Authenticated Key Exchange
This section applies only to Windows Server 2003 SP1 and later, and Windows XP SP2 and later.
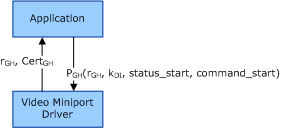
The following figure shows establishing a secure connection through authentication and key exchange. First, the video miniport driver supplies the graphics hardware certificate to the application. Next, the application extracts the public key from the graphics hardware certificate. After the application generates a data integrity key (kDI), the application uses the public key to encrypt a sequence that includes the data integrity key and supplies the sequence to the driver.
Command and status messages are subsequently passed unencrypted; however, for each message, MACs are created by using the data integrity key.
For more information about MACs, see Cryptographic Primitives Used by COPP.
The following table describes the values in the preceding figure.
| Value | Description |
|---|---|
rGH |
128-bit random number generated by the driver. |
CertGH |
Variable-length digital certificate used by the graphics hardware. |
PGH(rGH, kDI, status_start, command_start) |
Start sequence for the secure channel, which consists of the following items concatenated together:
The application encrypts the sequence by using the public key obtained from the graphic hardware certificate. The sequence is 2,048 bits long; the remainder of the sequence is padded with 0s. |