Device registration overview
Windows Autopatch must register your existing devices into its service to manage update deployments on your behalf.
The Windows Autopatch device registration process is transparent for end-users because it doesn't require devices to be reset.
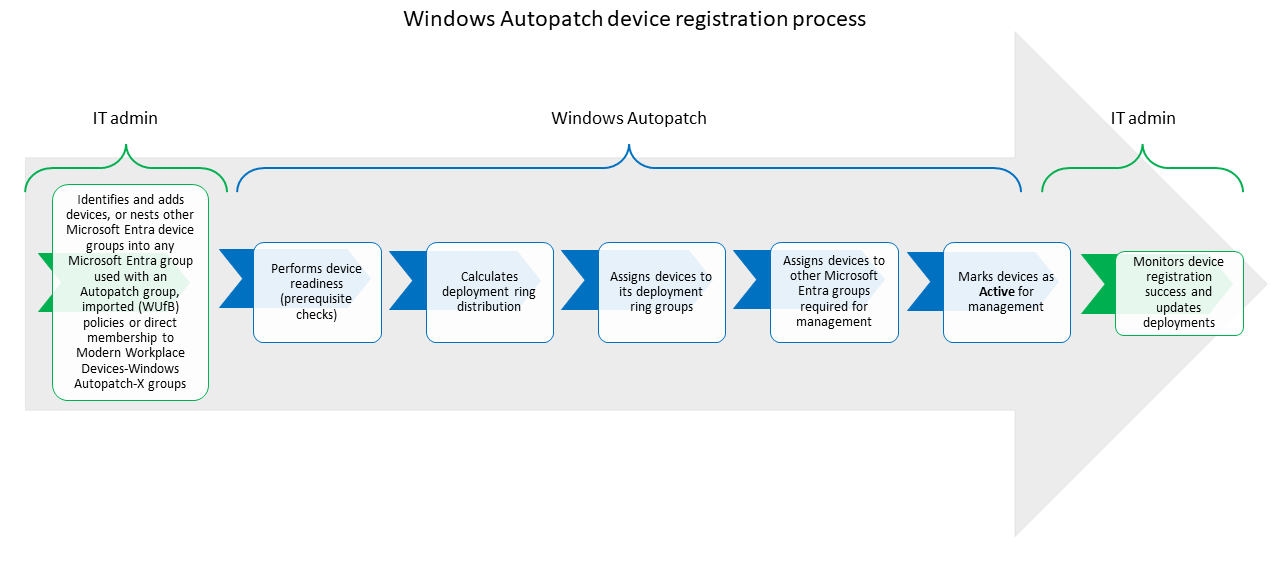
The overall device registration process is as follows:
- IT admin reviews Windows Autopatch device registration prerequisites before registering devices with Windows Autopatch.
- IT admin identifies devices to be managed by Windows Autopatch through either adding device-based Microsoft Entra groups as part of the Custom Autopatch group or the Default Autopatch group.
- Windows Autopatch then:
- Performs device readiness prior registration (prerequisite checks).
- Calculates the deployment ring distribution.
- Assigns devices to one of the deployment rings based on the previous calculation.
- Assigns devices to other Microsoft Entra groups required for management.
- Marks devices as active for management so it can apply its update deployment policies.
- IT admin then monitors the device registration trends and the update deployment reports.
For more information about the device registration workflow, see the Detailed device registration workflow diagram section for more technical details behind the Windows Autopatch device registration process.
Detailed device registration workflow diagram
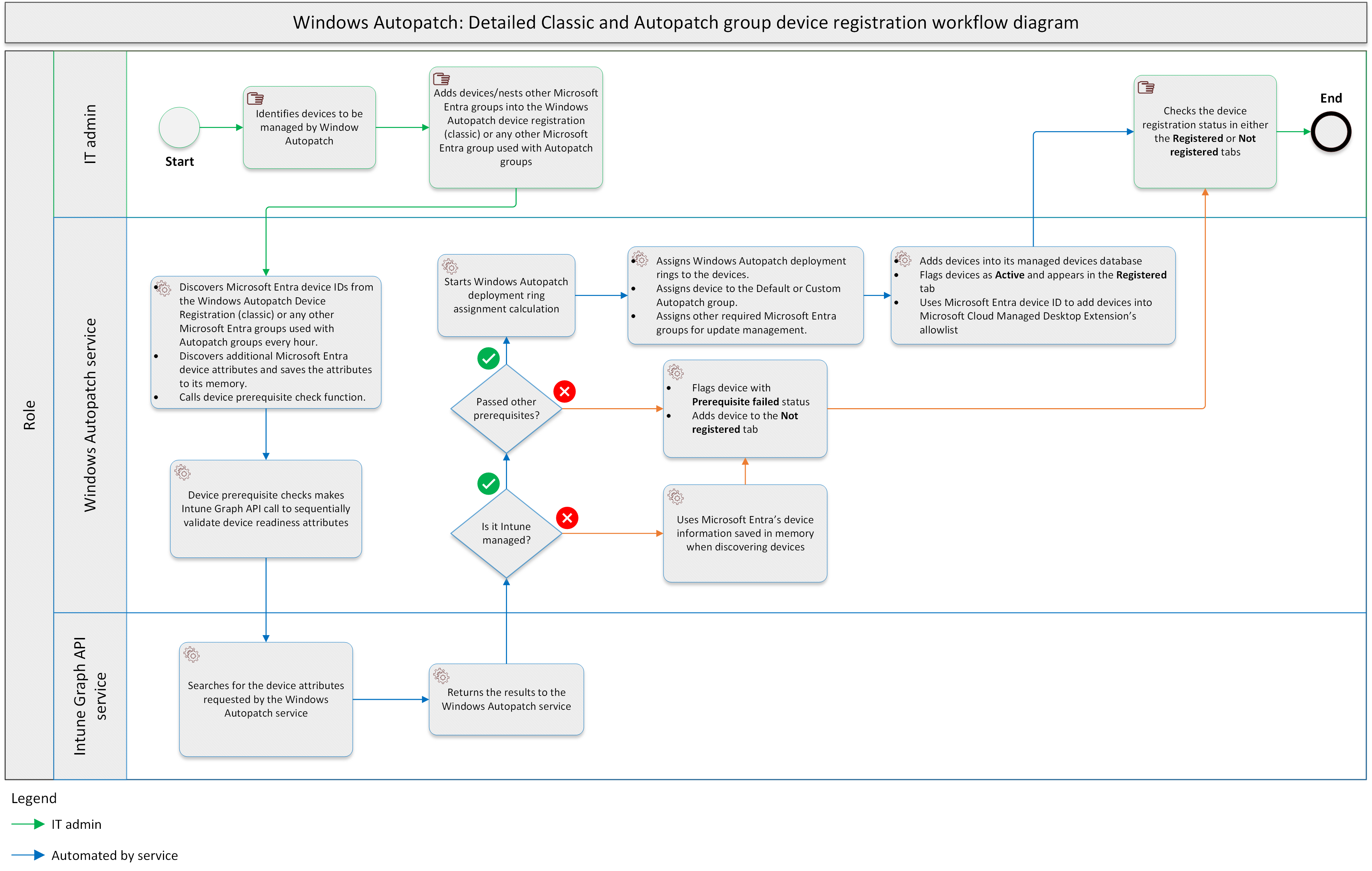
See the following detailed workflow diagram. The diagram covers the Windows Autopatch device registration process:
| Step | Description |
|---|---|
| Step 1: Identify devices | IT admin identifies devices to be managed by the Windows Autopatch service. |
| Step 2: Add devices | IT admin adds devices through Direct membership or nests other Microsoft Entra ID assigned or dynamic groups into the Windows Autopatch Device Registration Microsoft Entra ID assigned group when using adding existing device-based Microsoft Entra groups while creating/editing Custom Autopatch groups, or editing the Default Autopatch group |
| Step 3: Discover devices | The Windows Autopatch Discover Devices function discovers devices (hourly) that were previously added by the IT admin into the Windows Autopatch Device Registration Microsoft Entra ID assigned group or from Microsoft Entra groups used with Autopatch groups in step #2. The Microsoft Entra device ID is used by Windows Autopatch to query device attributes in both Microsoft Intune and Microsoft Entra ID when registering devices into its service.
|
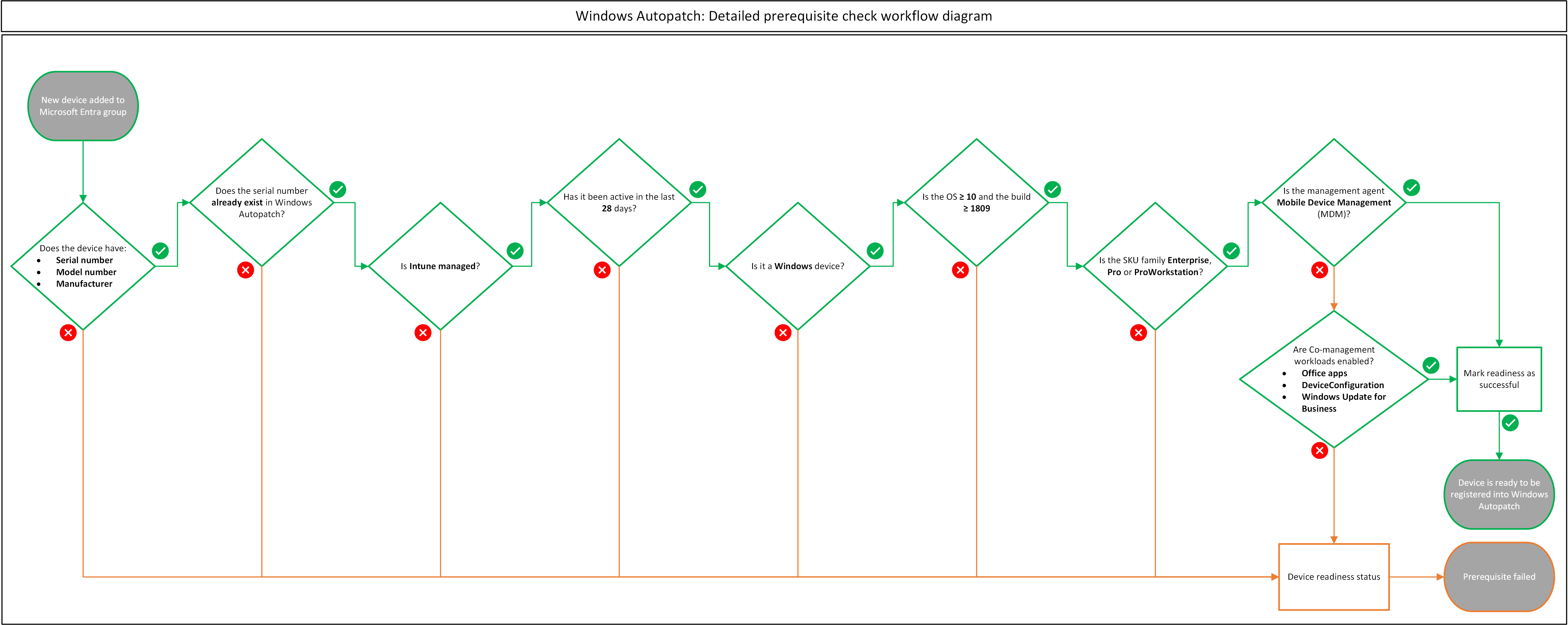
| Step 4: Check prerequisites | The Windows Autopatch prerequisite function makes an Intune Graph API call to sequentially validate device readiness attributes required for the registration process. For detailed information, see the Detailed prerequisite check workflow diagram section. The service checks the following device readiness attributes, and/or prerequisites:
|
| Step 5: Calculate deployment ring assignment | Once the device passes all prerequisites described in step #4, Windows Autopatch starts its deployment ring assignment calculation. The following logic is used to calculate the Windows Autopatch deployment ring assignment:
|
| Step 6: Assign devices to a deployment ring group | Once the deployment ring calculation is done, Windows Autopatch assigns devices to two deployment ring sets, the first one being the service-based deployment ring set represented by the following Microsoft Entra groups:
|
| Step 7: Assign devices to a Microsoft Entra group | Windows Autopatch also assigns devices to the following Microsoft Entra groups when certain conditions apply:
|
| Step 8: Post-device registration | In post-device registration, three actions occur:
|
| Step 9: Review device registration status | IT admins review the device registration status in both the Registered and Not registered tabs.
|
| Step 10: End of registration workflow | This is the end of the Windows Autopatch device registration workflow. |
Detailed prerequisite check workflow diagram
As described in step #4 in the previous Detailed device registration workflow diagram, the following diagram is a visual representation of the prerequisite construct for the Windows Autopatch device registration process. The prerequisite checks are sequentially performed.
Windows Autopatch deployment rings
During the tenant enrollment process, Windows Autopatch creates two different deployment ring sets:
The following four Microsoft Entra ID assigned groups are used to organize devices for the service-based deployment ring set:
| Service-based deployment ring | Description |
|---|---|
| Modern Workplace Devices-Windows Autopatch-Test | Deployment ring for testing service-based configuration, app deployments prior production rollout |
| Modern Workplace Devices-Windows Autopatch-First | First production deployment ring for early adopters. |
| Modern Workplace Devices-Windows Autopatch-Fast | Fast deployment ring for quick rollout and adoption |
| Modern Workplace Devices-Windows Autopatch-Broad | Final deployment ring for broad rollout into the organization |
The five Microsoft Entra ID assigned groups that are used to organize devices for the software update-based deployment ring set within the Default Autopatch group:
| Software updates-based deployment ring | Description |
|---|---|
| Windows Autopatch - Test | Deployment ring for testing software updates-based deployments prior production rollout. |
| Windows Autopatch - Ring1 | First production deployment ring for early adopters. |
| Windows Autopatch - Ring2 | Fast deployment ring for quick rollout and adoption. |
| Windows Autopatch - Ring3 | Final deployment ring for broad rollout into the organization. |
| Windows Autopatch - Last | Optional deployment ring for specialized devices or VIP/executives that must receive software update deployments after it's well tested with early and general populations in an organization. |
In the software-based deployment ring set, each deployment ring has a different set of update deployment policies to control the updates rollout.
Caution
Adding or importing devices directly into any of these groups isn't supported. Doing so might affect the Windows Autopatch service. To move devices between these groups, see Moving devices in between deployment rings.
Important
Windows Autopatch device registration doesn't assign devices to the Test deployment rings of either the service-based (Modern Workplace Devices-Windows Autopatch-Test), or software updates-based (Windows Autopatch - Test and Windows Autopatch - Last) in the Default Autopatch group. This is intended to prevent devices that are essential to a business from being affected or devices that are used by executives from receiving early software update deployments.
During the device registration process, Windows Autopatch assigns each device to a service-based and software-update based deployment ring so that the service has the proper representation of device diversity across your organization.
The deployment ring distribution is designed to release software update deployments to as few devices as possible to get the signals needed to make a quality evaluation of a given update deployment.
Note
You can't create additional deployment rings or use your own rings for devices managed by the Windows Autopatch service.
Default deployment ring calculation logic
The Windows Autopatch deployment ring calculation occurs during the device registration process and it applies to both the service-based and the software update-based deployment ring sets:
- If the Windows Autopatch tenant's existing managed device size is ≤ 200, the deployment ring assignment is First (5%), Fast (15%), remaining devices go to the Broad ring (80%).
- If the Windows Autopatch tenant's existing managed device size is >200, the deployment ring assignment will be First (1%), Fast (9%), remaining devices go to the Broad ring (90%).
Note
You can customize the deployment ring calculation logic by editing the Default Autopatch group.
| Service-based deployment ring | Default Autopatch group deployment ring | Default device balancing percentage | Description |
|---|---|---|---|
| Test | Test | zero | Windows Autopatch doesn't automatically add devices to this deployment ring. You must manually add devices to the Test ring following the required procedure. For more information on these procedures, see Moving devices in between deployment rings. The recommended number of devices in this ring, based upon your environment size, is as follows:
|
| First | Ring 1 | 1% | The First ring is the first group of production users to receive a change. This group is the first set of devices to send data to Windows Autopatch and are used to generate a health signal across all end-users. For example, Windows Autopatch can generate a statistically significant signal saying that critical errors are trending up in a specific release for all end-users, but can't be confident that it's doing so in your organization. Since Windows Autopatch doesn't yet have sufficient data to inform a release decision, devices in this deployment ring might experience outages if there are scenarios that weren't covered during early testing in the Test ring. |
| Fast | Ring 2 | 9% | The Fast ring is the second group of production users to receive changes. The signals from the First ring are considered as a part of the release process to the Broad ring. The goal with this deployment ring is to cross the 500-device threshold needed to generate statistically significant analysis at the tenant level. These extra devices allow Windows Autopatch to consider the effect of a release on the rest of your devices and evaluate if a targeted action for your tenant is needed. |
| Broad | Ring 3 | Either 80% or 90% | The Broad ring is the last group of users to receive software update deployments. Since it contains most of the devices registered with Windows Autopatch, it favors stability over speed in a software update deployment. |
| N/A | Last | zero | The Last ring is intended to be used for either specialized devices or devices that belong to VIP/executives in an organization. Windows Autopatch doesn't automatically add devices to this deployment ring. |
Software update-based to service-based deployment ring mapping
There's a one-to-one mapping in between the service-based and software updates-based deployment rings introduced with Autopatch groups. This mapping is intended to help move devices in between deployment rings for other software update workloads that don't yet support Autopatch groups such as Microsoft 365 Apps and Microsoft Edge.
| If moving a device to | The device also moves to |
|---|---|
| Windows Autopatch - Test | Modern Workplace Devices-Windows Autopatch-Test |
| Windows Autopatch - Ring1 | Modern Workplace Devices-Windows Autopatch-First |
| Windows Autopatch - Ring2 | Modern Workplace Devices-Windows Autopatch-Fast |
| Windows Autopatch - Ring3 | Modern Workplace Devices-Windows Autopatch-Broad |
| Windows Autopatch - Last | Modern Workplace Devices-Windows Autopatch-Broad |
If your Autopatch groups have more than five deployment rings, and you must move devices to deployment rings after Ring3. For example, <Autopatch group name - Ring4, Ring5, Ring6, etc.>. The devices will be moved to Modern Workplace Devices-Windows Autopatch-Broad.
Moving devices in between deployment rings
If you want to move devices to different deployment rings (either service or software update-based), after Windows Autopatch's deployment ring assignment, you can repeat the following steps for one or more devices from the Registered tab.
Important
You can only move devices in between deployment rings within the same Autopatch group. You can't move devices in between deployment rings across different Autopatch groups. If you try to select a device that belongs to one Autopatch group, and another device that belongs to a different Autopatch group, you'll receive the following error message on the top right corner of the Microsoft Intune portal: "An error occurred. Please select devices within the same Autopatch group.
To move devices in between deployment rings:
Note
You can only move devices to other deployment rings when they're in an active state in the Registered tab.
- In the Intune admin center, select Devices in the left pane.
- In the Windows Autopatch section, select Devices.
- In the Registered tab, select one or more devices you want to assign. All selected devices will be assigned to the deployment ring you specify.
- Select Device actions from the menu.
- Select Assign ring. A fly-in opens.
- Use the dropdown menu to select the deployment ring to move devices to, and then select Save. The Ring assigned by column will change to Pending.
- When the assignment is complete, the Ring assigned by column changes to Admin (which indicates that you made the change) and the Ring column shows the new deployment ring assignment.
If you don't see the Ring assigned by column change to Pending in Step 5, check to see whether the device exists in Microsoft Intune or not by searching for it in its device blade. For more information, see Device details in Intune.
Warning
Moving devices between deployment rings through directly changing Microsoft Entra group membership isn't supported and may cause unintended configuration conflicts within the Windows Autopatch service. To avoid service interruption to devices, use the Assign device to ring action described previously to move devices between deployment rings.
Automated deployment ring remediation functions
Windows Autopatch monitors device membership in its deployment rings, except for the Modern Workplace Devices-Windows Autopatch-Test, Windows Autopatch - Test and Windows Autopatch - Last rings, to provide automated deployment ring remediation functions to mitigate the risk of not having its managed devices being part of one of its deployment rings. These automated functions help mitigate risk of potentially having devices in a vulnerable state, and exposed to security threats in case they're not receiving update deployments due to either:
- Changes performed by the IT admin on objects created by the Windows Autopatch tenant enrollment process, or
- An issue occurred which prevented devices from getting a deployment ring assigned during the device registration process.
There are two automated deployment ring remediation functions:
| Function | Description |
|---|---|
| Check device deployment ring membership | Every hour, Windows Autopatch checks to see if any of its managed devices aren't part of one of the deployment rings. If a device isn't part of a deployment ring, Windows Autopatch randomly assigns the device to one of its deployment rings (except for the Modern Workplace Devices-Windows Autopatch-Test, Windows Autopatch - Test and Windows Autopatch - Last rings). |
| Multi-deployment ring device remediator | Every hour, Windows Autopatch checks to see if any of its managed devices are part of multiple deployment rings (except for the Modern Workplace Devices-Windows Autopatch-Test, Windows Autopatch - Test and Windows Autopatch - Last rings). If a device is part of multiple deployment rings, Windows Autopatch randomly removes the device until the device is only part of one deployment ring. |
Important
Windows Autopatch automated deployment ring functions don't assign or remove devices to or from the following deployment rings:
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for