I have been researching this again today (having had this issue for months) and found the following: OpenSSL are aware of the issues that are raised in CVE-2024-2511 but consider it low severity and won't be addressing it anytime soon:
This issue only affects TLS servers supporting TLSv1.3. It does not affect TLS
clients.
The FIPS modules in 3.2, 3.1 and 3.0 are not affected by this issue. OpenSSL
1.0.2 is also not affected by this issue.
OpenSSL 3.2, 3.1, 3.0, 1.1.1 are vulnerable to this issue.
OpenSSL 3.2 users should upgrade to OpenSSL 3.2.2 once it is released.
OpenSSL 3.1 users should upgrade to OpenSSL 3.1.6 once it is released.
OpenSSL 3.0 users should upgrade to OpenSSL 3.0.14 once it is released.
OpenSSL 1.1.1 users should upgrade to OpenSSL 1.1.1y once it is released
(premium support customers only).
Due to the low severity of this issue we are not issuing new releases of
OpenSSL at this time. The fix will be included in the next releases when they
become available. The fix is also available in commit e9d7083e (for 3.2),
commit 7e4d731b (for 3.1) and commit b52867a9 (for 3.0) in the OpenSSL git
repository. It is available to premium support customers in commit
5f8d2577 (for 1.1.1).
Source: https://openssl-library.org/news/secadv/20240408.txt
This was dated 8 April 2024.
It doesn't matter what Zoom or PowerBI or anyone do, CVE-2024-2511 will be around until OpenSSL address the weaknesses in those specific libraries.
If you have Zoom, update to version 6.1.0 or above to address OpenSSL flaws except CVE-2024-2511 and CVE-2024-4603, which doesn't affect clients:
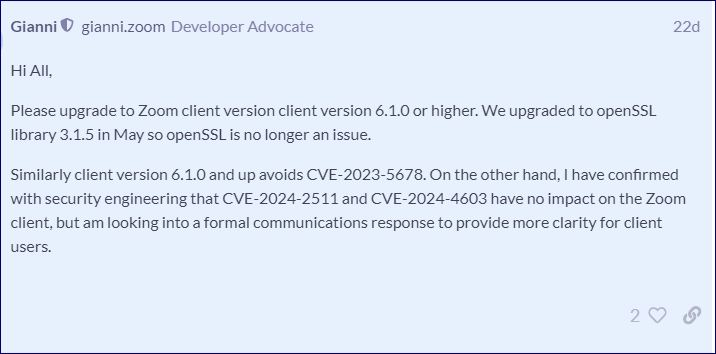
Source: https://devforum.zoom.us/t/zoom-5-6-10-vulnerabilities-with-openssl-dll-need-version-3-1-5/98806/78?page=4
