Authentication overview
TFS 2017 | TFS 2015
Choose a method to securely access the code in Azure Repos, Azure DevOps Server 2019, or Team Foundation Server (TFS) Git repositories. Use these credentials with Git at a command prompt. These credentials also work with any Git client that supports HTTPS or SSH authentication. Limit the scope of access and revoke these credentials when they're no longer needed.
Important
Azure DevOps no longer supports Alternate Credentials authentication since the beginning of March 2, 2020. If you're still using Alternate Credentials, we strongly encourage you to switch to a more secure authentication method (for example, personal access tokens). Learn more.
Azure DevOps Server was formerly named Visual Studio Team Foundation Server.
Tip
Using Visual Studio? Team Explorer handles authentication with Azure Repos for you.
Note
Visual Studio 2019 version 16.8 and later versions provide a new Git menu for managing the Git workflow with less context switching than Team Explorer. Procedures provided in this article under the Visual Studio 2019 tab provide information for using the Git experience as well as Team Explorer. To learn more, see Side-by-side comparison of Git and Team Explorer.
Authentication comparison
| Authentication Type | When to use | Secure? | Ease of setup | Additional tools |
|---|---|---|---|---|
| Personal access tokens | You need an easy to configure credential or need configurable access controls | Very secure (when using HTTPS) | Easy | Optional (Git credential managers) |
| SSH | You already have SSH keys set up, or are on macOS or Linux | Very secure | Intermediate | Windows users will need the SSH tools included with Git for Windows |
Personal access tokens
Personal access tokens (PATs) give you access to Azure DevOps and Team Foundation Server (TFS), without using your username and password directly. These tokens have an expiration date from when they're created. You can restrict the scope of the data they can access. Use PATs to authenticate if you don't already have SSH keys set up on your system or if you need to restrict the permissions that are granted by the credential.
Use Git Credential Manager to generate tokens
The Git Credential Manager is an optional tool that makes it easy to create PATs when you're working with Azure Repos. Sign in to the web portal, generate a token, and then use the token as your password when you're connecting to Azure Repos.
PATs are generated on demand when you have the credential manager installed. The credential manager creates the token in Azure DevOps and saves it locally for use with the Git command line or other client.
Note
Current versions of Git for Windows include the Git credential manager as an optional feature during installation.
SSH key authentication
Key authentication with SSH works through a public and private key pair that you create on your computer. You associate the public key with your username from the web. Azure DevOps will encrypt the data sent to you with that key when you work with Git. You decrypt the data on your computer with the private key, which is never shared or sent over the network.
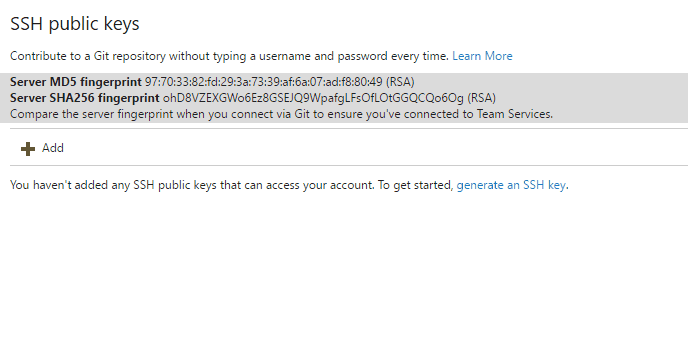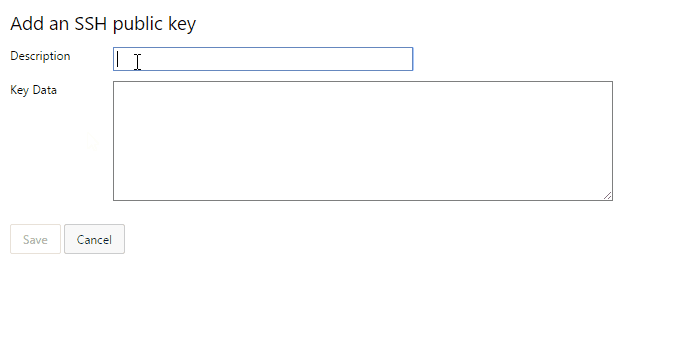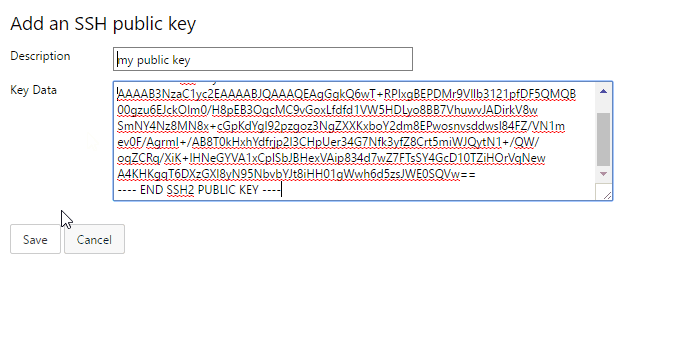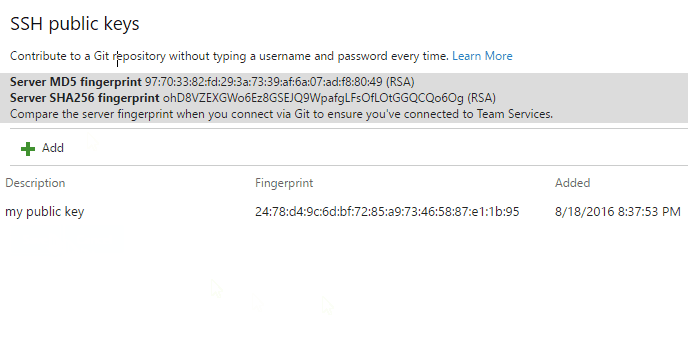
SSH is a great option if you've already got it set up on your system—just add a public key to Azure DevOps and clone your repos using SSH. If you don't have SSH set up on your computer, you should use PATs and HTTPS instead - it's secure and easier to set up.
Learn more about setting up SSH with Azure DevOps
OAuth
Use OAuth to generate tokens for accessing REST APIs. The Accounts and Profiles APIs support only OAuth.
- SSH authentication to generate encryption keys when you use Linux, macOS, or Windows running Git for Windows and can't use Git credential managers or personal access tokens for HTTPS authentication.