Change permissions at the organization or collection-level
TFS 2018
Several permissions are set at the organization or collection level. You can grant these permissions by adding a user or group to the Project Collection Administrators group. Or, you can grant select collection-level permissions to a custom security group or to a user.
A project collection is the container for several projects that share resources. For more information about projects and project collections, see About projects and scaling your organization.
See the following articles for related information:
- Request an increase in permission levels
- Change project-level permissions
- Add or remove users or groups, manage security groups
- Set object-level permissions
- Look up a project collection administrator
- Look up the organization owner
Note
Security groups belong to the collection level, even if they only access a specific project. Some groups may be hidden in the web portal depending on user permissions. However, you can discover the names of all groups in an organization using the REST APIs. For more information, see Add and manage security groups.
Collection-level permissions
The following table lists the permissions assigned at the organization or collection-level. All of these permissions, except for the Make requests on behalf of others permission, are granted to members of the Project Collection Administrators group. For a description of each permission, see Permissions and groups reference, Groups.
General
- Alter trace settings
- Create new projects
- Delete team project
- Edit instance-level information
- View instance-level information
Service Account
- Make requests on behalf of others
- Trigger events
- View system synchronization information
Boards
- Delete field from organization or account
Repos (TFVC)
- Administer shelved changes
- Administer workspaces
- Create a workspace
Pipelines
- Administer build resource permissions
- Manage build resources
- Use build resources
- View build resources Test Plans
- Manage test controllers
Note
The permission to add or remove organization or collection-level security groups, add and manage organization or collection-level group membership, and edit collection and project-level permission ACLs is assigned to all members of the Project Collection Administrators group. It isn't controlled by a permissions surfaced within the user interface.
Prerequisites
- To manage permissions or groups at the organization or collection level, you must be a member of the Project Collection Administrators security group. If you created the organization or collection, you are automatically added as a member of this group. To get added to this group, you need to request permissions from a member of the Project Collection Administrators group. See Look up a project collection administrator.
- If want to add security groups defined in Microsoft Entra ID or Active Directory, make sure those are first defined. To learn more, see Add Active Directory / Microsoft Entra users or groups to a built-in security group.
Note
Users granted Stakeholder access, won't be able to access select features even if granted permissions to those features. To learn more, see Stakeholder access quick reference.
Add members to the Project Collection Administrators group
You can add users who've been added to a project, organization, or collection to the Project Collection Administrators group, or any other group at the organization or collection-level. To add a custom security group, first create the group as described in Add or remove users or groups, manage security groups.
Here we show how to add a user to the Project Collection Administrators group. The method is similar to adding a Microsoft Entra ID or Active Directory group.
Open the web portal and choose the project where you want to add users or groups. To choose another project, see Switch project, repository, team.
Choose the
 gear icon to open the administrative context.
gear icon to open the administrative context.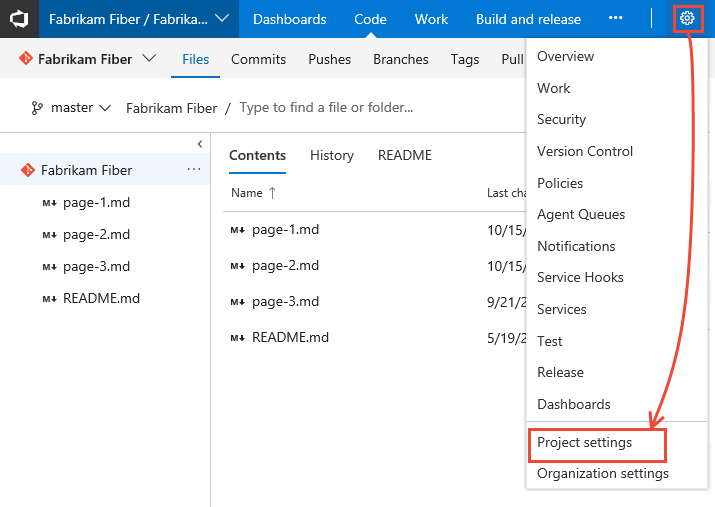
Choose Security, Project Administrators group, Members, and then Add.
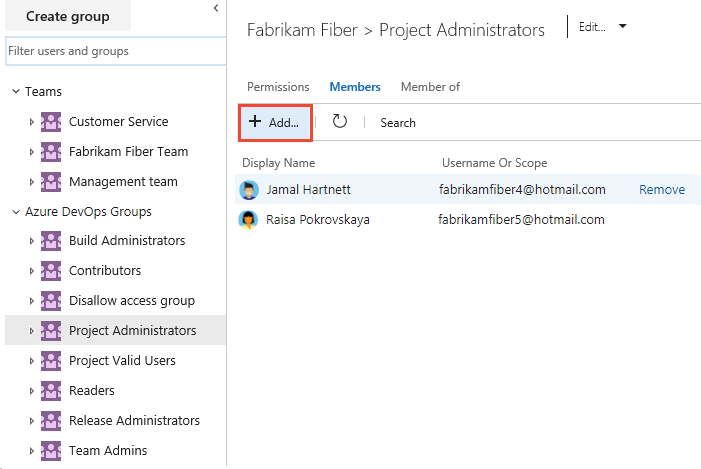
Enter the name of the user account into the text box. You can enter several identities into the text box, separated by commas. The system automatically searches for matches. Choose the match(es) that meets your choice.
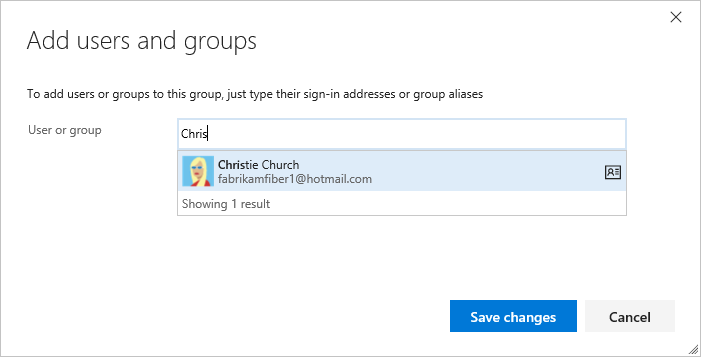
Note
Users that have limited access, such as Stakeholders, won't be able to access select features even if granted permissions to those features. To learn more, see Permissions and access.
Choose Save changes. Choose the
 refresh icon to see the additions.
refresh icon to see the additions.
Change permissions for a group
You can change the permissions for any organization or collection-level group, except the Project Collection Administrators group. You can add security groups to a collection in a similar manner to adding a security group to a project. See Add or remove users or groups, manage security groups. To understand permission assignments and inheritance, see About permissions, Permission states.
Open the Security page as described in the previous section, Add a user or group to the Project Collection Administrators group.
From the Security page, choose the group whose permissions you want to change.
For example, here we choose the Stakeholders Limited group, and change several permissions.
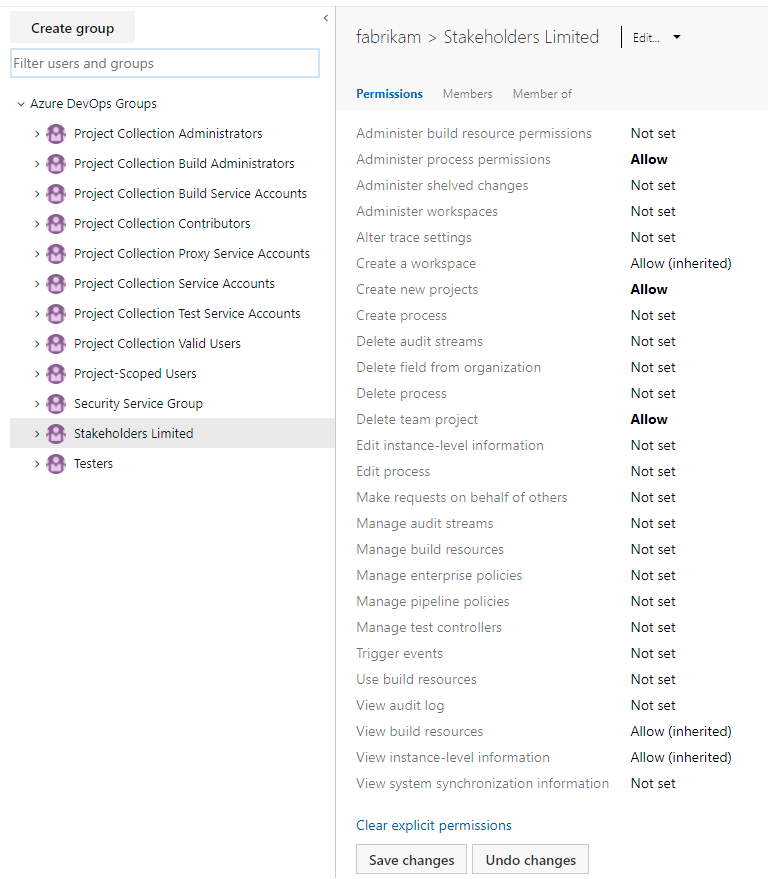
Choose Save changes.
Change permissions for a user
You can change the collection-level permissions for a specific user. To understand permission assignments and inheritance, see About permissions, Permission states.
Open the Security page as described in the previous section, Add a user or group to the Project Administrators group.
From the Security page, in the Filter users and groups text box, enter the name of the user whose permissions you want to change.
Change change the assignment for one or more permissions.
For example, here we change the Edit project-level information for Christie Church.
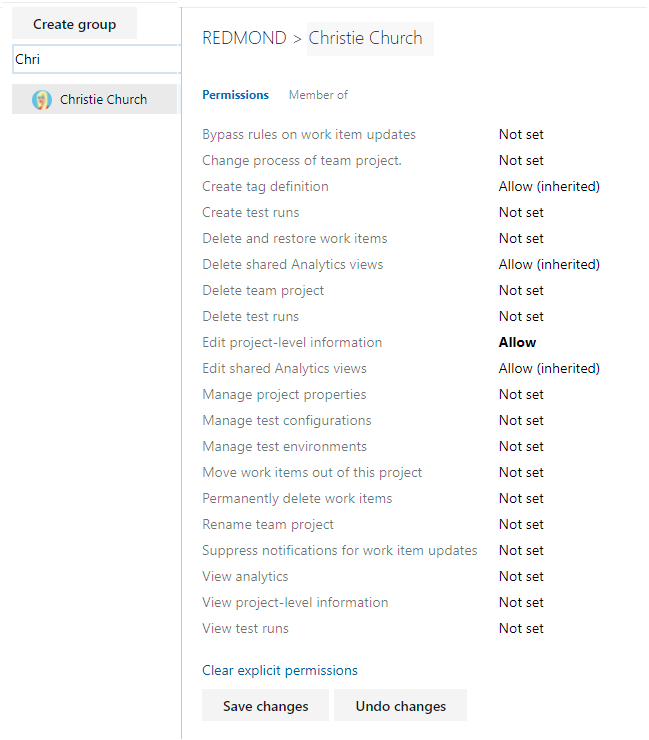
Choose Save changes.
On-premises deployments
For on-premises deployments, see these additional articles:
If your on-premises deployment is integrated with SQL Server Reports, you'll need to manage membership for those products separately from their websites. See Grant permissions to view or create SQL Server reports in TFS.
FAQs
Q: When do I need to add someone to the Project Collection Administrator role?
A: It varies. For most organizations that use Azure DevOps, Project Collection Administrators manage the collections that members of the Team Foundation Administrators group create. Members of the Project Collection Administrators group don't create the collections themselves. Project collection administrators also do many operations required to maintain the collection. Operations include creating team projects, adding users to groups, modifying the settings for the collection, and so on.
Q: What are the optimal permissions to administer a project collection across all of its components and dependencies?
A: Project collection administrators must be members of the following groups or have the following permissions:
Team Foundation Server: A member of the Project Collection Administrators group, or have the appropriate collection-level permissions set to Allow.
SharePoint Products: If the collection is configured with a site collection resource, then a member of the Site Collection Administrators group.
Reporting Services: If the collection is configured with reporting resources, then a member of the Team Foundation Content Manager group.
Q: I'm an admin, but I don't have permission to add a Project Collection Administrator. What do I need?
A: The following permissions are required:
You must be a Project Collection Administrator, or your View Server-Level Information and Edit Server-Level Information permissions must be set to Allow.
To add permissions for SharePoint Products, you must be a member of the Site Collection Administrators or Farm Administrators groups for SharePoint Products.
To add permissions for Reporting Services, you must be a member of the Content Managers or Team Foundation Content Managers groups for Reporting Services.
Important
To perform administrative tasks like creating project collections, your user requires administrative permissions. The service account that the Team Foundation Background Job Agent uses must have certain permissions granted to it. For more information, see Service accounts and dependencies in Team Foundation Server and Team Foundation Background Job Agent.