Enable data policy enforcement on your Microsoft Purview sources
Data policy enforcement is an option within the data source registration in Microsoft Purview. This option lets Microsoft Purview manage data access for your resources. The high level concept is that the data owner allows its data resource to be available for access policies by enabling data policy enforcement.
Currently, a data owner can enable data policy enforcement on a data resource, which enables it for these types of access policies:
- DevOps policies
- Data owner access policies
- Self-service access policies - access policies automatically generated by Microsoft Purview after a self-service access request is approved.
- Protection-policies
To be able to create any data policy on a resource, data policy enforcement must first be enabled on that resource. This article will explain how to enable data policy enforcement on your resources in Microsoft Purview.
Important
Because data policy enforcement directly affects access to your data, it directly affects your data security. Review additional considerations and best practices below before enabling data policy enforcement in your environment.
Prerequisites
Register the data source in Microsoft Purview
Before a policy can be created in Microsoft Purview for a data resource, you must register that data resource in Microsoft Purview Studio. You will find the instructions related to registering the data resource later in this guide.
Note
Microsoft Purview policies rely on the data resource ARM path. If a data resource is moved to a new resource group or subscription it will need to be de-registered and then registered again in Microsoft Purview.
Configure permissions to enable Data policy enforcement on the data source
Once a resource is registered, but before a policy can be created in Microsoft Purview for that resource, you must configure permissions. A set of permissions are needed to enable the Data policy enforcement. This applies to data sources, resource groups, or subscriptions. To enable Data policy enforcement, you must have both specific Identity and Access Management (IAM) privileges on the resource as well as specific Microsoft Purview privileges:
You must have either one of the following IAM role combinations on the resource's Azure Resource Manager path or any parent of it (that is, using IAM permission inheritance):
- IAM Owner
- Both IAM Contributor and IAM User Access Administrator
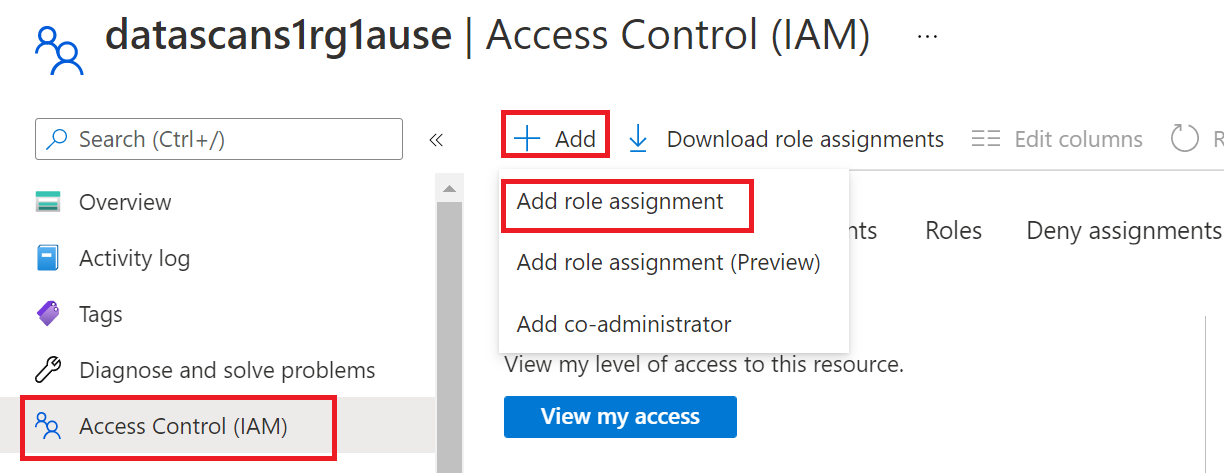
To configure Azure role-based access control (RBAC) permissions, follow this guide. The following screenshot shows how to access the Access Control section in the Azure portal for the data resource to add a role assignment.
Note
The IAM Owner role for a data resource can be inherited from a parent resource group, a subscription, or a subscription management group. Check which Microsoft Entra users, groups, and service principals hold or are inheriting the IAM Owner role for the resource.
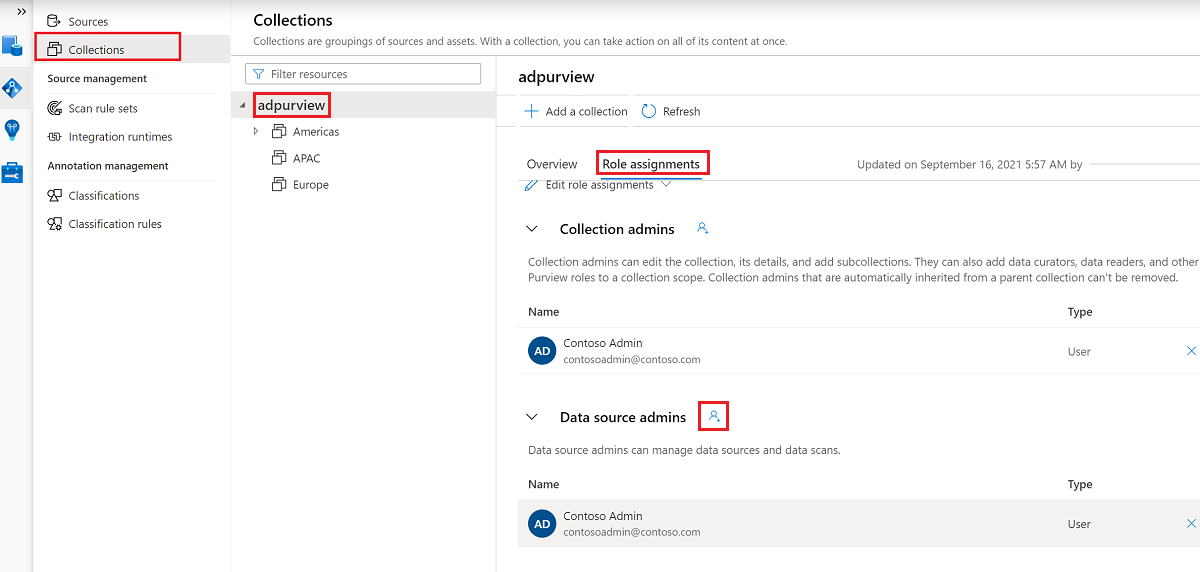
You also need to have the Microsoft Purview Data source admin role for the collection or a parent collection (if inheritance is enabled). For more information, see the guide on managing Microsoft Purview role assignments.
The following screenshot shows how to assign the Data source admin role at the root collection level.
Configure Microsoft Purview permissions to create, update, or delete access policies
To create, update or delete policies, you need to get the Policy author role in Microsoft Purview at root collection level:
- The Policy author role can create, update, and delete DevOps and Data Owner policies.
- The Policy author role can delete self-service access policies.
For more information about managing Microsoft Purview role assignments, see Create and manage collections in the Microsoft Purview Data Map.
Note
Policy author role must be configured at the root collection level.
In addition, to easily search Microsoft Entra users or groups when creating or updating the subject of a policy, you can greatly benefit from getting the Directory Readers permission in Microsoft Entra ID. This is a common permission for users in an Azure tenant. Without the Directory Reader permission, the Policy Author will have to type the complete username or email for all the principals included in the subject of a data policy.
Configure Microsoft Purview permissions for publishing Data Owner policies
Data Owner policies allow for checks and balances if you assign the Microsoft Purview Policy author and Data source admin roles to different people in the organization. Before a Data owner policy takes effect, a second person (Data source admin) must review it and explicitly approve it by publishing it. This does not apply to DevOps or Self-service access policies as publishing is automatic for them when those policies are created or updated.
To publish a Data owner policy you need to get the Data source admin role in Microsoft Purview at root collection level.
For more information about managing Microsoft Purview role assignments, see Create and manage collections in the Microsoft Purview Data Map.
Note
To publish Data owner policies, the Data source admin role must be configured at the root collection level.
Delegate access provisioning responsibility to roles in Microsoft Purview
After a resource has been enabled for Data policy enforcement, any Microsoft Purview user with the Policy author role at the root collection level can provision access to that data source from Microsoft Purview.
Note
Any Microsoft Purview root Collection admin can assign new users to root Policy author roles. Any Collection admin can assign new users to a Data source admin role under the collection. Minimize and carefully vet the users who hold Microsoft Purview Collection admin, Data source admin, or Policy author roles.
If a Microsoft Purview account with published policies is deleted, such policies will stop being enforced within an amount of time that depends on the specific data source. This change can have implications on both security and data access availability. The Contributor and Owner roles in IAM can delete Microsoft Purview accounts. You can check these permissions by going to the Access control (IAM) section for your Microsoft Purview account and selecting Role Assignments. You can also use a lock to prevent the Microsoft Purview account from being deleted through Resource Manager locks.
Enable data policy enforcement
To enable data policy enforcement for a resource, the resource will first need to be registered in Microsoft Purview. To register a resource, follow the Prerequisites and Register sections of the source pages for your resources.
Once you have your resource registered, follow the rest of the steps to enable an individual resource for data policy enforcement.
From the classic Microsoft Purview governance portal
Go to the classic Microsoft Purview governance portal.
Select the Data map tab in the left menu.
Select the Sources tab in the left menu.
Select the source where you want to enable data policy enforcement.
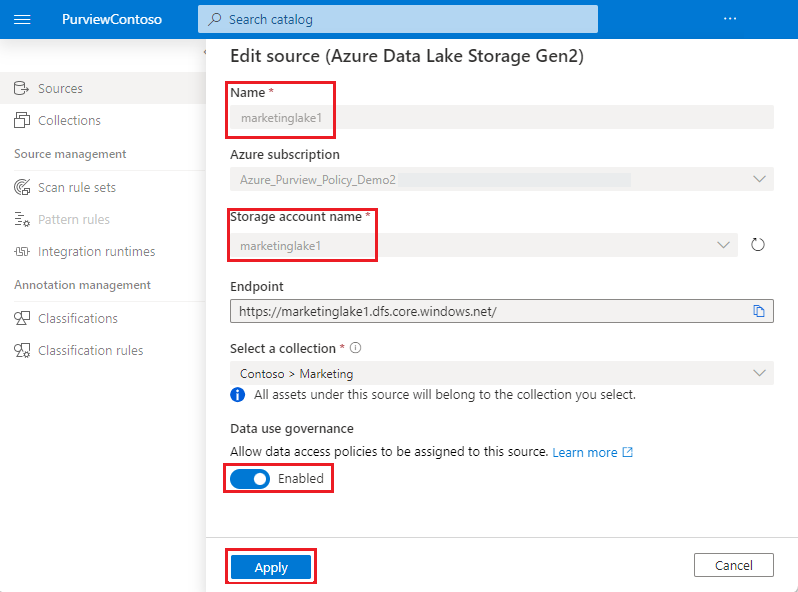
At the top of the source page, select Edit source.
Set the Data policy enforcement toggle to Enabled, as shown in the image below.
From the new Microsoft Purview portal
Go to the new Microsoft Purview portal.
Select the Data Map tab in the left menu.
Select the Data sources tab in the left menu.
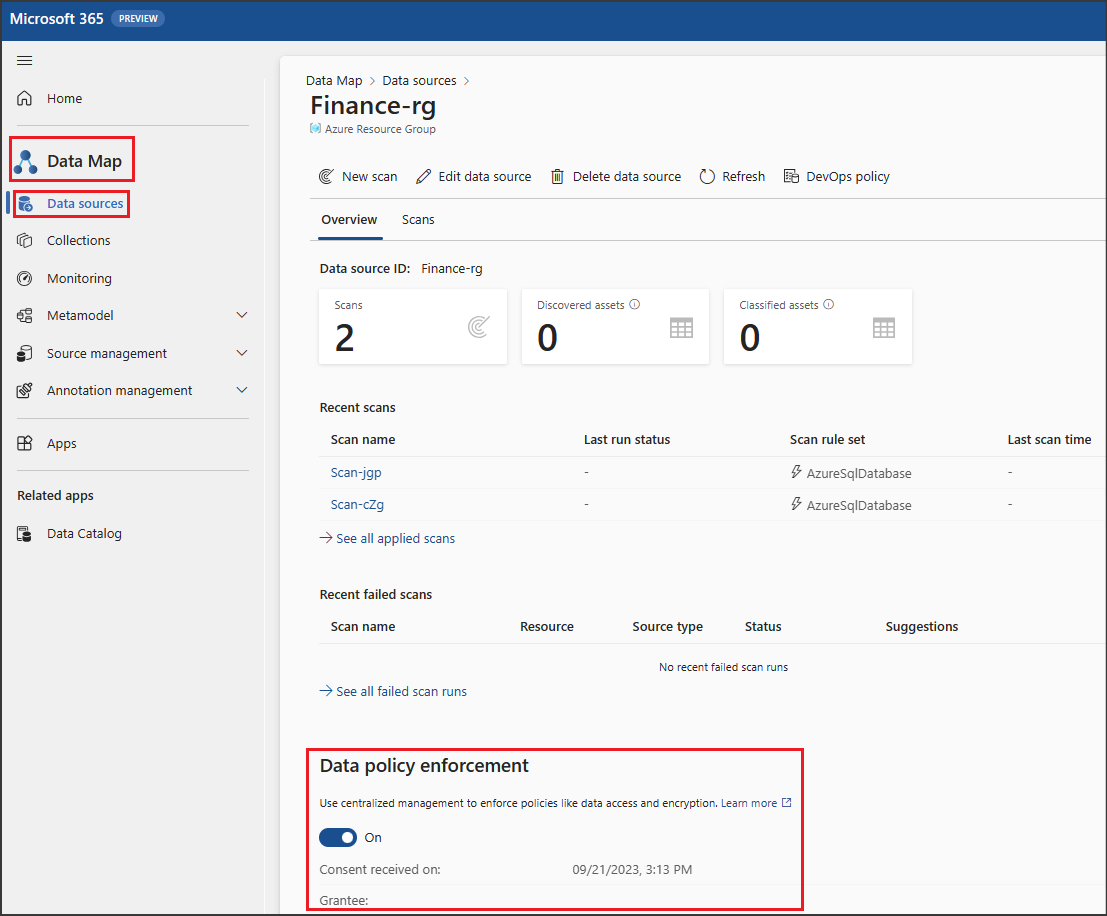
Select the source where you want to enable data policy enforcement.
Set the Data policy enforcement toggle to On, as shown in the image below.
Disable data policy enforcement
To disable data policy enforcement for a source, resource group, or subscription, a user needs to either be a resource IAM Owner or a Microsoft Purview Data source admin. Once you have those permissions follow these steps:
From the classic Microsoft Purview governance portal
Go to the Microsoft Purview governance portal.
Select the Data map tab in the left menu.
Select the Sources tab in the left menu.
Select the source you want to disable data policy enforcement for.
At the top of the source page, select Edit source.
Set the Data policy enforcement toggle to Disabled.
From the new Microsoft Purview portal
Go to the new Microsoft Purview portal.
Select the Data map tab in the left menu.
Select the Sources tab in the left menu.
Select the source you want to disable data policy enforcement for.
Set the Data policy enforcement toggle to Off.
Additional considerations related to data policy enforcement
- Make sure you write down the Name you use when registering in Microsoft Purview. You will need it when you publish a policy. The recommended practice is to make the registered name exactly the same as the endpoint name.
- To disable a source for data policy enforcement, you first have to remove any published policies on that data source.
- While user needs to have both data source Owner and Microsoft Purview Data source admin to enable a source for data policy enforcement, any Data Source admin for the collection can disable it.
- Disabling data policy enforcement for a subscription will disable it also for all assets registered in that subscription.
Warning
Known issues related to source registration
- Moving data sources to a different resource group or subscription is not supported. If want to do that, de-register the data source in Microsoft Purview before moving it and then register it again after that happens. Note that policies are bound to the data source ARM path. Changing the data source subscription or resource group makes policies ineffective.
- Once a subscription gets disabled for data policy enforcement any underlying assets that are enabled for data policy enforcement will be disabled, which is the right behavior. However, policy statements based on those assets will still be allowed after that.
Data policy enforcement best practices
- We highly encourage registering data sources for data policy enforcement and managing all associated access policies in a single Microsoft Purview account.
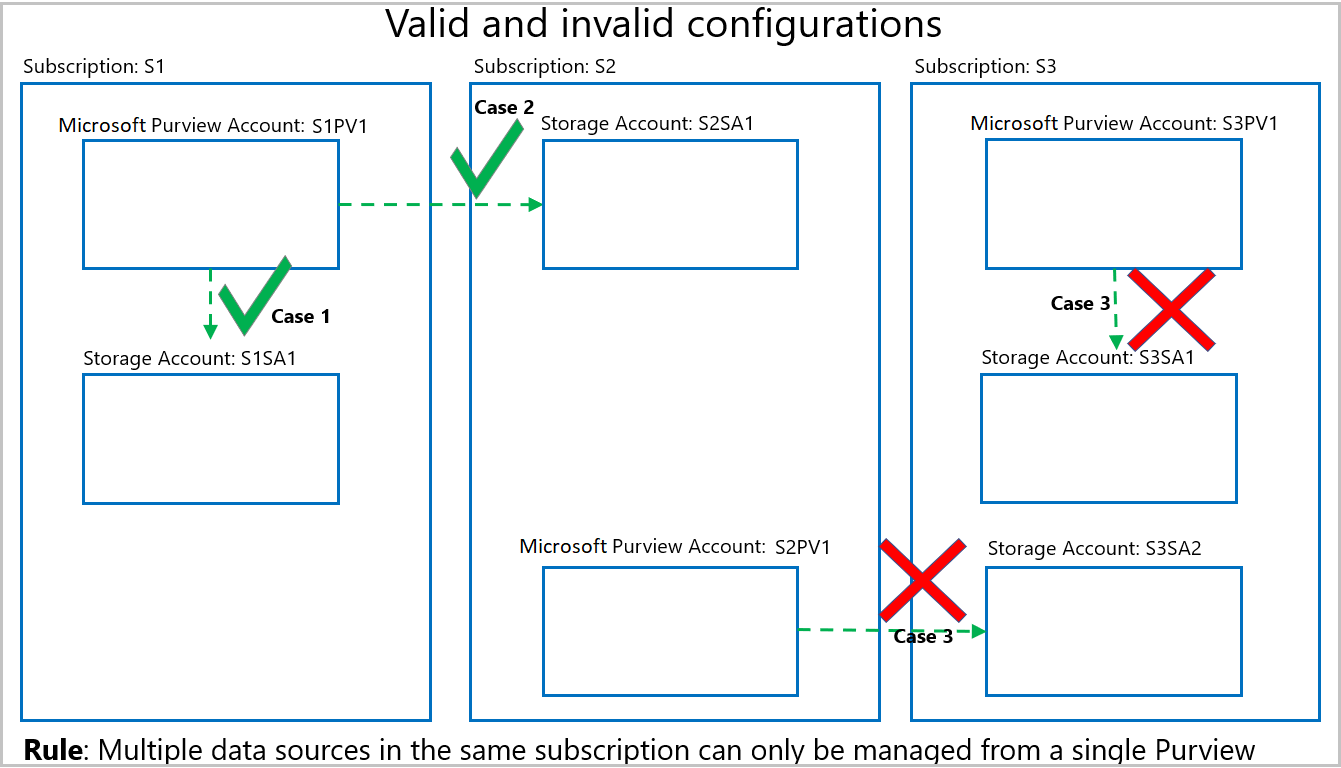
- Should you have multiple Microsoft Purview accounts, be aware that all data sources belonging to a subscription must be registered for data policy enforcement in a single Microsoft Purview account. That Microsoft Purview account can be in any subscription in the tenant. The data policy enforcement toggle will become greyed out when there are invalid configurations. Some examples of valid and invalid configurations follow in the diagram below:
- Case 1 shows a valid configuration where a Storage account is registered in a Microsoft Purview account in the same subscription.
- Case 2 shows a valid configuration where a Storage account is registered in a Microsoft Purview account in a different subscription.
- Case 3 shows an invalid configuration arising because Storage accounts S3SA1 and S3SA2 both belong to Subscription 3, but are registered to different Microsoft Purview accounts. In that case, the data policy enforcement toggle will only enable in the Microsoft Purview account that wins and registers a data source in that subscription first. The toggle will then be greyed out for the other data source.
- If the data policy enforcement toggle is greyed out and cannot be enabled, hover over it to know the name of the Microsoft Purview account that has registered the data resource first.
Next steps
Comentarios
Próximamente: A lo largo de 2024 iremos eliminando gradualmente GitHub Issues como mecanismo de comentarios sobre el contenido y lo sustituiremos por un nuevo sistema de comentarios. Para más información, vea: https://aka.ms/ContentUserFeedback.
Enviar y ver comentarios de