SharePoint 2013–Generating Unique Permissions Report
There will be several instances when you will like to generate reports of all the unique permissions that are present through out the site collection.
I have written a script which will generate a CSV report with all the users and groups added on the Web, List, Item or Folder level
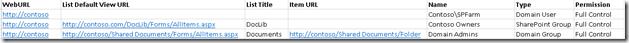
Refer to the screenshot CSV report.
This report
will contain 7 columns
- WebURL – Url of the Site
- List Default View URL – Default view of the List. If this is blank that means permission are broken at Web Level and the User-Group reported has been added at the web level. If this contains information then it means permissions have been broken at the list level and the user-group along with permission reported has been added at the List level.
- List Title – Title of the list. If this is blank that means permission are broken at Web Level and the User-Group reported has been added at the web level.If this contains information then it means permissions have been broken at the list level and the user-group along with permission reported has been added at the List level.
- Item URL – URL of the Item.If this is blank that means permission are broken at Web/list Level and the User-Group reported has been added at the web/list level. If this contains information then it means permissions have been broken at the Item level and the user-group along with permission reported has been added at the Item level.
- Name – Name of User or Group
- Type – If it’s a Domain Group, Domain User or SharePoint Group
- Permission – Permissions granted to the user or group. Note if the OOB permissions levels have been modified then this information might mislead. It’s not a good practice to modify OOB permission levels.
Add-PSSnapin Microsoft.SharePoint.Powershell
$Url = "https://contoso.com" #Replace URL with your site collection
$RootURL = $url.Split("/") # Split function is required for Host based site collection
$RootURL = $RootURL[0] + "/" + $RootURL[1] + "/" + $RootURL[2]$logTime = Get-Date -Format "Mm-dd-yyyy_hh-mm-ss"
$Columns = "WebURL" + ";" + "List Default View URL" + ";" + "List Title" + ";" + "Item URL" + ";" + "Name" + ";" + "Type" +";"+"Permission"
$logFile = "C:\UniquePermissions" + $logtime + ".csv" # Log Location
$columns | out-file -filepath $logfile -append$site=Get-SPSite $url
$Webs = $site.AllWebs
foreach($web in $webs)
{if($web.HasUniqueRoleAssignments)
{
$WebRoles = $Web.RoleAssignments
foreach($WebRole in $WebRoles)
{$WebRoleBindings = $WebRole.RoleDefinitionBindings
foreach($WebRoleBinding in $WebRoleBindings)
{if($webrole.Member.IsDomainGroup -eq $null)
{
$output = $web.url + ";" + ";" + ";" + ";" + $WebRole.member.Name + ";" + "SharePoint Group" + ";" + $WebRoleBinding.Name
$output | out-file -filepath $logfile -append
}
else
{
if($webrole.Member.IsDomainGroup)
{
$output = $web.url + ";" + ";" + ";" + ";" + $WebRole.member.Name + ";" + "Domain Group" + ";" + $WebRoleBinding.Name
$output | out-file -filepath $logfile -append
}
else
{
$output = $web.url + ";" + ";" + ";" + ";" + $WebRole.member.UserLogin + ";" + "Domain User" + ";" + $WebRoleBinding.Name
$output | out-file -filepath $logfile -append
}
}
}}
}
$lists = $web.Lists
foreach($list in $lists)
{
if($list.HasUniqueRoleAssignments)
{$ListRoles = $list.RoleAssignments
foreach($listRole in $ListRoles)
{
$ListRoleBindings = $listrole.RoleDefinitionBindings
foreach($ListRoleBinding in $ListRoleBindings)
{
if($listrole.Member.IsDomainGroup -eq $null)
{
$output = $web.url + ";" + $rooturl + $list.DefaultViewUrl + ";" + $list.Title + ";" + ";" + $ListRole.Member.Name + ";" + "SharePoint Group" + ";" + $ListRoleBinding.Name
$output | out-file -filepath $logfile -append
}
else
{
if($listrole.Member.IsDomainGroup)
{
$output = $web.url + ";" + $rooturl + $list.DefaultViewUrl + ";" + $list.Title + ";" + ";" + $ListRole.Member.Name + ";" + "Domain Group" + ";" + $ListRoleBinding.Name
$output | out-file -filepath $logfile -append
}
else
{
$output = $web.url + ";" + $rooturl + $list.DefaultViewUrl + ";" + $list.Title + ";" + ";" + $ListRole.Member.UserLogin + ";" + "Domain User" + ";" + $ListRoleBinding.Name
$output | out-file -filepath $logfile -append}
}
}
}}
$Uniqueitems = $list.GetItemsWithUniquePermissions()
foreach($Uniqueitem in $Uniqueitems)
{$item = $list.GetItemById($Uniqueitem.id)
$itemRoles = $item.RoleAssignments
foreach($itemRole in $itemroles)
{
$itemRoleBindings = $itemrole.RoleDefinitionBindings
foreach($itemrolebinding in $itemRoleBindings)
{
if($itemrole.Member.IsDomainGroup -eq $null)
{
$output = $web.url + ";" + $rooturl + $list.DefaultViewUrl + ";" + $list.Title + ";" + $rooturl+ "/" +$item.Url + ";" + $itemRole.Member.Name + ";" + "SharePoint Group" + ";" + $itemRoleBinding.Name
$output | out-file -filepath $logfile -append
}
else
{
if($itemrole.Member.IsDomainGroup)
{
$output = $web.url + ";" + $rooturl + $list.DefaultViewUrl + ";" + $list.Title + ";" + $rooturl+ "/" +$item.Url + ";" + $itemRole.Member.Name + ";" + "Domain Group" + ";" + $itemRoleBinding.Name
$output | out-file -filepath $logfile -append}
else
{
$output = $web.url + ";" + $rooturl + $list.DefaultViewUrl + ";" + $list.Title + ";" + $rooturl+ "/" +$item.Url + ";" + $itemRole.Member.UserLogin + ";" + "Domain User" + ";" + $itemRoleBinding.Name
$output | out-file -filepath $logfile -append
}
}}
}}
}
$web.Dispose()
}
$site.Dispose()
This will not work for SharePoint 2007, I have written one for SharePoint 2007 too, if someone needs it then leave a comment and I will share it out.
Comments
- Anonymous
May 21, 2015
Good one Harmeet, very useful when site has number of unique permissions?? - Anonymous
January 12, 2016
Harmeet, can you post the SharePoint 2007 version of this script? It would be very helpful to me. Thanks! - Anonymous
February 06, 2016
Nice Thanks... - Anonymous
March 09, 2016
So you have this nice script hear to do what I need to do; however, for the ones of us that are less informed how and where do you use it? is it a stand alone script? added to a webpage, placed on a SharePoint page in your collection???? thank you for this answer. - Anonymous
March 09, 2016
Disregard Comment figured it out :)