Exchange Online Protection - Spear Phishing Attack, ASF and ATP
By: Caio Ribeiro Cesar
In this post, I will be discussing some practices used by attackers in order to get authentication information for VIP users.
This is a common practice called "spear phishing", or individual phishing - first, attackers get to know the victim (usually a CISO/CTO or someone that holds important data). Then, they start the attack.
These methodologies are evolving. Spear phishing are usually mixed with social engineering in order to create a relationship between the attacker and the victim - as getting a call about the email being sent with important information available on a link that they need to click. When this email is delivered, the victim usually trusts the attacker and does not hesitate to access the information.
Let's first understand how a phishing attack is done, so we can discuss individual attacks.
1) We need a website. Maybe a copy of a reliable site, as a methodology for people to trust the information they see. Attackers add the site to the email body (or maybe a site, forum or anywhere people can click and be lurked to the attacker)
Attackers create a clone of reliable websites, or they create their own. Spear phishing usually relies on cloning as they are more precise on a single attack rather than expecting "some hits" from a 10k/100k mail list.
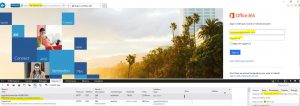
The example below is a clone of the old O365 portal, created by me back in 2015 (https://c4iocesar.wordpress.com/2015/08/24/exchange-online-protection-spear-phishing-attack-asf-e-safe-links/).
The attacker would simply create a DNS entry for the external IP address of this website. The webpage is identical to the old "login.microsoftonline.com".
After the website is cloned and published, the attacker will build a nice written email with this information. It's important to understand that they usually use spoofs, so these emails are sent similar to the original sender - and this is why we should use features such as SPF/Dkim/DMARC.
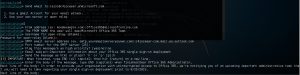
In the simulation below, I'm adding my webserver to the email, spoofing the sender so they can be tricked by opening and clicking on my email:
*As much as I can create a valid clone, published externally and add a real spoof in the attack, I want to keep my Kali Linux Lab in Azure. If you are a Pentester, please let the azure team know in the procedure of creating the VM.
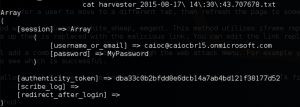
The victim then would access the URL from my email, and the HTTP POST would be added to my webserver DB.
How can administrators prevent end users from clicking on these emails?
Exchange Online Protection has not only tools that can prevent these emails from arriving, but also features that can prevent end users from accessing the information.
1) ASF
Advanced SPAM Filter acts on the SPAM Filter for ExO. It acts by reading the email body and preventing these emails from reaching the /Inbox. For example:
This was added as a Spam Confidence Level of 6, due to the "Numeric IP in URL" action. This methodology is commonly used by attackers in order to trick users by clicking on a fake URL.
- ATP (Safe Links)
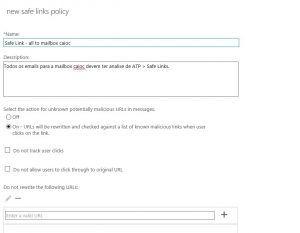
Advanced Threat Protection has become common for larger enterprises. This avoids users from reaching out to unsafe links. When the end user tries to reach out the URL, it's validated by a MS server so we are sure this URL is valid/does not contain a malware, redirect or being used as a phishing endpoint. The end user is alerted and these actions can be monitored by the company admin:
As we can see below, when the website is redirected to a phishing endpoint, we are first routed to ".safelinks.protection.outlook.com":
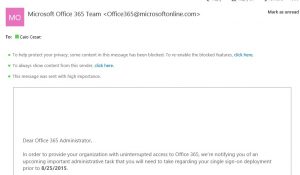
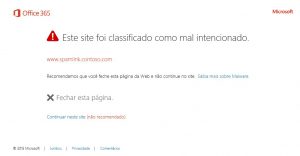
Information received by the end user (language can be customized):
Admin reporting for the ATP:
++++++++++++++++++++++++++++++++++++++++++++++
This is a post translation for the 2015 article written in Portuguese. Today, ATP has evolved, together with multiple Microsoft (and third party) technologies. For Microsoft, I indicate going through the CISO workshop [https://docs.microsoft.com/en-us/office365/securitycompliance/ciso-workshop
], together with the Cybersecurity Reference Architecture (MCRA) for integrated solutions.
Other solutions that can help you and your organization to be ready for these attacks:
1) SecureScore can help you (as the admin) to understand your security score for O365.
2) Phishing Simulations (phishing campaigns) are available in O365. This can help to prepare your organization culture.