Introduction
DevOps practices enable development teams to deploy applications faster and more frequently. However, speed without security creates risk. Moving fast toward a security vulnerability doesn't help your business. The challenge is maintaining velocity while ensuring applications remain secure throughout their lifecycle.
The security challenge in modern development
DevOps teams have access to unprecedented infrastructure and scale through cloud platforms. This accessibility brings opportunities but also exposes organizations to sophisticated security threats. Every application deployment potentially risks business security, customer data, and organizational reputation.
Traditional security approaches fail in modern environments: Perimeter-based security models that protected data centers with firewalls and network controls don't translate to distributed cloud environments. Applications span multiple services, regions, and cloud providers. Data flows between microservices, APIs, and external integrations. The traditional castle-and-moat approach no longer provides adequate protection.
Modern security requires multiple defense layers: Organizations must adopt security at multiple levels including application code, infrastructure, network, data, and identity. Security can't exist as a single checkpoint. It must be embedded throughout the stack with multiple opportunities to detect and prevent threats.
The DevSecOps approach
How do you ensure applications are secure and stay secure with continuous integration and continuous delivery? How can you find and fix security issues early in the development process? The answer lies in practices commonly referred to as DevSecOps.
Security as a shared responsibility: DevSecOps incorporates security teams and their capabilities into your DevOps practices, making security the responsibility of everyone on the team rather than a separate function. Developers, operations engineers, and security specialists collaborate throughout the development lifecycle.
Shift security left: Security needs to shift from an afterthought evaluated at the end of development to a consideration at every process step. This "shift left" approach catches security issues early when they're easier and less expensive to fix. A vulnerability found during code review costs far less than one discovered in production.
Security as a continuous process
Securing applications is a continuous process that encompasses multiple areas:
Secure infrastructure: Build on secure foundations including hardened operating systems, properly configured networks, encrypted storage, and secure identity management.
Architecture with layered security: Design applications with security built into the architecture. Implement defense in depth with multiple security layers so if one control fails, others remain effective.
Continuous security validation: Automate security testing throughout your pipeline. Run security scans, vulnerability assessments, and compliance checks as part of continuous integration and deployment.
Monitoring and response: Monitor applications in production for security threats and anomalous behavior. Respond quickly to detected issues with automated remediation where possible.
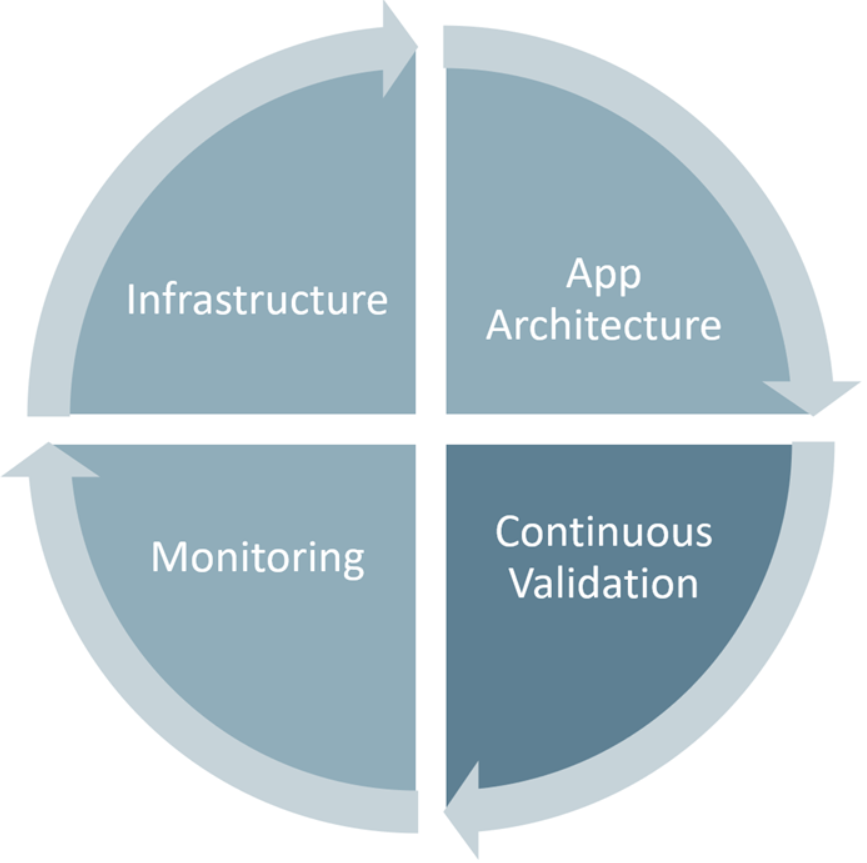
Holistic security approach: Security is everyone's responsibility and must be addressed holistically across the entire application lifecycle from initial design through production operation and eventual decommissioning.
What this module covers
This module introduces DevSecOps concepts and practices that integrate security throughout your development lifecycle:
Common vulnerabilities: You'll learn about SQL injection attacks, one of the most prevalent and dangerous security vulnerabilities. Understanding how these attacks work helps you prevent them in your applications.
DevSecOps principles: You'll understand how DevSecOps differs from traditional security approaches and how to integrate security practices into your existing DevOps workflows without sacrificing development velocity.
Pipeline security: You'll discover critical validation points in your CI/CD pipeline where security checks should occur. Learn how to implement automated security testing that catches vulnerabilities before they reach production.
Threat modeling: You'll learn systematic approaches to identifying, evaluating, and prioritizing security threats. Threat modeling helps you focus security efforts on the most significant risks to your applications and business.
Automated security analysis: You'll explore tools like GitHub CodeQL that provide automated security analysis. These tools scan code for vulnerabilities and security patterns, enabling you to find issues early without manual security reviews for every code change.
Accelerating security teams: Continuous integration and deployment pipelines can actually accelerate the work of security teams by automating repetitive security checks and improving collaboration with software development teams. Security teams can focus on complex threats rather than manual review of routine changes.
Learning objectives
After completing this module, you'll be able to:
- Identify and understand SQL injection attacks and their impact on application security.
- Explain DevSecOps principles and how security integrates throughout the development lifecycle.
- Implement security validation at key points in your DevOps pipeline.
- Conduct threat modeling to identify and prioritize security risks.
- Use GitHub CodeQL for automated security analysis and vulnerability detection.
Prerequisites
- Understanding of DevOps concepts and practices.
- Familiarity with continuous integration and continuous deployment pipelines.
- Basic knowledge of application development and common security concepts.
- Experience with version control systems like Git.
- Beneficial to have experience in an organization that delivers software.