Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Starting in Configuration Manager current branch version 1702, you can enable multi-factor authentication (MFA) for Systems Management Server (SMS) Provider calls to prevent unauthorized administrative accesses.
Original product version: Configuration Manager (current branch)
Original KB number: 4042963
How to enable MFA for SMS Provider calls
Important
You must be a member of the Full Administrator role that has access to the All scope to set and change MFA setting for SMS Provider calls.
Note
You can enable MFA from any server that hosts the SMS Provider because it is a global setting.
To enable MFA, follow these steps:
Open WBEMTEST.
Connect to the Configuration Manager primary site namespace
root\sms\site_<site code>. Then, select Execute Method.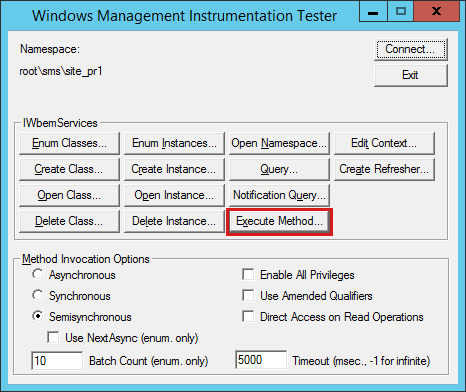
In the Object Path field, enter sms_site, and then select OK.
In Method list, select
SetAuthenticationLevel, and then select Edit In Parameters.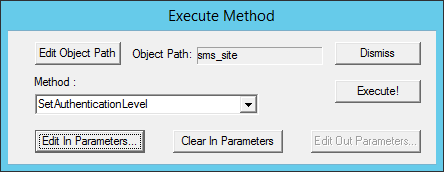
Edit the
AuthenticationLevelandExceptionListproperties, and then select Save Object.Note
Both
AuthenticationLevelandExceptionListare global properties that are used on all primary sites.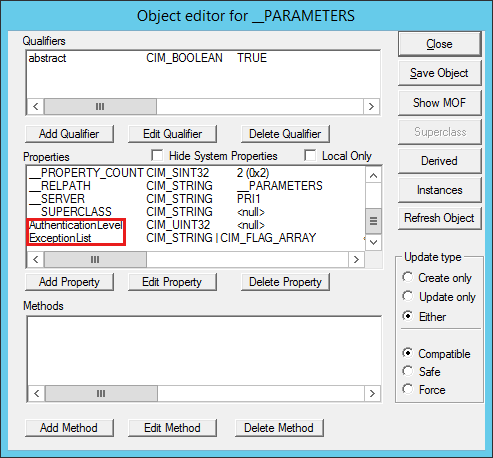
Edit the
AuthenticationLevelproperty.Refer to the following table to set the value of
AuthenticationLevel.Value Description 0 This is the default value. For this value, a second layer of authentication isn't required. Everyone can make SMS Provider calls based on their role-based access. 10 For this level, users who are logged on by using a PIN or smart card can make SMS Provider calls if they have the appropriate permissions to access the respective provider. 20 For this level, users who are logged on by using a PIN can make provider calls if they have the appropriate permissions to access the respective provider. Edit the
ExceptionListproperty.You can bypass MFA for users in the
ExceptionList, such as service accounts. Add theUserSIDorSecurityGroupSIDto theExceptionList. To determine the SIDs, see Well-Known SID Structures.Note
Users in the
ExceptionListcan't call theSetAuthenticationLevelmethod.
select Execute!, and then select Dismiss.
You can run the following SQL query to check whether MFA is enabled. If MFA is enabled, the query output shows the value of the Value3 property is 10.
select * from vSMS_SC_GlobalProperty where PropertyName='{3B1F3900-A186-11d0-BDA9-00A0C909FDD7} Authentication'
Use PowerShell cmdlets to set the AuthenticationLevel and ExceptionList properties
You can also use PowerShell cmdlets to set the AuthenticationLevel and ExceptionList properties.
Note
To get the security identifier (SID) of Active Directory users and groups, run the Get-AdUser and Get-ADGroup cmdlets.
Example 1: Set the authentication level and add two SIDs to the exception list
[array]$ExceptionList=@("S-1-5-<domain SID>-<RID of the user or group account>","S-1-5-<domain SID>-<RID of the user or group account>")
[uint32]$AuthenticationLevel=<Authentication level value>
Invoke-CimMethod -Namespace 'root\sms\site_<site code>' -ClassName 'SMS_Site' -MethodName 'SetAuthenticationLevel' -Arguments @{AuthenticationLevel=$AuthenticationLevel;ExceptionList=$ExceptionList}
Example 2: Set the authentication level to default and remove any entries from the exception list
[uint32]$AuthenticationLevel=0
Invoke-CimMethod -Namespace 'root\sms\site_<site code>' -ClassName 'SMS_Site' -MethodName 'SetAuthenticationLevel' -Arguments @{AuthenticationLevel=$AuthenticationLevel}