Azure Log Analytics: Sorting Events
Jon (who also works at Microsoft) was asking me how to use an ‘or’ to filter EventIDs, I thought I’d add some syntax examples.
We have seen in the last post that you can get Event or SecurityEvent details. I’ll use SecurityEvents as the example but you can use Events if you prefer. All examples are once again from the Advanced Analytics portal.
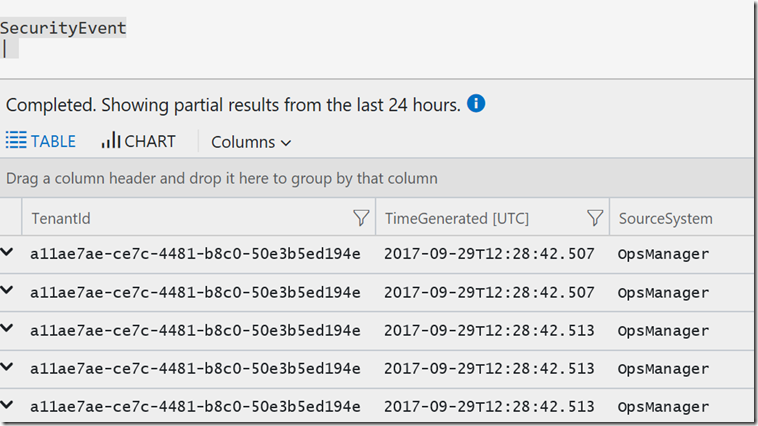
We could just type:- SecurityEvent and get a very long list (as I was scoped to 24hrs) 10k events were returned, so only partial results were highlighted. You can reduce the time scope from the portal or in code or you can reduce the Events that are returned. The Limit syntax is again a best practise.
So instead you could type:
SecurityEvent
| summarize count() by EventID
Giving you a nice list of EventIDs to pick, such as 4768 which I’ve used with the Where syntax.
SecurityEvent
| where EventID == 4768
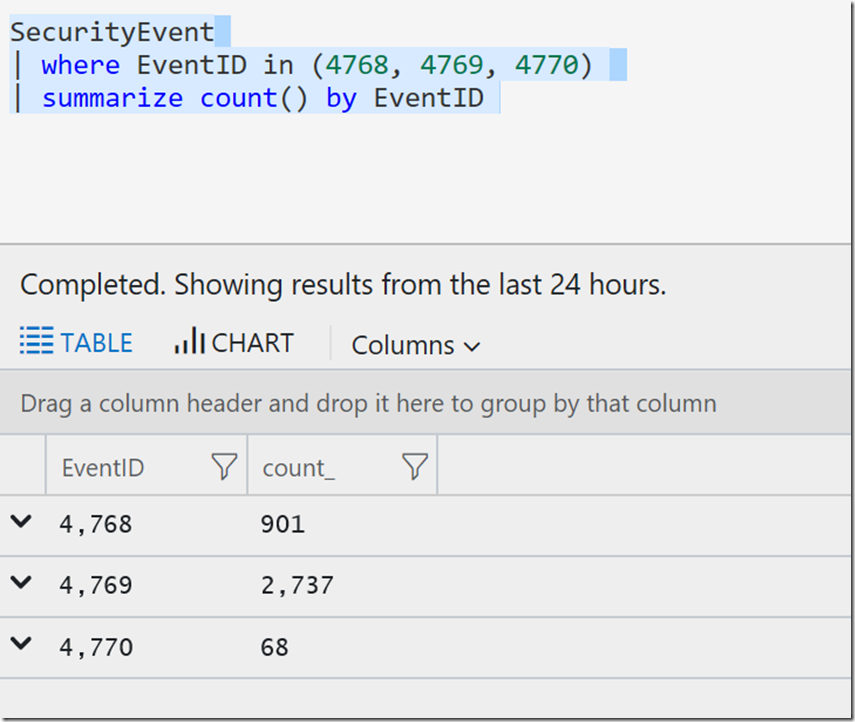
You can also introduce the ‘in’ option to get a list, I also added a summarize count to show how many of each type were returned.
SecurityEvent
| where EventID in (4768, 4769, 4770)
| summarize count() by EventID
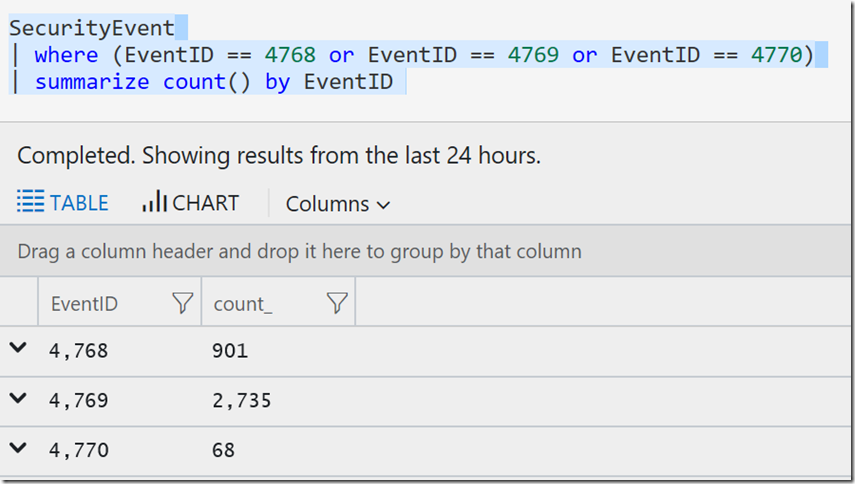
So to the question Jon asked, how to use an OR with EventIDs, you can do this:
SecurityEvent
| where (EventID == 4768 or EventID == 4769 or EventID == 4770)
| summarize count() by EventID
The same method works with ‘and’ as well.
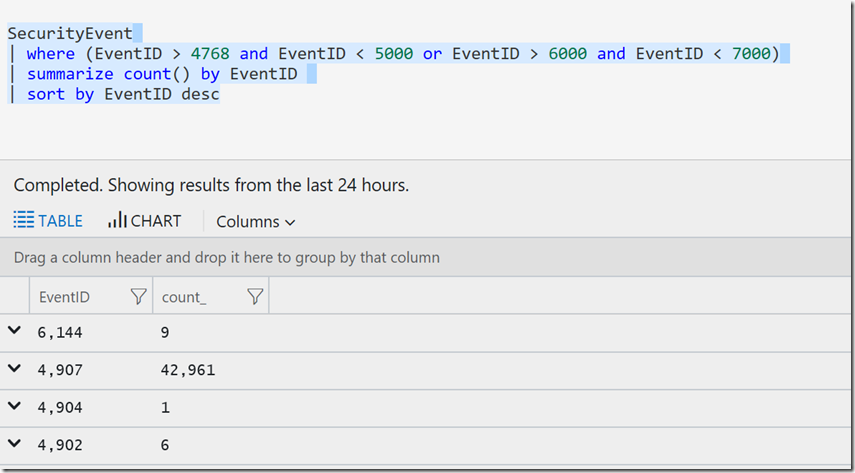
Also if you happen to have a range of EventIDs then you can do the following (I also sorted this to show a descending list):
SecurityEvent
| where (EventID > 4768 and EventID < 5000 or EventID > 6000 and EventID < 7000)
| summarize count() by EventID
| sort by EventID desc
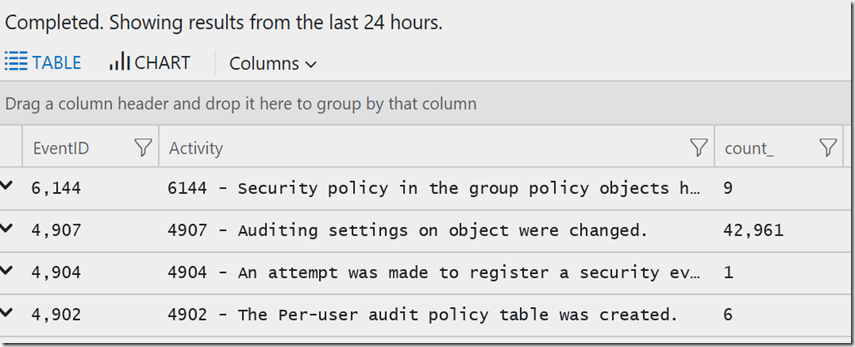
Of course the EventID is a good piece of info but you probably want one or more other columns, you can add others (and intellisense will prompt you) in a comma separated list, such as here where I've added ‘activity’:
SecurityEvent
| where (EventID > 4768 and EventID < 5000 or EventID > 6000 and EventID < 7000)
| summarize count() by EventID , Activity
| sort by EventID desc