Troubleshoot domain controller location issues in Windows
This article helps troubleshoot domain controller location issues in Windows.
Domain controller (DC) location, also known as DC Locator, refers to the algorithm the client machine uses to find a suitable domain controller. DC Locator is a critical baseline functionality in all enterprise environments. For more information about how domain controllers are located in Windows, see Locating domain controllers in Windows and Windows Server.
If DC Locator doesn't work as expected in Active Directory domains, troubleshoot issues by using the following steps:
Note
Authentication is the first step in almost all functional scenarios in an Active Directory enterprise environment. However, authentication occurs after the client communicates with an Active Directory domain controller.
Check the system logs (for example, the event source is NETLOGON) on both the client and the server. Also check the Directory Service logs (for example, the event source is NTDS KCC) on the server and Domain Name System (DNS) logs on the DNS server.
Open an elevated command prompt, and check the IP configuration by running the following command:
ipconfig /allUse the Ping utility to verify network connectivity and the name resolution. Ping the IP address, the server name, and the domain name.
Use the PortQryUI tool to probe for availability of important domain controller services. When you start the tool, specify the domain controller fully qualified domain name (FQDN), and query the Domains and Trusts set of services as follows:
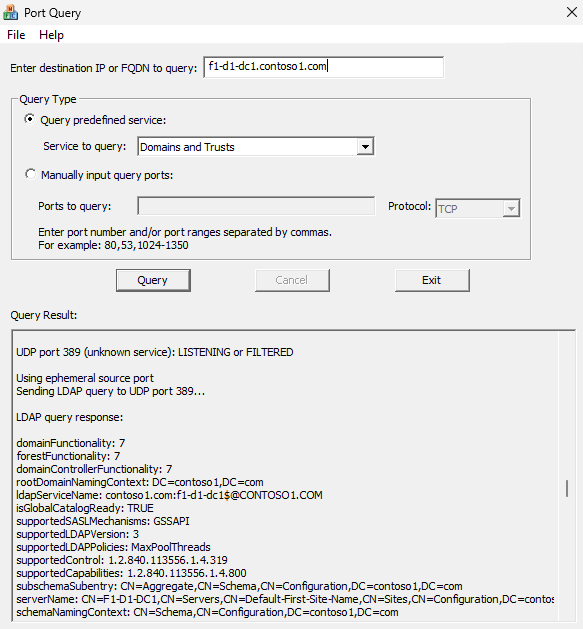
The screenshot shows one important port for DC discovery which is UDP/389, and in this case, it is successful.
Note
UDP/389: This port is required to discover AD services.
Use the
nslookuptool to verify that DNS entries are correctly registered in DNS. Verify that the server host records and the globally unique identifier (GUID) SRV records can be resolved.For example, to verify record registrations, run the following commands:
nslookup servername.childofrootdomain.rootdomain.comnslookup guid._msdcs.rootdomain.comIf either of these commands doesn't succeed, use one of the following methods to reregister records with DNS:
- To force the host record registration, use the
ipconfig /registerdnscommand. - To force the domain controller service registration, stop and restart the Netlogon service.
- To detect domain controller issues, run the DCdiag utility from a command prompt. The utility runs many tests to verify that a domain controller is running correctly. Use the
dcdiag /v >dcdiag.txtcommand to send the results to a text file.
- To force the host record registration, use the
Use the Ldp.exe tool to connect and bind to the domain controller to verify appropriate Lightweight Directory Access Protocol (LDAP) connectivity.
If you suspect that a particular domain controller has issues, turn on Netlogon debug logging. Use the Nltest tool by running the
nltest /dbflag:0x2000ffffcommand. The information is then logged in the Netlogon.log file under the %windir%\Debug folder.If you still haven't isolated the issue, use network monitor tools like Wireshark to capture and analyze network traffic between the client and the domain controller.