Granting Tenant Admin Consent for Microsoft Graph Explorer
Introduction
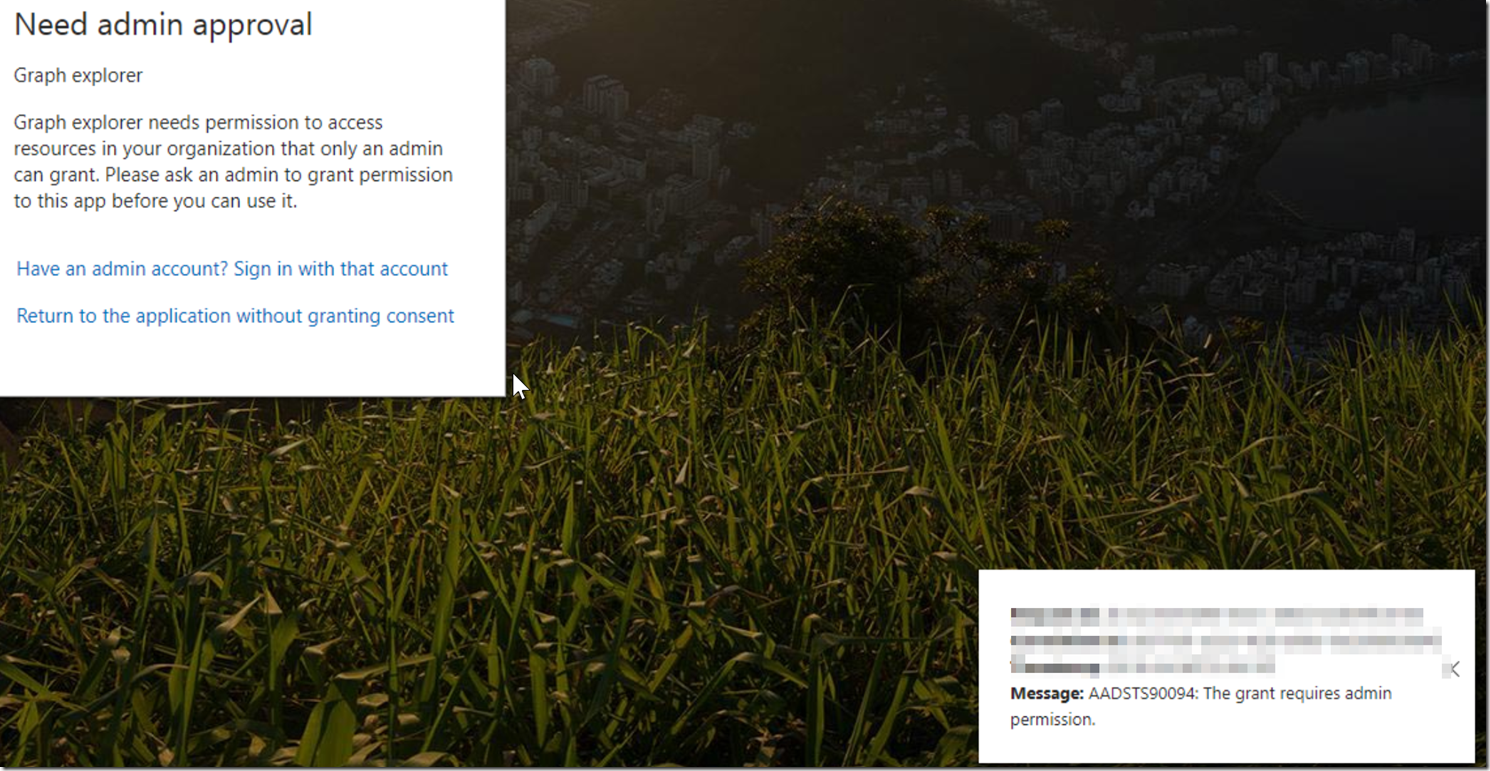
This post is meant for users who are trying to utilize the Microsoft Graph Explorer but are getting an error regarding admin consent. This error is described in the picture below :
Giving Consent for All Users for Microsoft Graph Explorer
This error is occurring because the user trying to use the graph explorer is trying to utilize a v2 permission that requires admin consent. The permissions/scopes regarding the v2 endpoint are described in the link here : https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-v2-scopes
Resolution
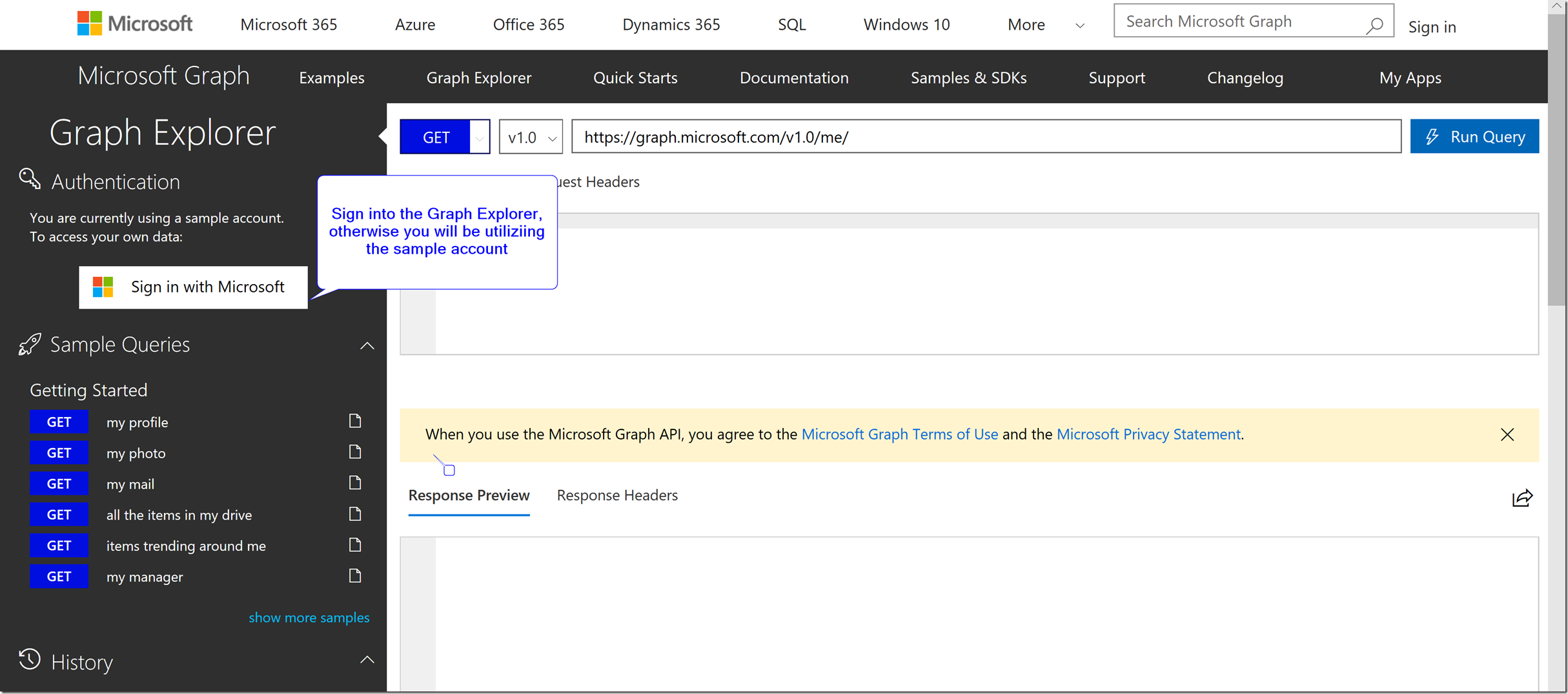
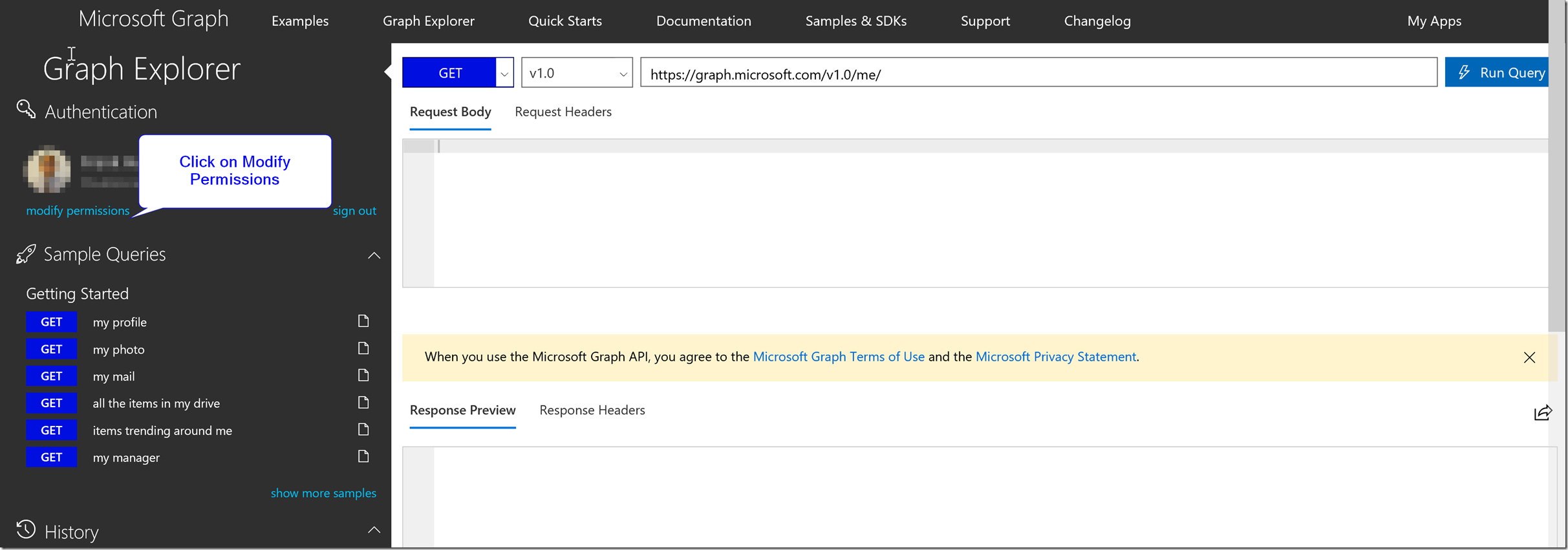
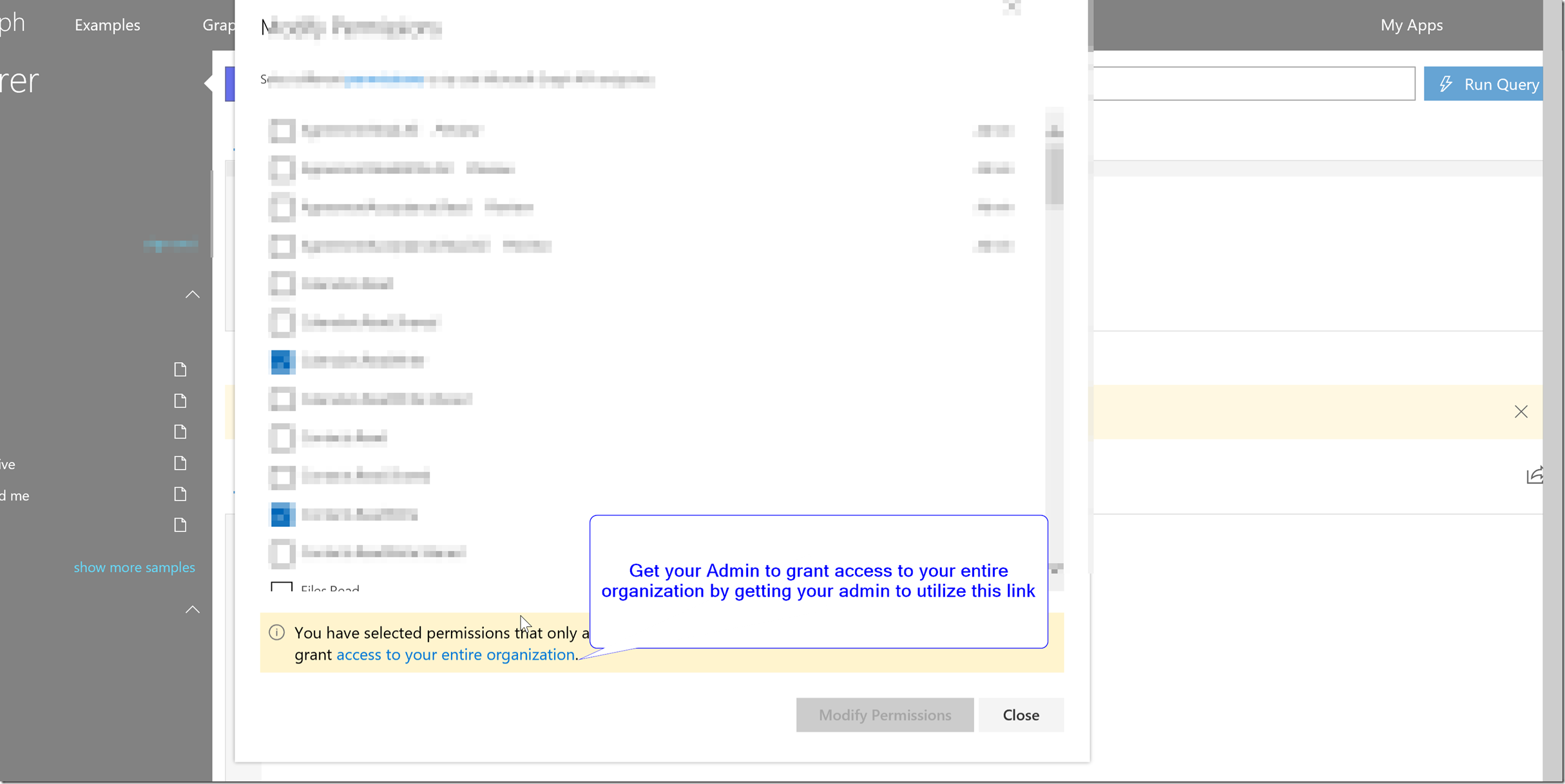
To resolve this issue, the Microsoft Graph explorer provides a convenient pre-developed URL for users to give the Global Admin of the tenant in order to grant admin consent on behalf of all users in the tenant. This is currently the only way to let users use the Microsoft Graph Explorer to get access to the Microsoft Graph API with permissions that require Admin Consent.
This link can be found by following the steps described in the pictures below.
Comments
- Anonymous
June 29, 2018
I cannot get past the Sign in With Microsoft link without seeing the: "Need admin approval" error message with error code: AADSTS90094.Is there a way to get to the link through the portal? Or can you just share the link here?- Anonymous
June 29, 2018
Hey, I'm sorry but I don't understand the issue. You'll need to be an Azure Active Directory Global Admin to grant you the approval. Please file a support ticket for further help as it looks like it may require a bit more digging to determine what's going on.Edit: After rereading your post, I think the issue is that you're admin hasn't allowed users to grant consent on behalf of themselves. Please refer to this article for more information on that error : https://blogs.msdn.microsoft.com/aaddevsup/2018/05/08/receiving-aadsts…admin-permission/
- Anonymous
- Anonymous
August 22, 2018
Hi Frank, Thank you for your article. Do you know how can I revoke the permission(admin permissions) after granted ? - Anonymous
August 22, 2018
Hey, so you should be able to find the service principal in the azure portal. Go to portal.azure.com. Then go to Azure Active Directory, and then go to enterprise applications. From there you should see Graph Explorer, delete the enterprise application and this will remove your service principal, meaning you are removing your permissions. If you have anymore issues with this, please file a support ticket and one of the support engineers will reach out to you.- Anonymous
August 28, 2018
Thank you Frank,after I removed graph explorer from enterprise application , can I still use user consent permission from Microsoft graph ?- Anonymous
August 29, 2018
Yes, the users can still consent on behalf of themselves if the AAD tenant allows users to consent and the user has to correct privileges/roles to perform the actions they are asking to perform.
- Anonymous
- Anonymous
- Anonymous
November 14, 2018
It seems that we have to keep having an admin grant consent every time we add a new user for Office 365. Is this behaviour expected and is there a workaround so that all new users have the same permissions without having to have an admin grant consent every time?- Anonymous
November 14, 2018
Hello,In regards to the Graph Explorer, no. As this is the V2 AAD Endpoint, permissions are granted dynamically. To learn more info on this go to https://docs.microsoft.com/en-us/azure/active-directory/develop/v2-permissions-and-consent
- Anonymous