Blocking Legacy Clients with Azure AD Conditional Access
Hi,
A great new feature has been added to Azure AD Conditional Access that provides the ability to block access from legacy clients (In preview at the time of writing this post). I've had many customers ask for this capability so I thought I'd put together a quick run though on how to configure it and the user experience for a legacy client (Outlook 2010).
The "legacy clients" we are referring to are the non ADAL\Modern-Auth clients that are using legacy authentication methods (more information here) A good example being Basic Auth over SSL used with Outlook 2010 and below. This presented a challenge for some customers as they would configure Conditional Access Policies and they wouldn't apply to users using these older clients (and therefore have to use more clunky methods to block these clients).
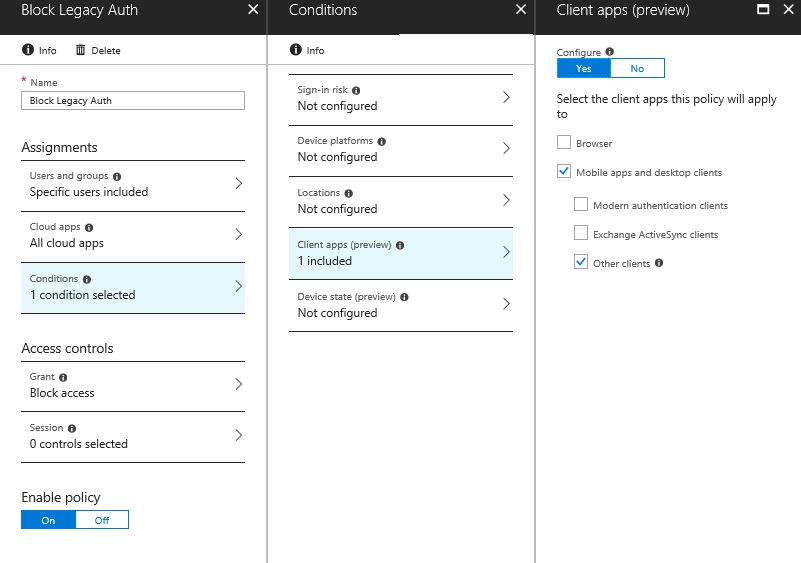
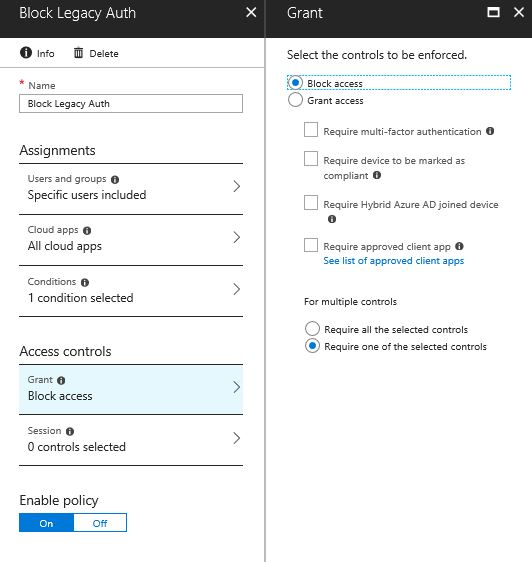
Below is an example of a Conditional Access Policy that blocks access from all legacy clients to all Microsoft Cloud Applications. I have created a Conditional Access Policy that is targeted to group of users and all cloud applications. (please target Conditional Access Policies carefully and always test on a small subset of users\applications before rolling out! ).
Within the "Conditions" > "Client apps (preview)" blade there is now a "Other clients" checkbox.
As this is a "Condition" it allows you to target all "other clients" aka legacy clients and apply a "Block" without affecting your more modern ADAL clients (e.g. Office 2016).
NOTE: There is also a "Modern authentication clients" condition which allows you to target a policy at ADAL\Modern Auth clients.
Before enabling the policy you need to be aware of a couple of things (more info here).
- Once enabled this policy could take up to 24 hours to apply.
- Configuring this policy for “Other clients” will apply to all clients that are using legacy authentication methods. You should use this to test on a small subset of users\apps and once you are clear on what impact the policy will have then consider rolling it out to a wider scope.
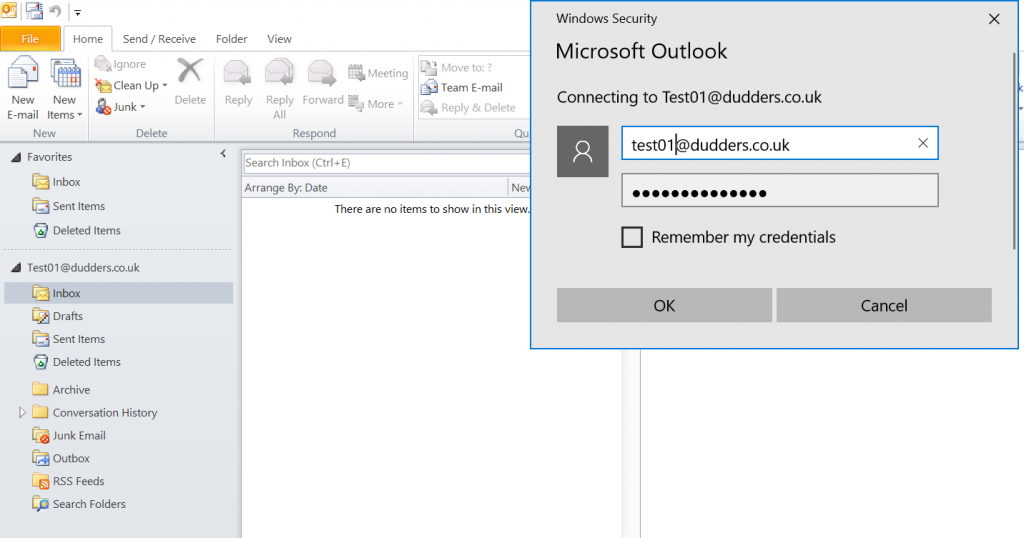
Now enabled, the next day I open Outlook 2010 and I'm prompted for credentials. Despite entering correct credentials the authentication is denied and user is re-prompted. I would recommend communications to helpdesk and users in advance so that users don't mistakenly think there password is incorrect. Outlook 2016 and other Modern Authentication Clients continue to work as expected.
Hope thats useful!
MD