Hello @learlab,
Thank you for posting your query on Microsoft Q&A.
It seems you're encountering an issue when users attempt to sign in to your application using their Outlook accounts, receiving the error message "AADSTS50020: User account 'user@outlook.com' from identity provider 'live.com' does not exist in tenant '<tenant_name>' and cannot access the application '<App_ID>'(App Name) in that tenant. The account needs to be added as an external user in the tenant first. Sign out and sign in again with a different Azure Active Directory user account." This occurs despite the application supporting "signInAudience": "AzureADandPersonalMicrosoftAccount".
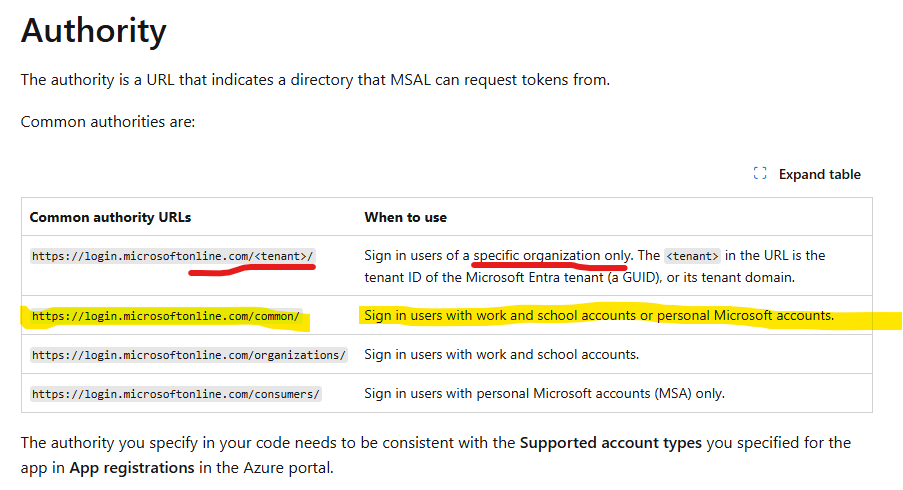
This issue typically arises when your application sends requests with a specific tenant ID. For instance, if your application is configured to support both work and school accounts or personal Microsoft accounts, and you generate an access token by sending a request to https://login.microsoftonline.com/<tenant>/ authority URL, it will only authenticate users within that specific tenant. That's why you have received an error message stating to add user as an external user in the tenant first.
To enable sign-ins from other tenants or personal accounts, you should send requests to https://login.microsoftonline.com/common/. Please verify whether your application is using the /common/ authority URL. If it is currently sending requests to https://login.microsoftonline.com/<tenant>/, you should coordinate with your application team to update the authority URL to /common/.
For more details on authority URLs, you can refer to the documentation here:
https://learn.microsoft.com/en-us/entra/identity-platform/msal-client-application-configuration#authority
I hope this information is helpful. Please feel free to reach out if you have any further questions.
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.
Thanks,
Raja Pothuraju.
