Using Logparser + Eventcomb to find malware
During the course of these Conficker / Downadup issues we typically see cases that started because accounts are getting locked out. I pause briefly here to point out that account lockouts are the work of the devil and are a sorry excuse for most people to not use a complex password policy. So it seems that these cases for the most part are slowing down however customers are still looking for those few machines that fall between the cracks that are still causing account lockouts when they turn back on their account lockout policy (once again because they don’t want to use complex passwords).
So the tool to turn towards is the account lockout tools. Part of this toolset is eventcombmt (mt stands for multithreaded).
Eventcombmt is cool for all sorts of things but the only thing we are interested in is the built in Account Lockout Search. Select Searches>Built In Searches>Account Lockouts. You could also change your output directory if you want, the default is C:\temp.
Once you selected this it should put in the right event id’s and locate and select all your DC’s. Click Search and it’s off searching through all your DC’s Security Event Logs and dumping all the pertinent info to DomainControllername.txt files in the c:\temp directory.
While your waiting for this go download log parser. Install that you may want to make sure it’s in your path afterwards for this to work try typing logparser from a cmd prompt. Once you have logparser in place and Eventcomb has finished and output all of your DC’s .txt files then you will want to run the following logparser query in the directory with the .txt’s
Once that’s complete run the following in the directory with all your textfile outputs from the DC’s
logparser -i:textline "SELECT SUBSTR(SUBSTR(Text, ADD(INDEX_OF(Text, 'Address: '), 8)), 1, INDEX_OF(SUBSTR(Text, ADD(INDEX_OF(Text, 'Address: '), 9)),' ')) AS IPAddr INTO addrs.csv FROM *.txt"
Revision 5/8/09 You may need to use this instead of the Addresses are all at the end of the line:
logparser -i:textline "SELECT SUBSTR(Text, LAST_INDEX_OF(Text, 'Address: ')) AS IPAddr INTO addrs.csv FROM *.txt"
This should create a file called addrs.csv which has all of the IP addresses that has caused by password attempts. There will be lines for each attempt so we need to parse this down a little more to give use a column with IP address and a column with the number of bad password attempts so we will run the following logparser query next:
logparser -i:csv -o:csv "select IPaddr, count (*) as hits into final.csv from addrs.csv group by IPaddr order by hits desc"
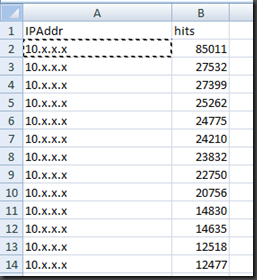
This should leave us with a final.csv file which has 2 columns one for the IP address and another for the amount of times we have seen that IP address causing bad password attempts in our security event logs across our DC’s. In the case below that first IP had caused 85k bad password attempts guessing that machine has a problem :) …
Seeing we’ve primarily used this for Conficker it seems the following line works well to output just a list of IP addresses with no header on the file and no hits.
logparser -i:csv -o:csv -headers:OFF "select distinct IPaddr into ips.txt from addrs.csv"
You can then take the ips.txt file and use the import function on Mcafee’s Conficker Detection Tool to scan all of these IP’s quickly to see if they are infected with Conficker or not.
Update 1: 4/9/2009 Totally reworked this thanks to Neil Carpenter and some better logparser logic to filter this better and have a much cleaner final output. Also dropped need for .csv files as we are filtering using textline input instead.
Update 2: 7/10/2009 Added new logpaser query to output just IP’s to file with no hits etc which you can then easily import to Mcafee’s Conficker Detection Tool
Comments
Anonymous
November 22, 2009
Thanks, this is very useful and helpful.Anonymous
November 26, 2009
Thank you, very nice article. Definitely adding this to the toolbox!Anonymous
December 23, 2009
Nice writeup -- I've worked on many networks with conficker -- over the past year or so likely around 100,000 PCs give or take a few hunhdred. A "must have" for sure.Anonymous
February 16, 2010
um vírus que volta sempre atacou meu computadoe, abre tudo, menos hotmail e msnAnonymous
February 19, 2010
I've walked into a network where the group policy recommendations were left half done. can i safely remove any gp's as described athttp://support.microsoft.com/kb/962007#Mitigationsteps ??