How To: Detect Cross Site Scripting Vulnerabilities using XSSDetect
RV again...
Last time we saw how to fix a cross site scripting (XSS) vulnerability. This time we look at how we can detect cross site scripting vulnerabilities using automated tools. Being the most common vulnerability found in web applications, it is very important to detect and mitigate XSS vulnerabilities early in development cycle. Arming developers with the right tools to develop application security is a big problem in every enterprise. Here at Microsoft, we have developed a static analysis tool specifically aimed at developers to detect cross site scripting. It was released a while ago as Microsoft XSSDetect.
XSSDetect is stripped down version of the Code Analysis Tool for .NET used by the ACE team to help find security vulnerabilities in software applications. It has been made available for free on Microsoft downloads. XSSDetect comes as a Visual Studio Add-in that can identify non-persistent XSS vulnerabilities in ASP.NET web-applications. XSSDetect is a type of static analysis tool, which uses Microsoft CCI libraries for analysis. CCI libraries are the same libraries used by FxCop. XSSDetect is a bit more than a FxCop plugin, as XSSDetect uses interprocedural analysis to detect XSS vulnerabilities. It uses the notion of Sources (input entry point) and Sinks (output method) to detect data paths which could lead to a XSS vulnerability.
The following are some examples of Sources and Sinks.
| Sources | Sinks |
| System.Web.HttpRequest.get_QueryString | System.Web.HttpResponse.Write |
| System.Web.HttpRequest.get_Form | System.IO.TextWriter.Write |
| System.Web.HttpRequest.get_Params | System.Web.UI.WebControls.Label.set_Text |
| System.Web.HttpRequest.get_Cookies | System.Web.UI.WebControls.HyperLink.set_Text |
| System.Web.UI.WebControls.TextBox.Text | System.Web.UI.WebControls.LinkButton.set_Text |
XSSDetect builds a huge data graph of the binary and identifies the data paths containing these sources and sinks. If any of these data paths use a encoding library such as AntiXss library it will be excluded from the results. You can find more information on the Sources, Sinks and Encoding rules in the %PROGRAMFILES%\Microsoft\XSSDetect\Config. Lets look at some vulnerable code that will be detected by XSSDetect.
1: //Code in .aspx page
2: <%=Request.QueryString["message"];%>
3:
4: //Writing hidden field value back on to the page
5: Response.Write(hidHiddenInput.Value);
6:
7: //Setting the link button text
8: LinkButton1.Text = String.Format(txtInput.Text, "LinkButton1.Text");
9:
10: //HTML table object
11: Table1.Caption = String.Format(txtInput.Text, "Table1.Caption");
12: Table1.Rows[0].Cells[0].Text =
13: String.Format(txtInput.Text, "Table1.Rows[0].Cells[0].Text");
14:
15: //Literal object text
16: Literal1.Text = String.Format(txtInput.Text, "Literal.Text");
17:
18: //Checkbox and Label text assignments
19: CheckBox1.Text = String.Format(txtInput.Text, "CheckBox1.Text");
20: Label1.Text = String.Format(txtInput.Text, "Label1.Text")
21:
22: //Indirect XSS
23: string strInput;
24: protected void Page_Load(object sender, EventArgs e)
25: {
26: strInput = Request.QueryString["message"];
27: this.SetMessage(strInput);
28: }
29:
30: private void SetMessage(string input)
31: {
32: Label1.Text = input;
33: }
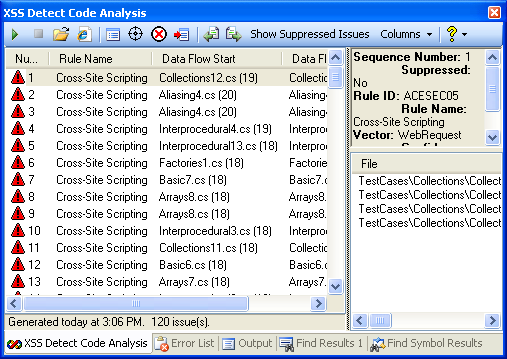
XSSDetect can detect many more variants of XSS vulnerabilities possible in ASP.NET Code. XSSDetect is currently available for Visual Studio 2005, we are working on a release to make it compatible with Visual Studio 2008. After installation go to Tools -> XSS Detect. It should open up a window as shown below.
Click the green "Play"/"Run" button (first button in the toolbar) to start the analysis. Please make sure that the solution is loaded and has all the needed references because XSSDetect will compile the source code to analyze the binary. Click on the Help Icon to open up the help file to find more information on the other features of XSSDetect. You can download XSS detect from MSDN downloads at https://www.microsoft.com/Downloads/details.aspx?FamilyID=19a9e348-bdb9-45b3-a1b7-44ccdcb7cfbe&displaylang=en. You can also see a FAQ for the tool at https://blogs.msdn.com/ace_team/archive/2007/12/11/xssdetect-faq.aspx.
Keep checking our blog for more exciting posts on Cross Site Scripting vulnerabilities and mitigation's.
Comments
- Anonymous
September 01, 2008
PingBack from http://blog.a-foton.ru/2008/09/how-to-detect-cross-site-scripting-vulnerabilities-using-xssdetect/ - Anonymous
September 01, 2008
XssDetect:System RequirementsSupported Operating Systems: Windows Vista; Windows XPMicrosoft Visual Studio 2005Microsoft .NET Framework Version 2.0Does microsoft provide installation file for VS2008 and .NET 3.5? (I seem not to be able to install on VS2008) - Anonymous
September 02, 2008
This week I have posted another blog entry on our team site. It is on using automated code analysis tool - Anonymous
October 30, 2008
Thanks, used this back in VS2005 and am missing it for 2008. Is there an approx timeline when it will be released for VS2008? - Anonymous
October 30, 2008
Unsupported way of doing this in VS2008 right now is to replace HostApplication childnodes with: <Name>Microsoft Visual Studio</Name> <Version>9.0</Version>under addin file in Application DataMicrosoftMSEnvSharedAddins