Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Learn how to use the LAPS properties dialog in the Windows Server Active Directory Users and Computers management snap-in to configure Windows Local Administrator Password Solution (Windows LAPS) for Windows Server Active Directory.
Windows LAPS snap-in availability
The Windows LAPS-enabled Active Directory Users and Computers management snap-in is available on Windows Server platforms that have been patched with the Windows LAPS feature. The Active Directory Users and Computers management snap-in must be installed, either as part of the larger Active Directory Domain Services role, or as part of the AD DS Snap-in and Command-Line Tools individual feature.
One way to install the AD DS Snap-Ins and Command-Line Tools feature is from the command line as follows:
dism.exe /online /enable-feature:DirectoryServices-DomainController-Tools /all
The Windows LAPS-enabled Active Directory Users and Computers management snap-in is available on supported Windows Client platforms that have been patched with the Windows LAPS feature, via Remote Server Administration Tools (RSAT). You may add RSAT on client platforms by going to Settings, then System (or Apps if on a version older than Windows 10 22H2), then Optional Features, and then add RSAT (specifically search for and add "RSAT: Active Directory Domain Services and Lightweight Directory Services Tools").
The Windows LAPS-enabled Active Directory Users and Computers management snap-in isn't available on older platforms that don't support Windows LAPS. The older Remote Server Administration tools package is not updated to support the new snap-in.
LAPS properties dialog in the management snap-in
The Windows Server Active Directory Users and Computers management snap-in includes a LAPS properties dialog that's available for computer objects:
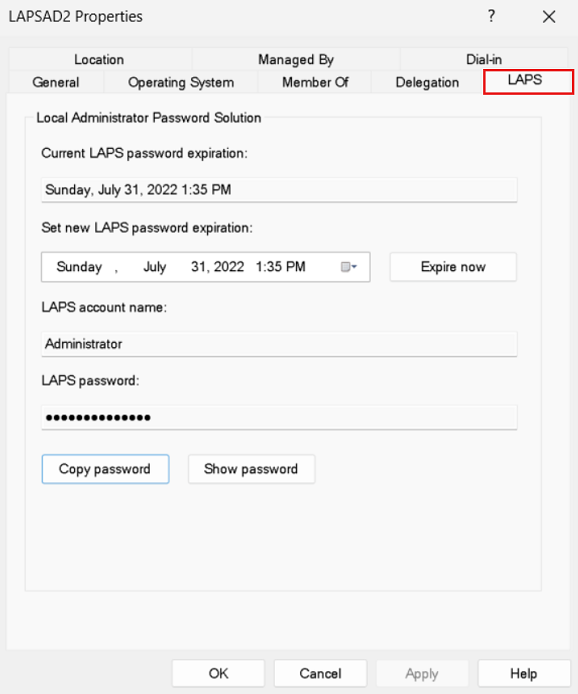
You can use the properties dialog to complete the following actions:
- View the current password expiration time.
- Modify the password expiration time.
- Expire the password expiration time.
- View the current account name and password.
Important
The LAPS properties dialog doesn't support viewing legacy Microsoft LAPS passwords or password expiration times.
View the current password expiration time
When you first go to the properties dialog for a Windows Server Active Directory computer, the date-time control displays the current password expiration time. For example:
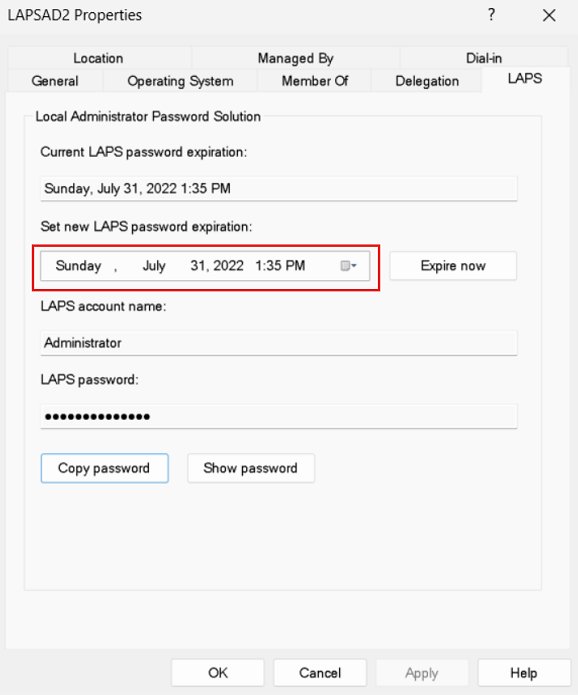
Modify the password expiration time
You can use the date-time control to modify the password expiration time. For example:

If you modify the date or time, select Apply, and then select OK.
Manually expire the password
To immediately expire the password, select Expire now:
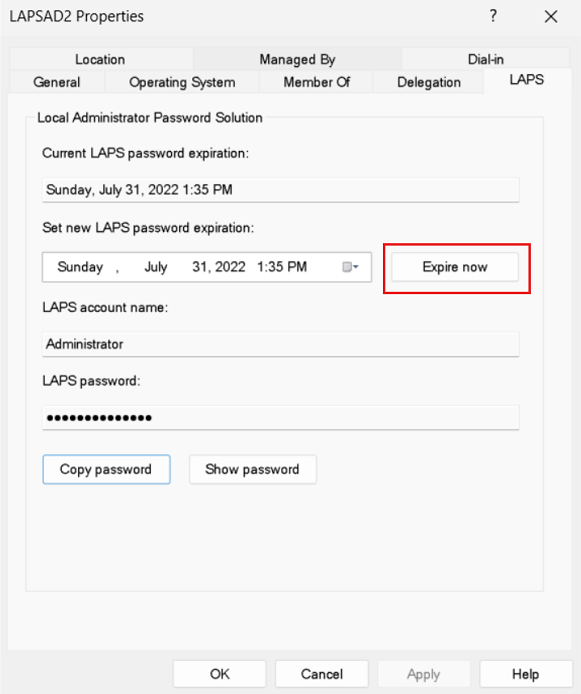
Select Apply, and then select OK.
View the current account name and password
If you have permissions to read and decrypt the computer's current Windows LAPS password attribute, Account Name and Password have your username and password. Select Copy password to copy the password to the clipboard. Select Show password to show the password.
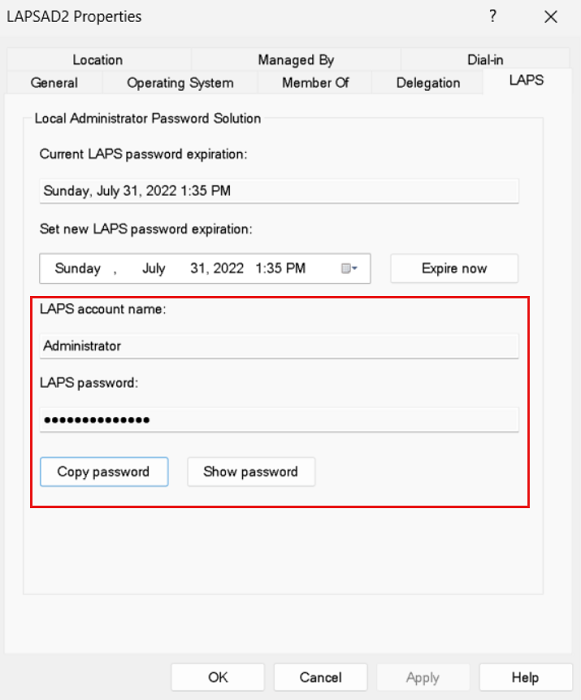
If you don't have permissions to read or decrypt the current password information, a dialog displays a warning.
Important
The Active Directory Users and Computers management snap-in only supports viewing the most recently stored password. In order to query older passwords (assuming you enabled password history), you must use the Get-LapsADPassword PowerShell cmdlet.