Understand the Communication Compliance workflow
Communication compliance policies are just one part of the larger process for reducing communication risks in Microsoft 365. Once policies are in place, organizations need to investigate issues, take action on violations, and continually evaluate whether the policies are effective. This section outlines the end-to-end workflow for identifying and resolving communication compliance issues.
Overview of the workflow
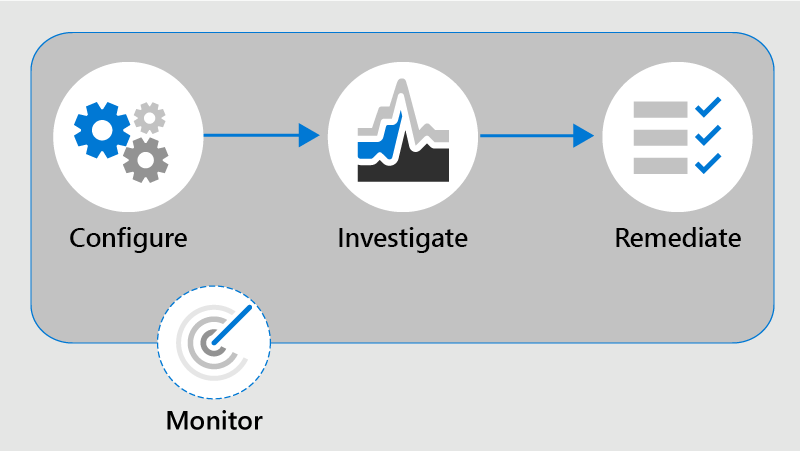
The communication compliance workflow follows four phases:
Configure policies that define what to look for.
Investigate messages that match those policy conditions.
Remediate violations through notices, escalations, or case creation.
Maintain and refine your policies by reviewing dashboard trends, alert patterns, and policy health insights.
Each phase builds on the last, helping you respond quickly and consistently to communication risks.
Phase 1: Configure
Start by identifying which compliance risks are most relevant to your organization. Use built-in policy templates to quickly create policies for common scenarios like inappropriate language, data leaks, or misuse of AI tools. You can also create custom policies to define your own detection signals and review settings.
Configuration includes decisions like:
- What content to scan (email, Teams, Viva Engage, Microsoft 365 Copilot)
- Who should be in scope (all users, specific groups, adaptive scopes)
- Which classifiers, keywords, or sensitive info types to use
- Who should review alerts
Policies begin scanning content about an hour after creation and continue hourly by default.
Phase 2: Investigate
When a message matches a policy condition, an alert is generated. Alerts are prioritized by severity and appear on the Communication Compliance dashboard and Alerts page. From there, reviewers can:
- View alert details and the conversation context
- Filter messages by sender, recipient, or date
- Review user activity history related to the alert
- Evaluate policy matches using different message views
Each alert provides the information needed to decide what happens next.
Phase 3: Remediate
Once an issue is reviewed, remediation actions can be taken directly from the alert. These actions include:
- Resolve: Mark the issue as handled. The alert moves to the resolved queue.
- Tag: Label the message as compliant, noncompliant, or questionable based on your organization’s standards. Custom tags are also supported.
- Notify: Send a warning notice to the user who triggered the alert.
- Escalate: Forward the alert to another reviewer for additional review.
- Report as misclassified: Flag false positives to improve detection and automatically resolve the alert.
- Remove message: Delete the offending message if appropriate.
- Create a case: Transfer the alert to eDiscovery for more complex investigations involving legal teams or other departments.
These actions help organizations respond proportionally to policy violations, from issuing a simple notice to launching a full investigation.
Phase 4: Maintain
Communication compliance isn't a set-it-and-forget-it solution. Policies need regular evaluation to stay effective. Use the Communication Compliance dashboard, policy health reports, and audit logs to identify gaps in coverage, excessive alerting, or areas where important activity might be missed.
Policy health insights might show when:
- Storage limits have been reached
- Users are triggering alerts but aren't scoped
- Policies are flagging too much bulk or low-value content
These signals help you refine policy conditions and scope to better focus on meaningful risks.