Hello there,
Microsoft announced this week that it enabled TLS 1.3, the latest version of the security protocol, in the latest Windows 10 builds starting with build 20170.
-Press the Windows key + R to start Run, type regedit, and press Enter or click OK.
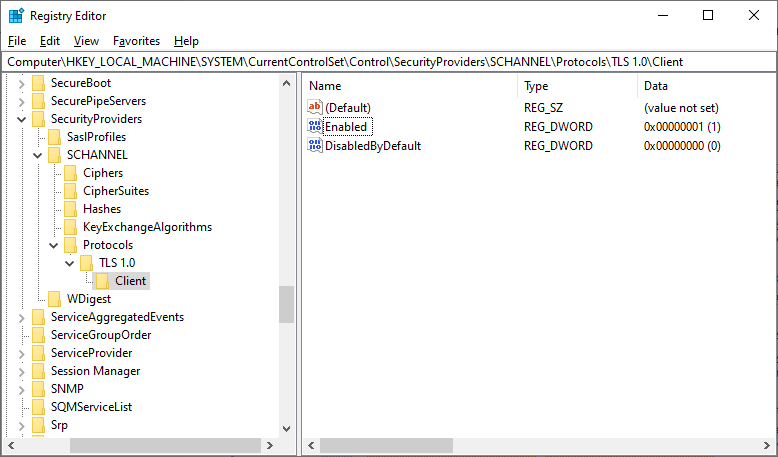
-Now go to the following key and check it. If it’s present, the value should be 0:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client\DisabledByDefault
-Also, check the following key. If you find it, its value should be 1:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client\Enabled
-If you can’t find any of the keys or if their values are not correct, then TLS 1.2 is not enabled.
I hope this information helps. If you have any questions please let me know and I will be glad to help you out.
-------------------------------------------------------------------------------------------------------------
--If the reply is helpful, please Upvote and Accept it as an answer--