LDAP calls made from the Unix client query incorrect login shell attribute
Recently while working on an issue where we got an issue where the Users once logged into Linux client were getting incorrect login shell. Changing the Login Shell in Active Directory (from Unix Attribute Tab), did not work as the user were still getting default login Unix Shell.
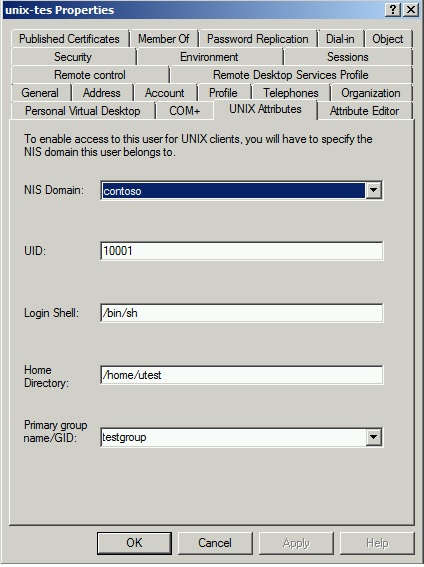
For example ==> This is the default view from ADUC ( Unix attribute tab)
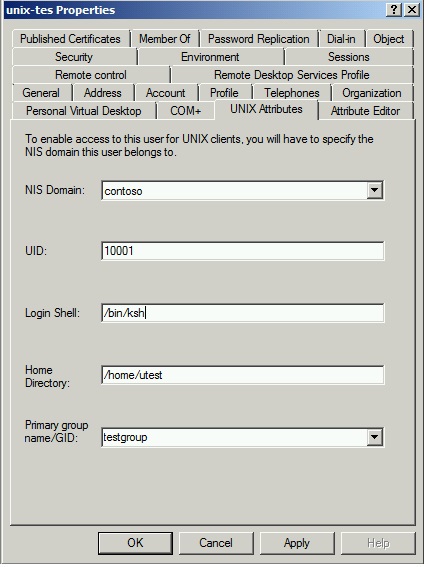
Default Login Shell value is /bin/sh. Then we changed the value to /bin/ksh but still the user was still getting /bin/sh shell while logging on the Linux Client machine.
Environment: Windows DC is configured as NIS Master Server and client is using Kerberos for Authentication.
Since the Login Shell attribute information is stored in the Active Directory, we ensure that AD Replication is good. Linux client are making LDAP calls to the Domain Controller to query various information, including login shell.
From the Network traces to check on the calls made by the Linux client to the Domain Controller for querying the information. And it revealed that client is requesting for msSFU30LoginShell attribute and not for loginshell attribute.
Snippet from netmon:
+ Filter:
(&(sAMAccountName=unixtes)(objectclass=user))
- Attributes: ( objectClass )( sAMAccountName )( userPassword )(uidNumber )( gidNumber )( gecos )( unixHomeDirectory )( msSFU30LoginShell )( userPrincipalName )( displayName )( memberOf )( nsUniqueId )( modifyTimestamp )( uSNChanged )( shadowLastChange )( shad
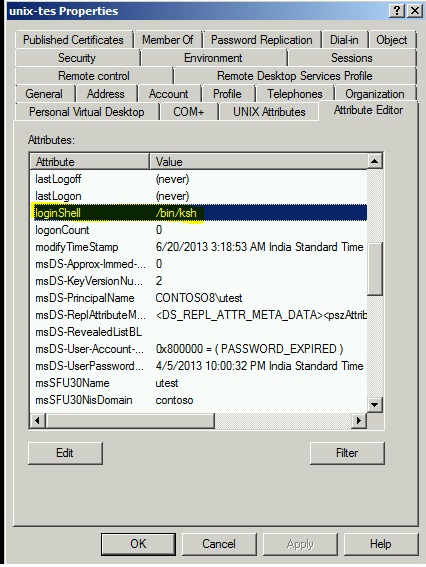
We also confirmed that in Active directory store the information is stored in the attribute called loginShell and not in the attribute – msSFU30LoginShell. Actually, when we use to extend the schema on Windows 2003, SFU 3.5 by installing “Server for NFS” , the attribute was called mssfu30Loginshell.
Hence the issue was, the client is requesting a wrong attribute which does not have value and hence not getting any response. Based on further research, we found that sssd.conf file was configured to pass this information on the Unix client.
- ldap_user_shell= msSFU30LoginShell
We changed it to the loginShell and now we see that client is sending ldap query for loginShell and got the correct value in return - /bin/ksh.
Snippet from netmon:
- Filter: (&(uidNumber=10001)(objectclass=posixAccount))
- Attributes: ( objectClass )(uid )( userPassword )( uidNumber )( gidNumber )( gecos )( homeDirectory )(loginShell )( krbPrincipalName )( cn )( memberOf )( nsUniqueId )( modifyTimestamp)( uSNChanged )( shadowLastChange )( shadowMin )( shadowMax )( shadowWarn
Please refer following documents for more information.
https://technet.microsoft.com/en-us/library/bb463172.aspx
https://msdn.microsoft.com/en-us/library/windows/desktop/ms676844(v=vs.85).aspx