Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This article expains a scenario where a Windows 10 device with secure boot enabled is shown as Not Compliant in Microsoft Intune.
Symptom
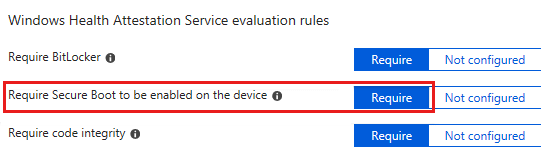
You create a compliance policy for Windows 10 devices in Intune. You set the Require Secure Boot to be enabled on the device setting to Require.
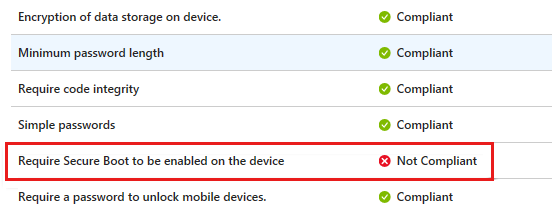
In this scenario, a Windows 10 device that meets the requirement is marked as Not Compliant.
Cause
The Require Secure Boot to be enabled on the device setting is supported on some TPM 1.2 and 2.0 devices. For devices that don't support TPM 2.0 or later, the policy status in Intune shows as Not Compliant. TPM 2.0 requires UEFI firmware. A computer with legacy BIOS and TPM 2.0 won't work as expected.
For more information about supported versions, see Supported versions for device health attestation.
For more information about how mobile device management (MDM) solutions use the Health Attestation Service, see Protect, control, and report on the security status of Windows 10-based devices.
More information
Use these steps to check whether your device meets the hardware requirements for the health attestation feature.
Check the TPM version.
Type
tpm.mscin the Run box, and then check the value in Specification Version.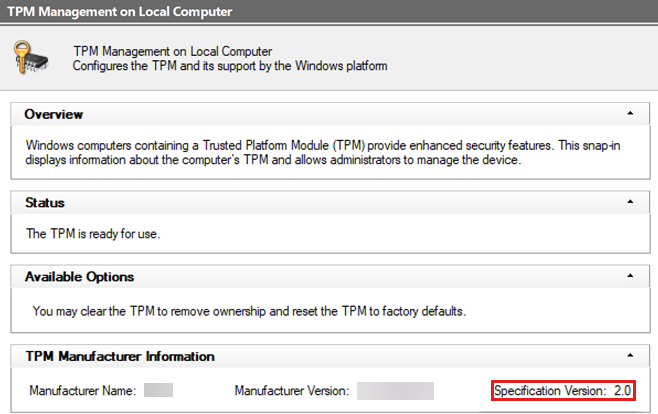
Note
If the TPM version is 1.2 and your device supports TPM 2.0, contact your device manufacturer to update to TPM 2.0.
Open an elevated command prompt, and run the
msinfo32command.In System Summary, verify that BIOS Mode is UEFI, and PCR7 Configuration is Bound.

Open an elevated PowerShell command prompt, and run the following command:
Confirm-SecureBootUEFIVerify that it returns the value of True.
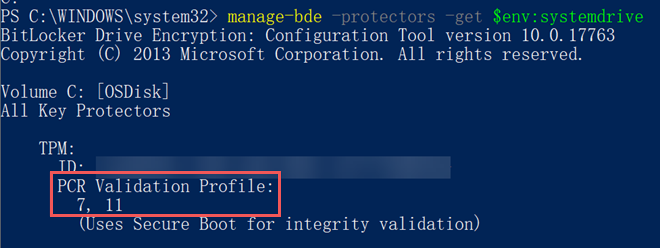
Run the following PowerShell command:
manage-bde -protectors -get $env:systemdriveVerify that the drive is protected by PCR 7.