptions for certain individuals to share the information. Or the organization can apply it in audit only mode. |
Planning for prerequisites
Before an organization can monitor DLP locations, it must first satisfy the DLP prerequisites. For more information, see the Before you begin section in the following articles:
- Get started with the data loss prevention on-premises scanner.
- Get started with Endpoint data loss prevention.
- Get started with the Microsoft compliance extension.
- Use data loss prevention policies for non-Microsoft cloud apps.
Policy deployment
When an organization creates its DLP policies, it should consider rolling them out gradually to assess their effect. It should also test their effectiveness before fully enforcing them. For example, an organization doesn't want a new DLP policy to unintentionally block access to thousands of documents or to break an existing business process.
Some organizations create DLP policies that may significantly affect their business processes. In these situations, Microsoft recommends that organizations follow this sequence:
Start in Test mode without Policy Tips. By doing so, the organization can assess the effect using the DLP reports and any incident reports. It can use DLP reports to view the number, location, type, and severity of policy matches. Based on the results, it can fine-tune the policies as needed. In test mode. DLP policies don't affect the productivity of people working in the organization. This stage should also test the organization's workflow for DLP event review and issue remediation.
Move to Test mode with notifications and Policy Tips. Doing so enables an organization to begin teaching users about its compliance policies. It also prepares them for the policies that it's going to apply. It's useful to have a link to an organization policy page that provides more details about the policy in the policy tip. At this stage, the organization can also ask users to report false positives so that it can further refine the policies. An organization should move to this stage once it has confidence the results of its policy application match what the stakeholders had in mind.
Start full enforcement on the policies. By doing so, the system applies the actions in the rules to protect the content. Continue to monitor the DLP reports and any incident reports or notifications. When doing so, ensure you see the intended results.
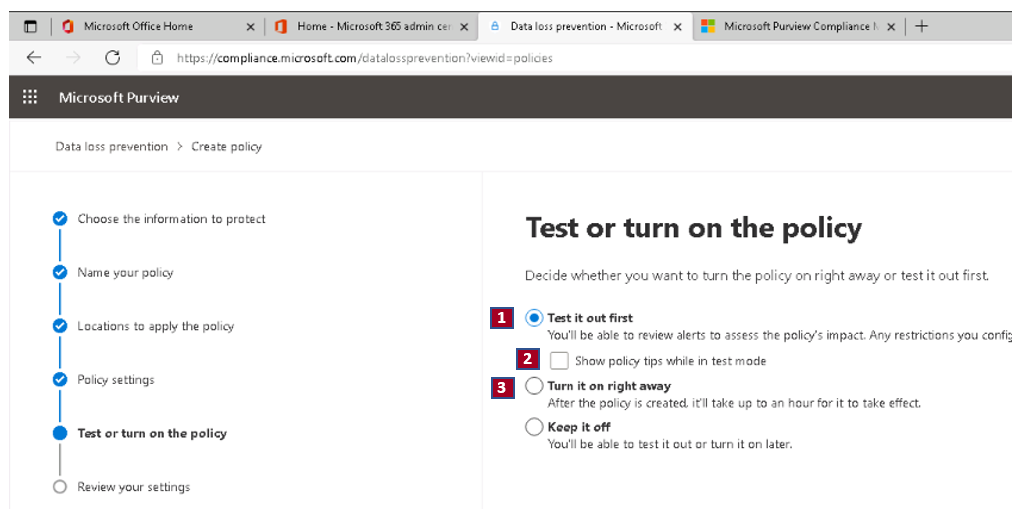
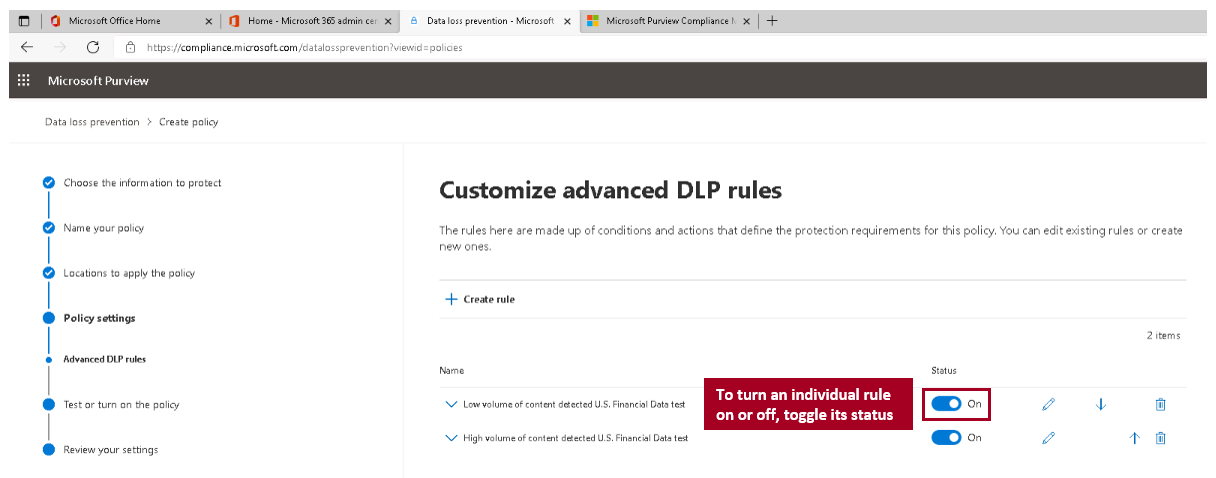
An organization can turn off a DLP policy at any time, which affects all rules in the policy. However, you can turn off each rule individually by toggling its Status in the rule editor.
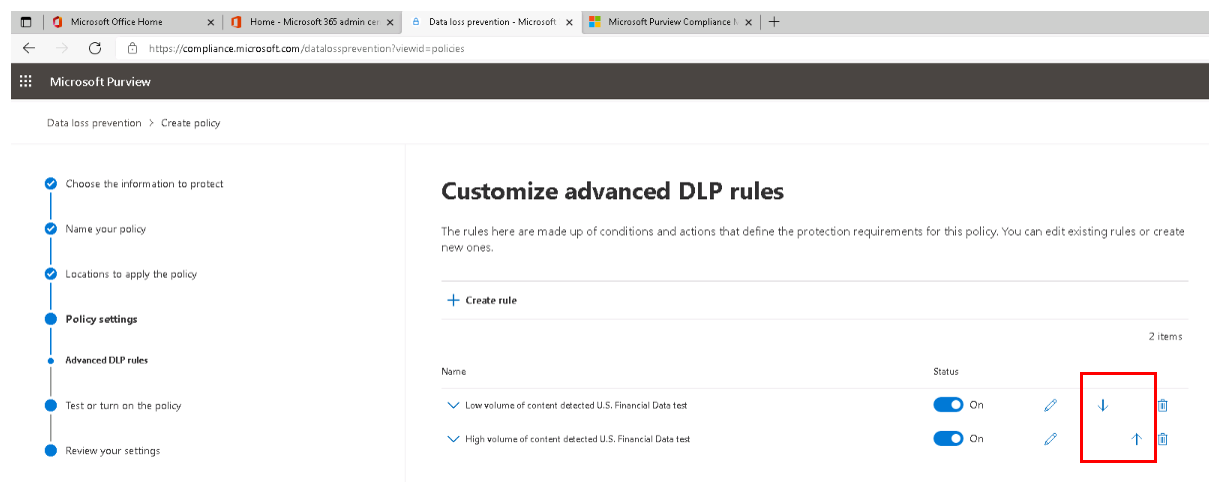
An organization can also change the priority of multiple rules in a policy. To do that, open a policy for editing. In the row for a rule, select the appropriate Up or Down arrow to rearrange the order of the rules.
End-user training
An organization can configure its DLP policies to Send email notifications and show policy tips for DLP policies to administrators and end users. Policies can send notifications and display policy tips when a user activity triggers a DLP policy. Policy tips are useful ways to raise awareness of risky behaviors on sensitive items and train users to avoid those behaviors in the future. This design is especially true while an organization's policies are still in test mode and before they enforce blocking actions.
Review DLP requirements and update strategy
The regulations, laws, and industry standards that an organization is subject to change over time. An organization's business goals for DLP may also change. An organization should include regular reviews of all these areas so that it stays in compliance, and its DLP implementation continues to meet its business needs.
Approaches to deployment
The following table identifies sample scenarios for three fictitious companies. The scenarios describe the business needs for each company. These business needs are real-world requirements taken from real-world implementations. For each company, the table also identifies the approach it should consider when implementing DLP to meet its business needs.
| Description of the customer's business needs | DLP implementation approach |
|---|---|
| Woodgrove Bank is in a highly regulated industry and has many different types of sensitive items in many different locations. The company: - Knows which types of sensitive information are top priority. - Must minimize business disruption as it rolls out policies. - Has IT resources and can hire experts to help plan, design, and deploy. - Has a premier support contract with Microsoft. |
- Take the time to understand what regulations it must comply with and how it's going to comply. -Take the time to understand the better value of the Microsoft Purview Information Protection stack. - Develop sensitivity labeling scheme for prioritized items and apply them. - Involve business process owners. - Design/code policies, deploy in test mode, and train users. - Repeat. |
| Lucerne Publishing doesn’t know what it has or where it is. It also has little to no resource depth. It extensively uses Teams, OneDrive for Business, and Exchange. | - Start with simple policies on the prioritized locations. - Monitor what gets identified. - Apply sensitivity labels accordingly. - Refine policies and train users. |
| Fabrikam is a small startup. It wants to protect its intellectual property, but it must move quickly. It's willing to dedicate some resources to implementing DLP, but it can't afford to hire outside experts. Fabrikam is currently facing the following issues: - Sensitive items are all in Microsoft 365 OneDrive for Business/SharePoint. - Adoption of OneDrive for Business and SharePoint is slow, employees/shadow IT use, and DropBox and Google drive to share/store items. - Employees value speed of work over data protection discipline. - It splurged and bought all 18 employees new Windows 11 devices. |
- Take advantage of the default DLP policy in Microsoft Teams. - Use the Restricted by default setting for SharePoint items. - Deploy policies that prevent external sharing. - Deploy policies to prioritized locations. - Deploy policies to Windows 11 devices. - Block uploads to non-OneDrive for Business cloud storage. |
Knowledge check
Choose the best response for the following question.