Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
This guide provides solutions to common issues encountered when using the wrap feature in Microsoft Power Apps.
Issue 1: Wrap build fails
If your wrap build fails, try the following actions:
Verify image formats
All images in your wrap project must be in PNG format. Using other formats causes the build to fail. Use an image converter to convert images to .png.
Important
Renaming a file extension to .png doesn't convert the image to PNG format.
Check Azure key vault setup
- Ensure you create an Azure service principal and assign the correct role.
- For more information, see Create Azure key vault for wrap in Power Apps.
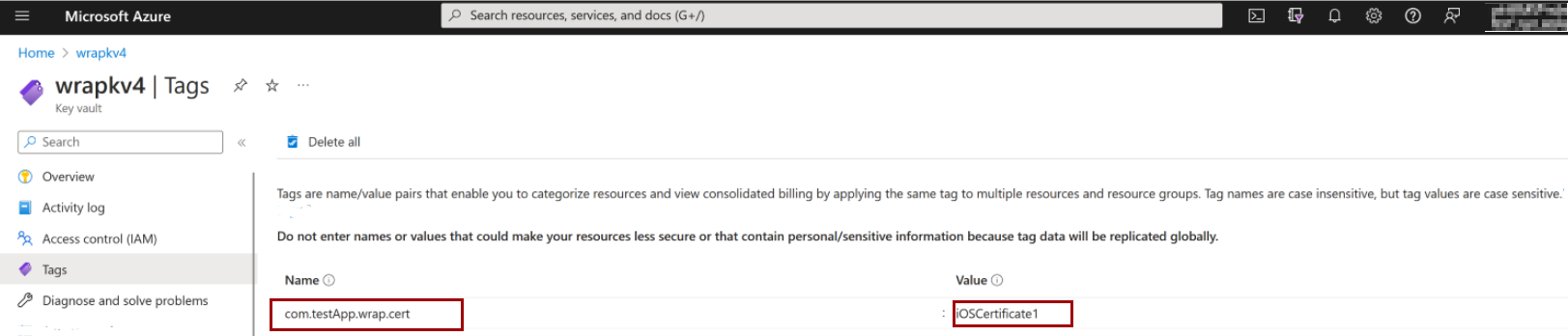
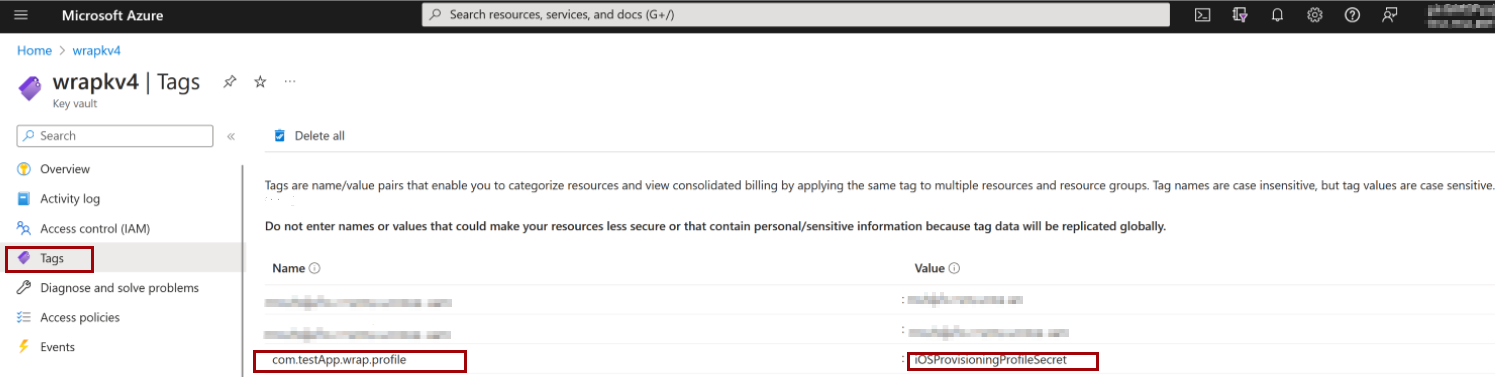
Your key vault must contain:
- For iOS: Two tags, one certificate, and one secret.
- For Android: One tag and one certificate.
Issue 2: Wrap button is disabled
You can only wrap apps if you have edit permissions. Confirm you have the correct permissions for the app and try again.
Issue 3: Unable to save your wrap project or trigger a build
Update to the latest version of the wrap solution and try again.
Issue 4: Unable to install wrapped mobile app
Ensure your app is properly signed by configuring a key vault during the build process, or signing the app manually.
For more information, see:
In addition, verify your device meets the minimum requirements.
Issue 5: Can't sign in or see data in wrapped app
If you can't sign in or see data in your wrapped app, try the following actions:
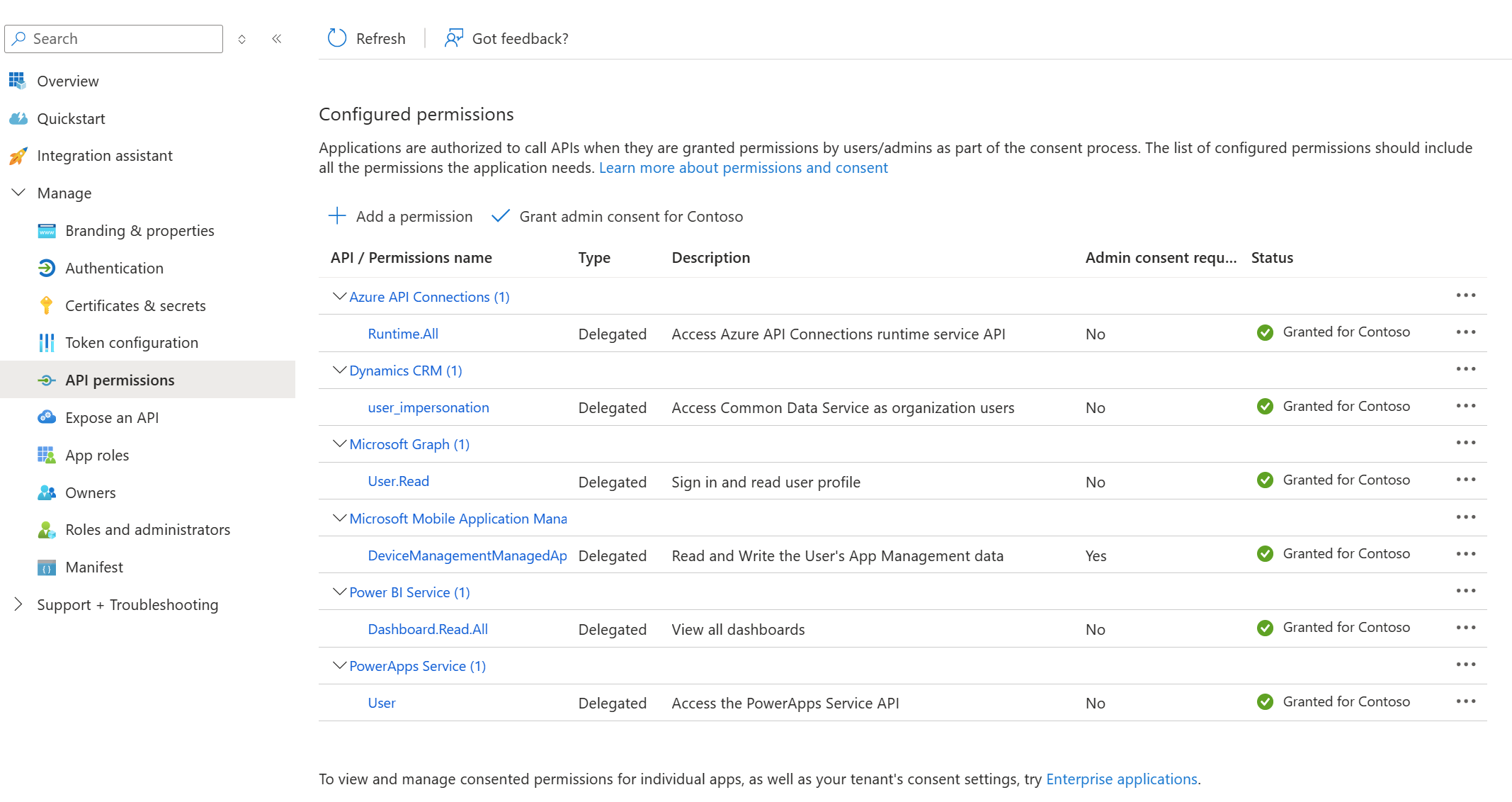
Verify API permissions and access
Ensure all required API permissions are configured and admin permissions are granted.
Ensure the
Add-AdminAllowedThirdPartyAppsscript runs successfully.
For more information, see Allow registered apps in your environment.
Check account type and redirect URIs
Verify the Microsoft Entra app type is set to Multitenant and the supported account type is Accounts in any organizational directory (Any Microsoft Entra ID tenant).
Configure proper redirect URIs for iOS and Android:
- For Android, confirm the hash is correct.
- For more information, see Configure platform settings and redirect URIs.
Issue 6: Azure key vault errors in wrap for Power Apps
You might encounter these error codes in the wrap wizard:
| Error code | Error message |
|---|---|
| 1000118 | Default subscription not found or missing access permissions. |
| 1000119 | Key vault doesn't exist or is missing access privileges. |
| 1000120 | No organization ID tags found on key vault. Ensure that the tag {Bundle ID}.{organization-id} is present and uses the correct case sensitivity. |
| 1000121 | Android keystore isn't valid. Ensure that the tag {Bundle ID}.{keystore} is present and uses the correct case sensitivity. |
| 1000122 | iOS certificate isn't valid. Missing Tag and/or Secret. Ensure that the tag {Bundle ID}.{cert} is present and uses the correct case sensitivity. |
| 1000123 | iOS profile isn't valid. Ensure that the tag {Bundle ID}.{profile} is present and uses the correct case sensitivity. |
| 1000128 | Missing access key required to access the Azure Blob Storage location. Ensure that the tag {Bundle ID}.{accessKey} is present and uses the correct case sensitivity. |
| 1000130 | Missing default value: The required environment variable for setting up Azure Key Vault in the wrap wizard isn't set. |
| 1000131 | No tags or missing access permission for the specified Azure Key Vault. |
| 1000132 | Missing environment variable 'PA_Wrap_KV_ResourceID' for the targeted environment. |
Error code 1000118
Erroe message: Default subscription not found, or missing access permissions.
Resolution steps
Ensure your Azure key vault is in the tenant's Default subscription.
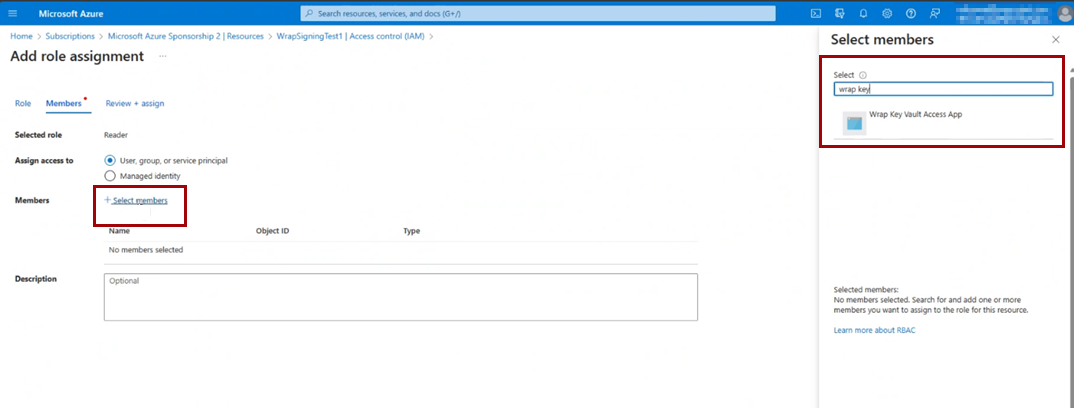
As a Microsoft Entra ID (formerly Azure AD) admin, add the service principal for the AppID "4e1f8dc5-5a42-45ce-a096-700fa485ba20" by running the following commands in PowerShell:
Connect-AzureAD -TenantId <your tenant ID> New-AzureADServicePrincipal -AppId 4e1f8dc5-5a42-45ce-a096-700fa485ba20 -DisplayName "Wrap KeyVault Access App"In the Azure portal, under Access Control (IAM), assign the Reader role to your service principal:
Error code 1000119
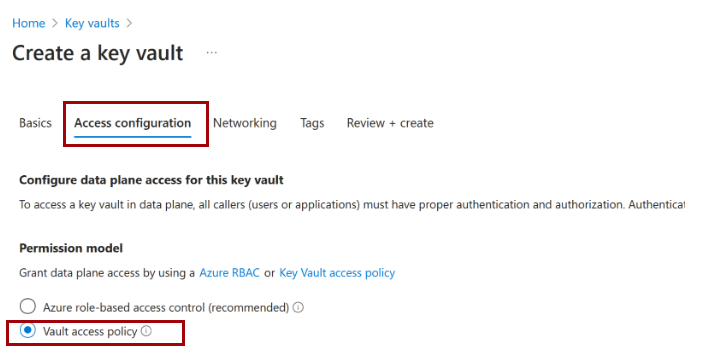
Error message: Key vault doesn't exist, or Key vault is missing access privileges.
Resolution steps
Confirm your Azure key vault is in the tenant's Default subscription.
While creating the key vault, select Vault access policy.
As a Microsoft Entra ID (formerly Azure AD) admin, add the service principal for the AppID "4e1f8dc5-5a42-45ce-a096-700fa485ba20" by running the following commands in PowerShell:
Connect-AzureAD -TenantId <your tenant ID> New-AzureADServicePrincipal -AppId 4e1f8dc5-5a42-45ce-a096-700fa485ba20 -DisplayName "Wrap KeyVault Access App"In the Azure portal, assign the Reader role as shown in the previous error code section.
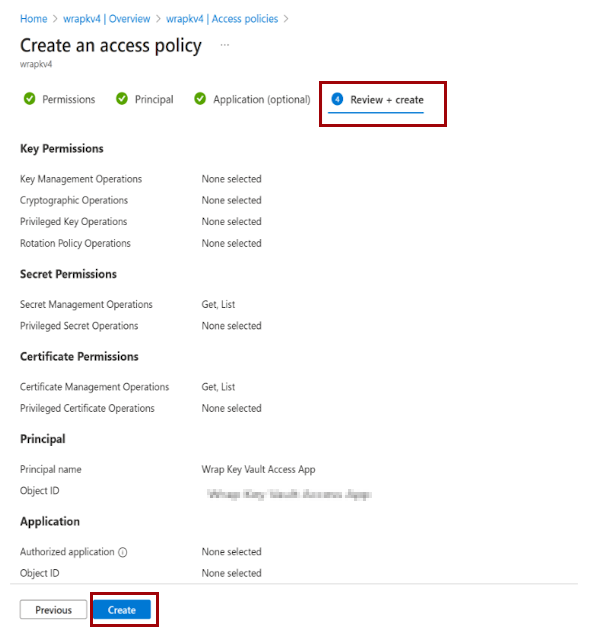
Add access policies to the key vault:

Error code 1000120
Error message: No organization ID tags found on key vault. Ensure that the tag {Bundle ID}.{organization-id} is present and uses the correct case sensitivity.
Resolution steps
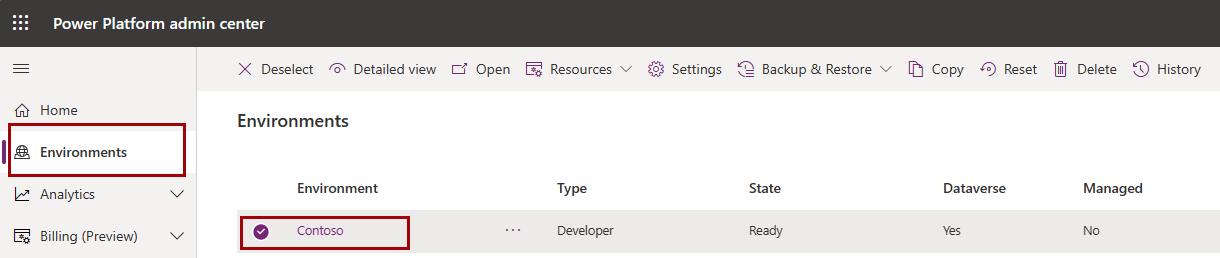
In the Power Platform admin center, select your environment.
Copy the Organization ID.
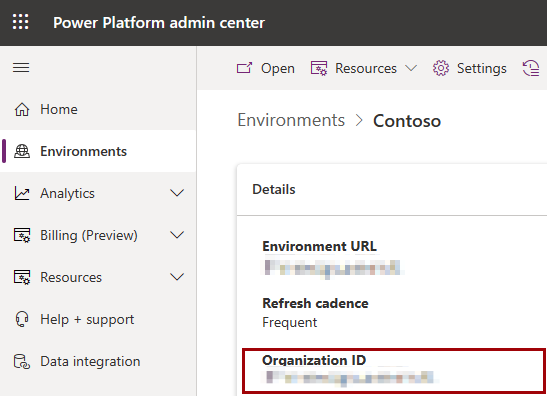
In your key vault, go to Tags and create a tag named organization-id with your organization ID as the value.
Error code 1000121
Error message: Android keystore isn't valid. Ensure that the tag {Bundle ID}.{keystore} is present and uses the correct case sensitivity.
Resolution steps
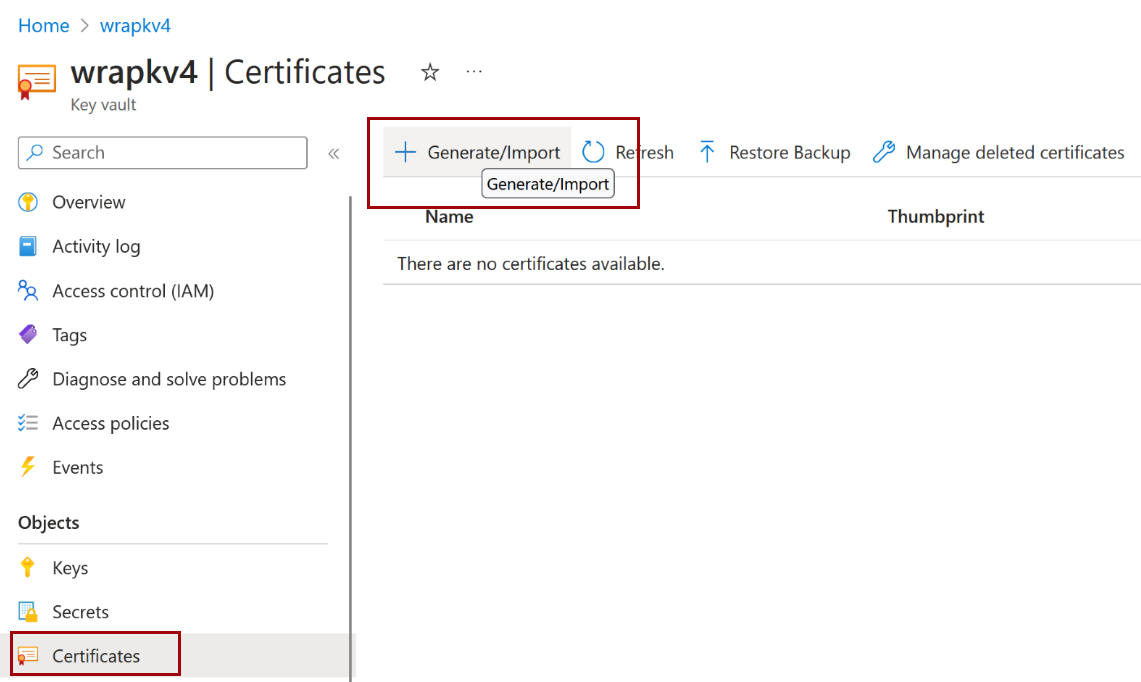
Import your Android Certificate.
Add a Tag for your certificate:
- Tag name: Use the same Bundle ID as your wrap project (for example,
com.testApp.wrap). - Tag value: Use the certificate name you assigned when uploading (for example,
AndroidCertificate).
- Tag name: Use the same Bundle ID as your wrap project (for example,
Error code 1000122
Error message: iOS certificate isn't valid. Missing Tag and/or Secret. Ensure that the tag {Bundle ID}.{cert} is present and uses the correct case sensitivity.
Resolution steps
Import your iOS Certificate.
Add a Tag for your certificate:
- Tag name: Use the Bundle ID from your wrap project.
- Tag value: Use the certificate name you assigned when uploading (for example,
iOSCertificate).
Error code 1000123
Error message: iOS profile isn't valid. Ensure that the tag {Bundle ID}.{profile} is present and uses the correct case sensitivity.
Resolution steps
Import your Provisioning Profile as a Secret.
Add a Tag for your provisioning profile:
- Tag name: Use the Bundle ID from your wrap project.
- Tag value: Use the name you gave the secret when uploading (for example,
iOSProvisioningProfile).
Error code 1000128
Error message: Missing access key required to access the Azure Blob Storage location. Ensure that the tag {Bundle ID}.{accessKey} is present and uses the correct case sensitivity.
Resolution steps
Add your access key from the Azure Blob storage account to the Azure key vault.
For more information, see Step 2: Target platform.
Error code 1000130
Error message: Missing default value: The required environment variable for setting up Azure Key Vault in the wrap wizard isn't set.
Resolution steps
Assign the resource ID of the Azure key vault you intend to use with your wrap application to the variable.
Confirm that the specified resource ID includes all required tags associated with the Bundle ID defined in the wrap wizard.
For more information, see Step 2: Target platform.
Error code 1000131
Error message: No tags or missing access permission for the specified Azure Key Vault.
Resolution steps
Assign the resource ID of the Azure key vault you intend to use with your wrap application to the variable.
Confirm that the specified resource ID includes all required tags associated with the Bundle ID defined in the wrap wizard.
Ensure you have permission to access your key vault:
As a Microsoft Entra ID (formerly Azure AD) admin, add the service principal for the AppID "4e1f8dc5-5a42-45ce-a096-700fa485ba20" by running the following commands in PowerShell:
Connect-AzureAD -TenantId <your tenant ID> New-AzureADServicePrincipal -AppId 4e1f8dc5-5a42-45ce-a096-700fa485ba20 -DisplayName "Wrap KeyVault Access App"In the Azure portal, under Access Control (IAM), assign the Reader role to your service principal:
For more information, see Step 2: Target platform.
Error code 1000132
Error message: Missing environment variable 'PA_Wrap_KV_ResourceID' for the targeted environment.
Resolution steps
Check whether the environment variable
PA_Wrap_KV_ResourceIDexists in the target environment. If it doesn't, create it.Ensure the name follows the correct naming convention without typos or formatting errors.
For more information, see Step 2: Target platform.
Issue 7: Fail to sign in to wrapped app
Ensure the user has access to the app. For more information, see Share a canvas app with your organization.
If the user has app access but still can't sign in, check the conditional Access policies in Microsoft Entra admin center.
Use the correlation ID from the failed sign-in screen for further troubleshooting.
Issue 8: Error message: "Something went wrong. [5objp]"
This issue might occur due to a Signature Hash Key mismatch or a Redirect URI mismatch during the app authentication process.
Common root causes
Cause 1: Signature Hash Key mismatch
The APK is signed with a different key than the one registered in the Microsoft Entra ID application. This might occur if:
A different keystore is used during the build process.
The registered hash key is incorrectly generated or copied (for example, it includes extra spaces or invalid characters.)
Cause 2: Redirect URI mismatch
The redirect URI being used by the app doesn't match what's registered in the portal:
Redirect URIs are case-sensitive. Mismatches might occur if the Bundle ID or URI is entered with incorrect casing.
Special characters in the URI (such as
%2F,%3D) must be properly encoded and match exactly what is registered in Microsoft Entra ID.
How to fix the issue
Verify the Signature Hash Key
Generate the correct hash key from the keystore used to sign the app.
In the Microsoft Entra admin center, go to App registrations and select your app.
In the app's navigation pane, select Authentication.
Under the Platform configurations section, locate the Android platform.
Check that your app's Signature Hash Key is listed and matches the hash key generated from your keystore.
If the hash key is missing or incorrect, add or update it as needed, and then save your changes.
Check the Redirect URI
Install Android Studio and set up an emulator.
Launch the emulator and drag the APK file onto it to install the app.
Open the app in the emulator, attempt to sign in, and note the error message.
On the error screen, locate the redirect URI being used.
If the hash key in the URI contains encoded characters (for example,
%2F), decode them (%2Fbecomes/) to get the Signature Hash Key.Copy the decoded Signature Hash Key.
In the Microsoft Entra admin center, go to App registrations and select your app.
Under Authentication, review the configured redirect URIs.
If the redirect URI is missing, add it with the correct Bundle ID and Signature Hash Key, and then save your changes.
Compare the existing redirect URI character-by-character (including case and encoding) with the one registered in Microsoft Entra ID.
If manually entering the Bundle ID in the portal, double-check for case consistency.
Recommended practices
To avoid this error in the future:
- Always copy the Bundle ID and hash key directly from the project or build output.
- Use logging or emulator logs to inspect the exact redirect URI at runtime.
- Avoid manually typing or modifying hash keys or redirect URIs.
- Use Android Studio to verify your app configuration.
Issue 9: Error message "Something went wrong [2002]" and error code 9n155
The error might occur when the app registration isn't configured to support multitenant accounts.
Common root causes
This error typically occurs when the app registration is created using the wrap wizard, which by default sets the app to single-tenant mode. If the user doesn't manually update this setting or accidentally selects single tenant during manual app registration, wrap app is unable to authenticate, resulting in error code 9n155.
Resolution
In the Microsoft Entra admin center, go to App registrations and select your app.
In the Essentials section, locate Supported account types. It should be set to Multiple organizations. If not, set it to Accounts in any organizational directory (Any Microsoft Entra directory - Multitenant).
Save your changes.
Other issues
If your issue isn't covered here, or if the preceding steps don't resolve your problem, see Next steps to report your issue. Be prepared to provide detailed steps to reproduce the problem.
Collecting diagnostic information
For troubleshooting sign-in issues, you can collect session details:
- For wrap wizard: On the sign-in screen, tap the gear icon in the upper-right corner and select Session Details.
- For mobile devices: After opening the app, press and hold the screen, and then select Session Details.
Next steps
If your issue still persists, search for more support resources or contact Microsoft support.