Identify and protect yourself from phishing
Imagine you're looking through your email and you see what looks like an alert from one of your social media accounts. Everything looks official. It asks you to sign in to your account and verify that your contact information is correct. You click the link in the email and sign in to what looks like your account.
Unfortunately, in that moment, an attacker has successfully stolen your account sign-in information.
This email-based social engineering technique is called phishing. Attackers use this technique often, sending over a billion phishing emails every year.
Let's take a closer look at phishing and how you can protect yourself to avoid becoming a victim.
What is phishing?
Phishing email is written to convince you to do one of two things:
- Click a link and go to a dangerous webpage.
- Open an attachment that runs a dangerous program.
Note
In this training, the term click a link is used to represent clicking a link with a mouse, tapping a link on a phone, or using any other type of assistive or other device to activate a link.
One of the most common phishing goals is to collect your personal information, such as your username and password. If the attacker is successful, they'll use your stolen information to access your account and any other accounts where you use that same username and password.
Another common phishing goal is to deliver malicious software, called malware. Opening one of these dangerous attachments can result in running a program that harms your computer. Such a program might even lock you out of your computer unless you pay a ransom. This malware is known as ransomware.
Phishing is one of the most common threats on the internet. In 2019 alone, the FBI's Internet Crime Complaint Center (IC3) reported more than 450,000 complaints and more than $3.5 billion in losses to individuals and businesses. This data represents only a small number of the actual cases. In other words, phishing is a popular and successful way for a criminal to steal your data.
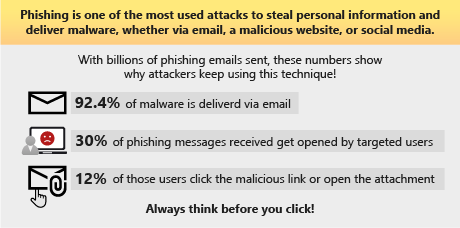
Why does phishing work so often?
Phishing is designed to be believable. Attackers have been using the same approach since the first phishing emails were sent in the 1990s. They often try to take advantage of your good nature, your desire to help, or your desire to solve a problem.
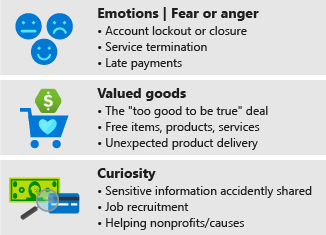
Attackers know what emotions get people to respond. For example, they might send an email to get you to click a link by telling you something needs to happen urgently. One common example is an email that says your account has been closed. Although this might seem like something serious at first, remember that most businesses won't send you an email that says they've closed your account with no warning.
Another common approach is to offer something too good to be true. Attackers will tell you that you've won an award or that they need you to manage their large sums of money.
One other common approach that attackers use is to take advantage of your curiosity. For example, they might make a fake job offer, pretend to be an old friend, or ask for help for their fake nonprofit.
What can you do to protect yourself?
First, recognize phishing! The following video has some guidance on what to look for and how to handle a possible phishing email.
Here are some common features of phishing attacks:
- Attachments: If your email has an attachment that you don't expect, it might be phishing, and that attachment might be dangerous.
- Unusual hyperlinks: Be aware of any links in emails. If you hover over a link and the destination looks odd, it might be a dangerous website. A website might look just like a legitimate one, but be designed to capture your login information or run malware.
- Urgency: If a message says you need to do something right now, it might be a phishing email. Remember, your bank usually doesn't reach out to you with no warning by using an email subject about canceling your accounts.
- Bad spelling or grammar: Phishing emails are often full of unusual writing, spelling errors, and grammar errors. If the email looks suspicious, you should avoid interacting with it.
- Fake sender: If the email address looks unusual or is someone you don't recognize, you should treat it as a phishing email.
The following example email has all of these features.

Now that you can recognize phishing email and you know not to click any links or open any attachments, let's talk about what else you can do. Your email application or website probably has the report phishing feature. Using this feature will notify the email provider and help prevent similar email in the future. Of course, you can delete phishing email too.
If you aren't sure about an email from a friend or family member, you still don't need to click any links or open any attachments. You can give them a call or send a text message and ask if they sent you anything.
You don't have to worry about all your email, but you do need to pay close attention to anything that looks unusual or suspicious. If you notice any signs of phishing, just remember not to do anything with that email other than reporting it and deleting it.