Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
In an enterprise organization, IT administrators enforce policies on their corporate devices to keep the devices in a compliant state and protect the OS by preventing users from changing configurations and creating config drift. Config drift occurs when users with local admin rights change settings and put the device out of sync with security policies. Devices in a noncompliant state can be vulnerable until the next sync and configuration reset with the MDM. Windows 11 with config lock enables IT administrators to prevent config drift and keep the OS configuration in the desired state. With config lock, the OS monitors the registry keys that configure each feature and when it detects a drift, reverts to the IT-desired state in seconds.
Secured-core configuration lock (config lock) is a new secured-core PC (SCPC) feature that prevents configuration drift from secured-core PC features caused by unintentional misconfiguration. In short, it ensures a device intended to be a secured-core PC remains a secured-core PC.
To summarize, config lock:
- Enables IT to "lock" secured-core PC features when managed through MDM
- Detects drift remediates within seconds
- Doesn't prevent malicious attacks
Windows edition and licensing requirements
The following table lists the Windows editions that support Secured-core configuration lock:
| Windows Pro | Windows Enterprise | Windows Pro Education/SE | Windows Education |
|---|---|---|---|
| Yes | Yes | Yes | Yes |
Secured-core configuration lock license entitlements are granted by the following licenses:
| Windows Pro/Pro Education/SE | Windows Enterprise E3 | Windows Enterprise E5 | Windows Education A3 | Windows Education A5 |
|---|---|---|---|---|
| Yes | Yes | Yes | Yes | Yes |
For more information about Windows licensing, see Windows licensing overview.
Configuration Flow
After a secured-core PCs reaches the desktop, config lock will prevent configuration drift by detecting if the device is a secured-core PC or not. When the device isn't a secured-core PC, the lock doesn't apply. If the device is a secured-core PC, config lock locks the policies listed under List of locked policies.
Enabling config lock using Microsoft Intune
Config lock isn't enabled by default, or turned on by the OS during boot. Rather, you need to turn it on.
The steps to turn on config lock using Microsoft Intune are as follows:
Ensure that the device to turn on config lock is enrolled in Microsoft Intune.
In the Intune admin center, select Devices > Configuration Profiles > Create a profile.
Select the following and press Create:
- Platform:
Windows 10 and later - Profile type:
Templates - Template name: Custom
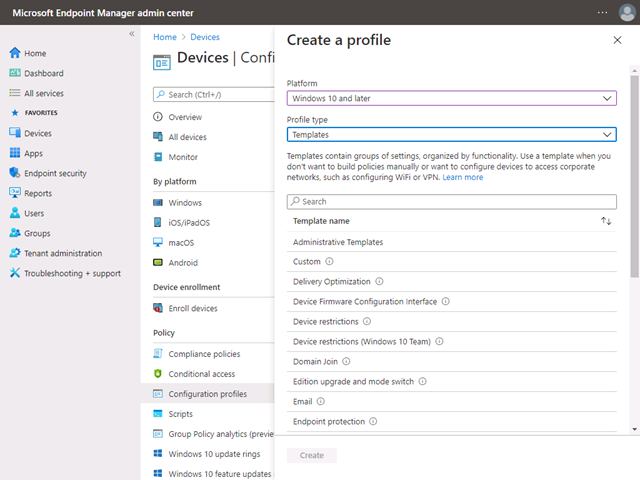
- Platform:
Name your profile.
When you reach the Configuration Settings step, select "Add" and add the following information:
- OMA-URI:
./Vendor/MSFT/DMClient/Provider/MS%20DM%20Server/ConfigLock/Lock - Data type:
Integer - Value:
1
To turn off config lock, change the value to 0.

- OMA-URI:
Select the devices to turn on config lock. If you're using a test tenant, you can select "+ Add all devices".
You don't need to set any applicability rules for test purposes.
Review the Configuration and select "Create" if everything is correct.
After the device syncs with the Microsoft Intune server, you can confirm if the config lock was successfully enabled.
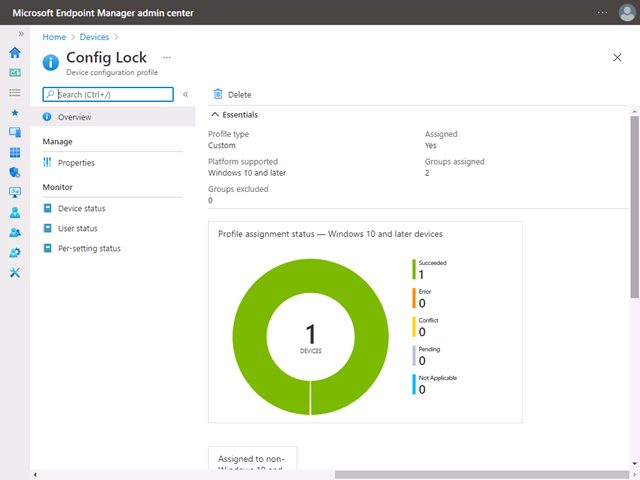
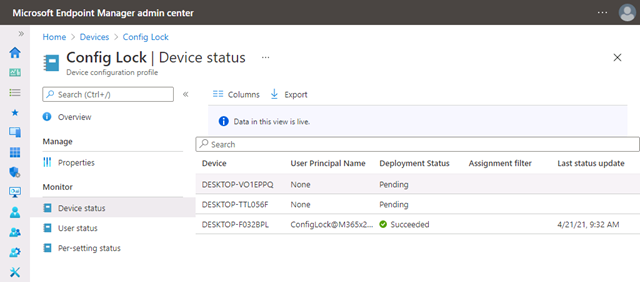
Configuring secured-core PC features
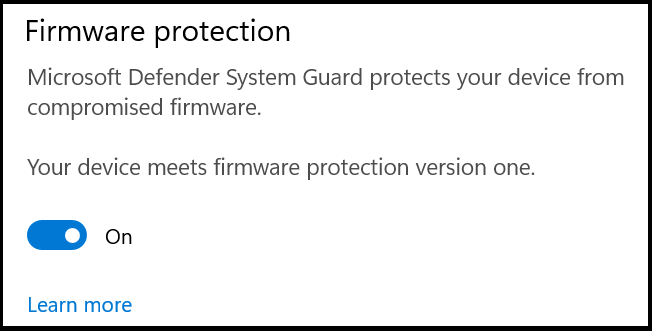
Config lock is designed to ensure that a secured-core PC isn't unintentionally misconfigured. You keep the ability to enable or disable SCPC features, for example, firmware protection. You can make these changes with group policies or MDM services like Microsoft Intune.
FAQ
- Can I disable config lock? Yes. You can use MDM to turn off config lock completely or put it in temporary unlock mode for helpdesk activities.
List of locked policies
| CSPs |
|---|
| BitLocker |
| PassportForWork |
| WindowsDefenderApplicationGuard |
| ApplicationControl |