SSL/TLS - Decrypt the encrypted network traces
Ask:
As we know SSL/TLS is encrypted traffic using symmetric keys created during SSL/TLS handshake. Many a time we might need to decrypt this traffic to observe the request/response packets or client certificates being sent.
Tools Needed to decrypt the traffic:
1. Network monitor 3.4 - https://www.microsoft.com/en-in/download/details.aspx?id=4865
2. NMDecrypt 2.3.4 - https://nmdecrypt.codeplex.com/ 3. Server Certificate - Private Key
Theory for presenting client certificate:
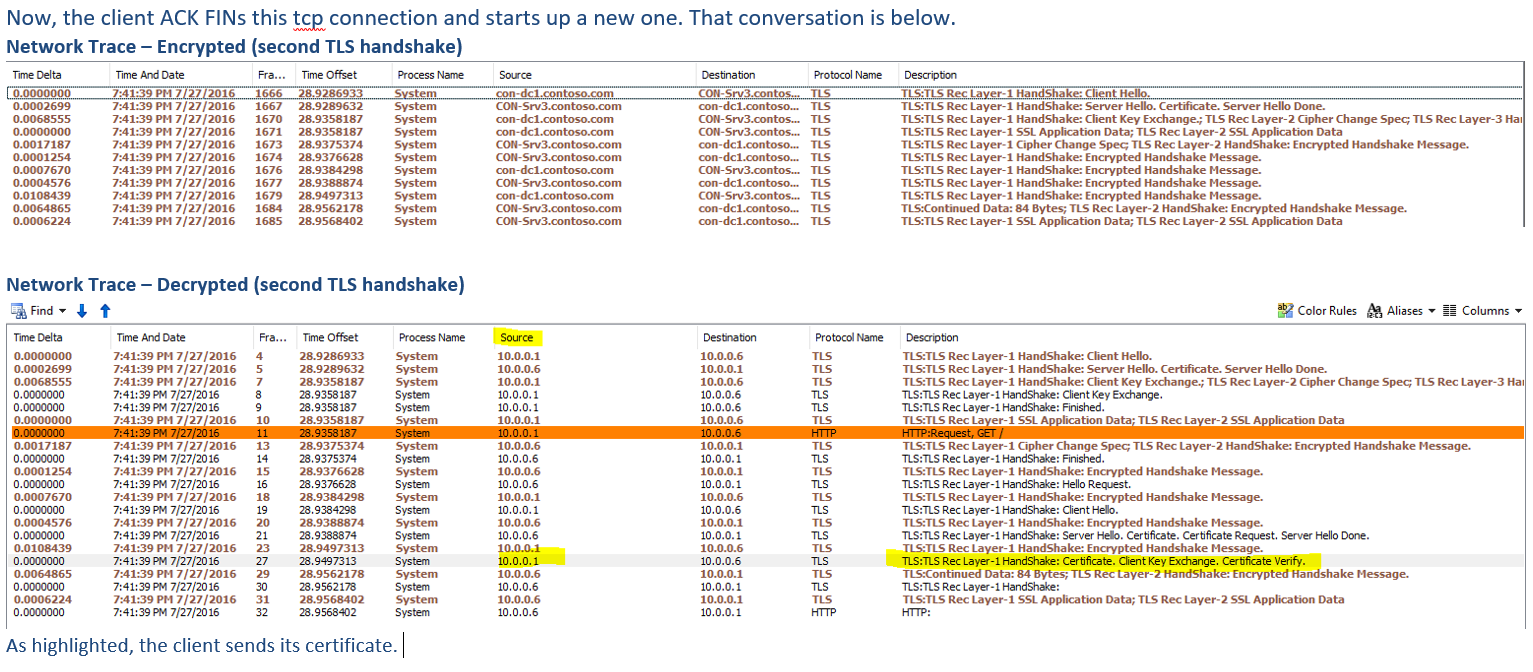
Client certificate: When this message will be sent?
This is the first message the client can send after receiving a server hello done message.
This message is only sent if the server requests a certificate.
If no suitable certificate is available, the client should send a certificate message containing no certificates.
If client authentication is required by the server for the handshake to continue, it may respond with a fatal handshake failure alert.
Steps:
1. Make sure there are no existing SSL/TLS session established between client and server.
2. Start Network monitor on both client and server side (during collection, use CAPTURE SETTINGS to collect traffic between desired ports only)
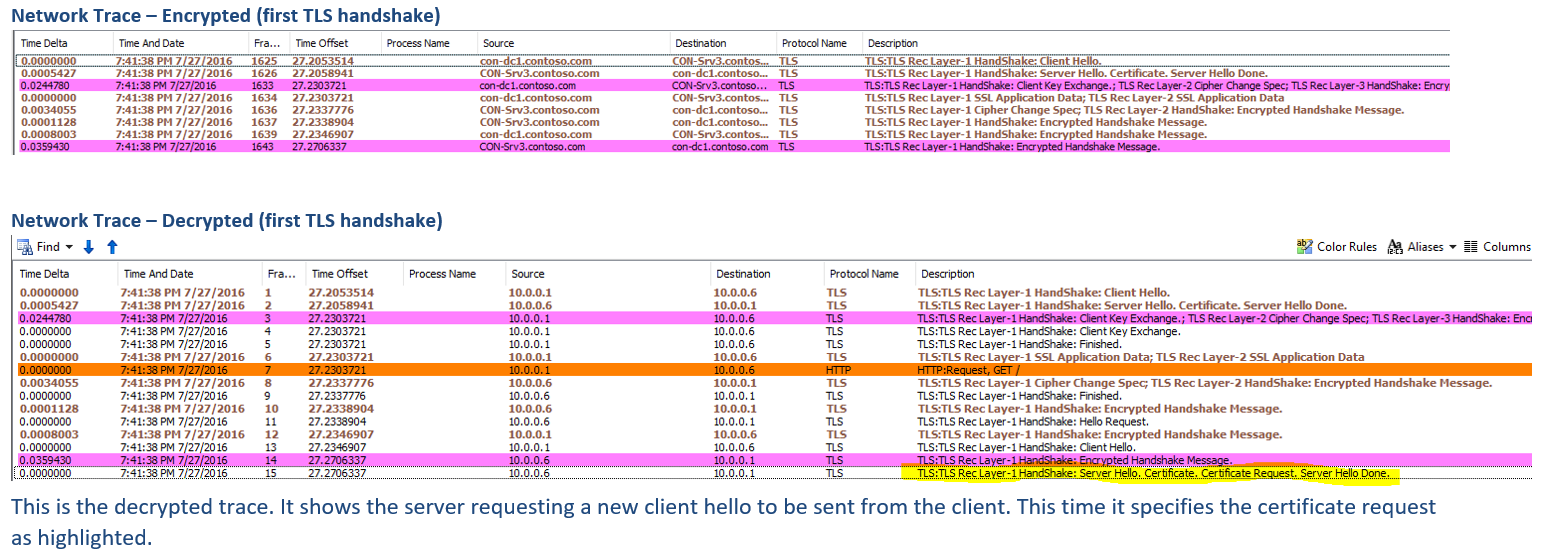
3. Once the data is collected we need to make sure that there is no SESSION ID being used along with Client Hello packet.
Client Hello with no session ID
 Once we are sure that the network traces are collected with NO existing SESSION ID, time to decrypt them. To use the NMDecrypt with Network Monitor, make sure to select the desired TCP communication from the left side tree view.
Once we are sure that the network traces are collected with NO existing SESSION ID, time to decrypt them. To use the NMDecrypt with Network Monitor, make sure to select the desired TCP communication from the left side tree view.
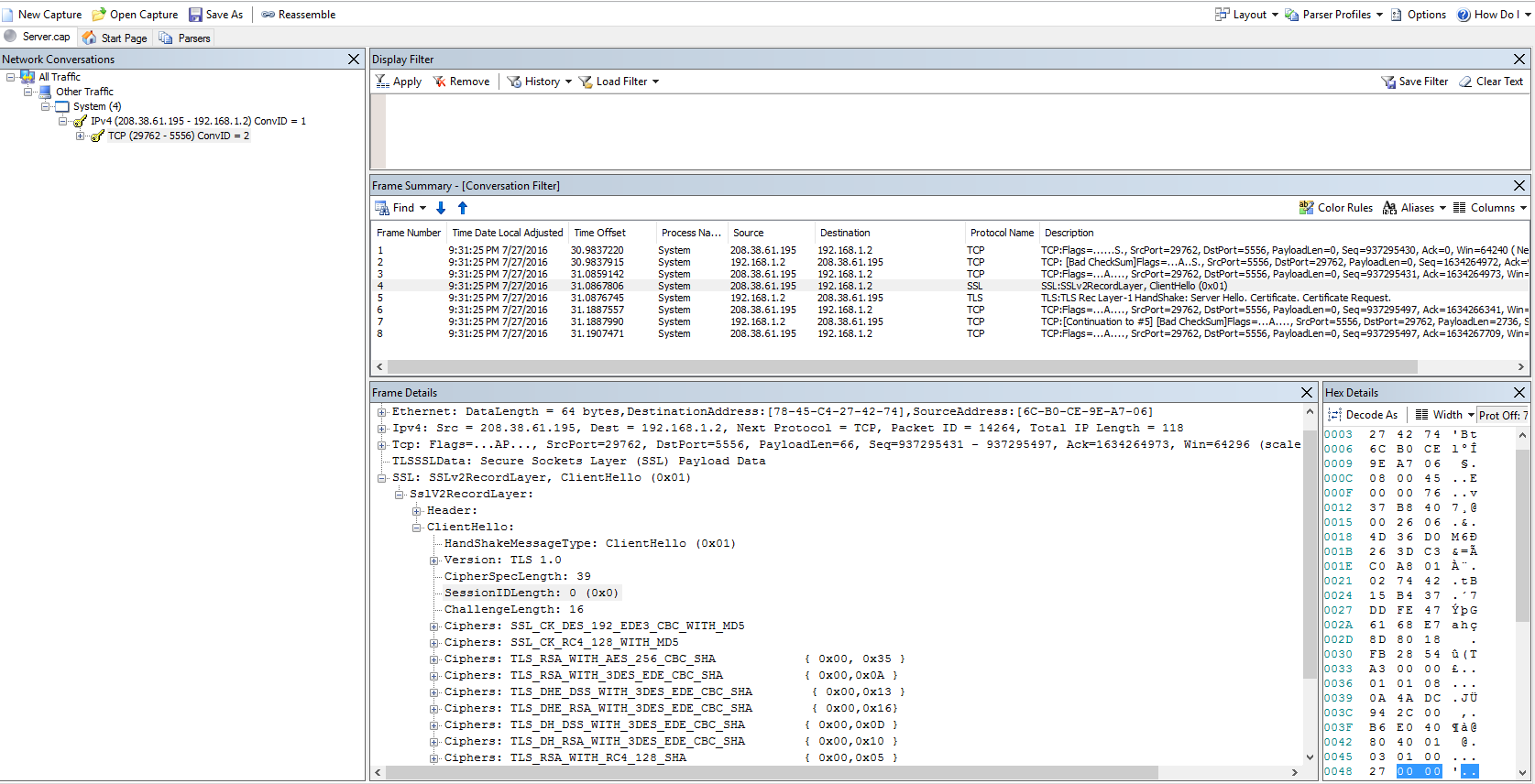
Selecting desired TCP conversation:
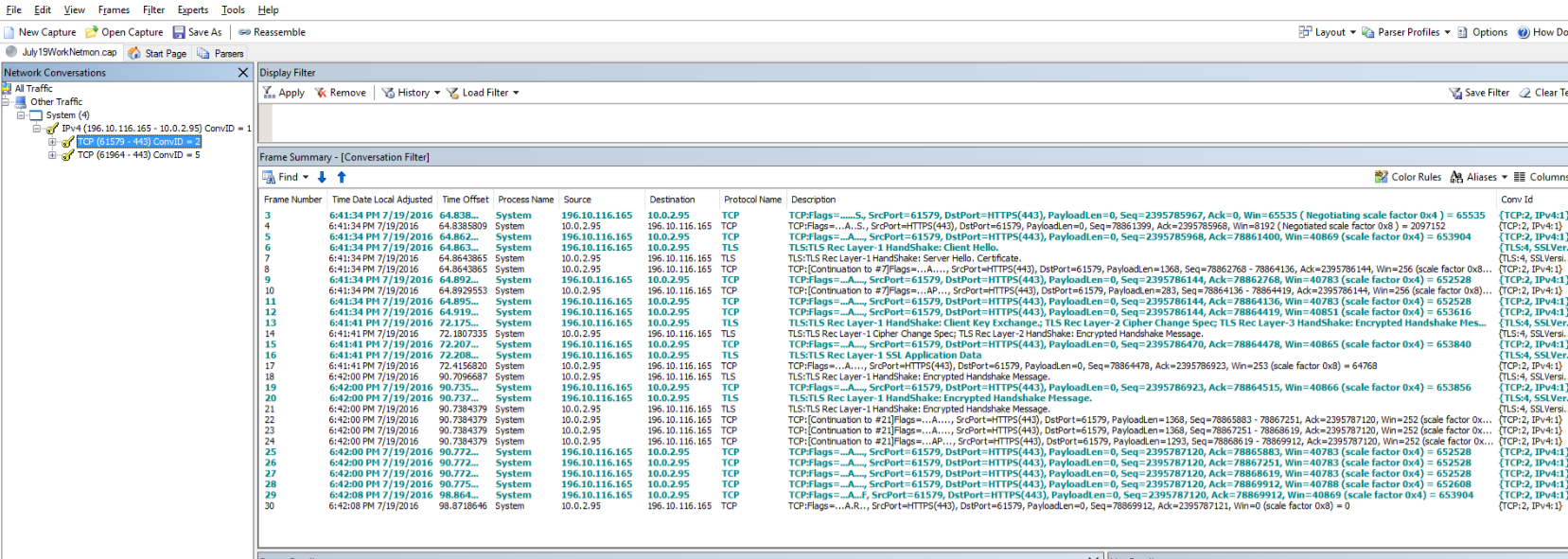
After selecting the conversation, go to Expert Menu and select Run NMDecrypt.Here we would need to specify the correct SERVER CERT and Private Key Password. Once done we should be able to decrypt the traffic.
Hope the steps help! Saurabh Somani