Using Fiddler to decipher Windows Azure PowerShell or REST API HTTPS traffic
If you are using publishsettings with Powershell, you may not be able to decrypt HTTPS traffic. Not sure what the problem is with publishsettings based certificates however I decided to create my own certificate using MAKECERT, and use it with Powershell to get HTTPS decryption working in Fiddler. The following steps are described based on my successful testing:
Step 1: First you would need to create using MAKECERT (Use VS2012 developer command prompt)
makecert -r -pe -n "CN=Avkash Azure Management Certificate" -a sha1 -ss My -len 2048 -sy 24 -b 09/01/2011 -e 01/01/2018
Step 2: Once certificate is created it will be listed in your Current User > Personal (My) store as below:
(Launch > Certmgr.msc to open the certificate mmc in Windows)
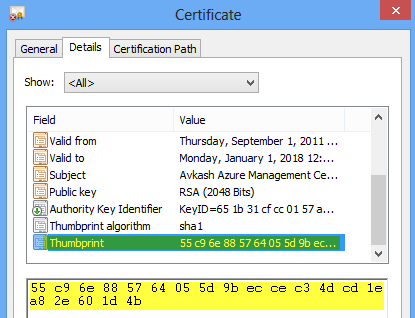
Step 3: Get the certificate Thumbprint ID and Serial Number (used in Step #13 to verify) from the certificate as below:
Thumbprint: 55c96e885764055d9beccec34dcd1ea82e601d4b
Serial Number: 85928750c5d9229d437287103ee08a79
Step 4: Now export this certificate to BASE 64 encoded certificate as below an save as CER file locally:
Step 5: Now upload your above created certificate (avkashmgmtBase64.cer) to your Windows Azure Management Portal. Be sure that the same certificate is listed as below:
Step 6: Be sure to have your Fiddler setting configure to decrypt HTTPS traffic as described here:
https://www.fiddler2.com/Fiddler/help/httpsdecryption.asp
Step 7: I would assume that you already have Fiddler installed in your machine. Now create a new copy of avkashmgmtBase64.cer as ClientCertificate.cer.
Copy this certificate @ C:\Users\<Your_User_Name>\Documents\Fiddler2\ ClientCertificate.cer
This is the certificate will be used by Fiddler to decrypt the HTTPS traffic. This is very important step.
Step 8: Now if you have already used Azure Powershell before with publishsettings then you would need to clear those settings. These files are generated every time Windows Azure Powershell connects to Management Portal with different credentials.
Go to the following folder and remove all the files here:
C:\Users\<Your_user_name>\AppData\Roaming\Windows Azure Powershell
Note: if you have Powershell settings based on previous publishsettings configuration this step is must for you.
Step 9: Now create a powershell script and using your certificate Thumbprint which you have collected in step #3 above:
$subID = "_your_Windows_Azure_subscription_ID" $thumbprint = "55c96e885764055d9beccec34dcd1ea82e601d4b" $myCert = Get-Item cert:\\CurrentUser\My\$thumbprint $serviceName = "_provide_some_Azure_Service_Name" Set-AzureSubscription –SubscriptionName "_Write_Your_Subscription_Name_Here_" -SubscriptionId $subID -Certificate $myCert Get-AzureDeployment $serviceName |
Step 10: Run the above powershell script without without Fiddler running and verify that it is working.
Step 11: Once step #10 is verified, start Fiddler and check HTTP decryption is enabled.
Step 12: Run the powershell again and you will see that HTTPS traffic shown in the Fiddler shows decrypted data.
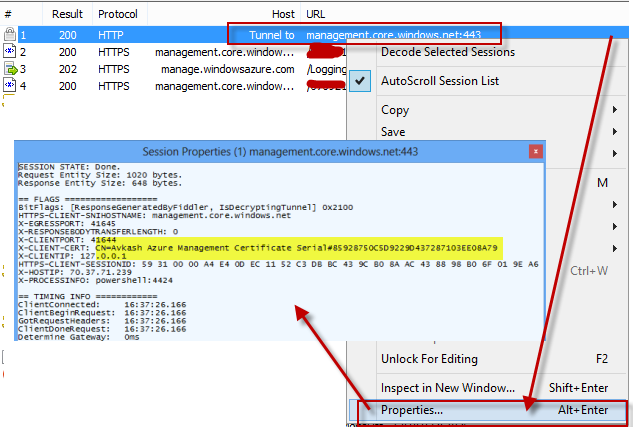
Step 13: To verify that you are using the correct certificate with Fiddler, what you can do is to open the first connect URL (Tunnel to -> management.core.windows.net:443) and select its properties. In the new windows you can verify that
X-CLIENT_CERT is using the same certificate name which you have created and its serial number match which you have collected in step #3.
Many thanks to Bin Du, Phil Hoff, Daniel Wang (AZURE) for helping me to get it working.
Tags: Windows Azure, Powershell, Fiddler, HTTPS, HTTPSDecrypt
Comments
Anonymous
June 20, 2014
If the private key (for ClientCertificate.cer) is installed in LocalMachineMy (instead of CurrentUserMy), Fiddler.exe must be launched as admin to have permission to read the private key file.Anonymous
June 22, 2015
Indeed a nice article. Somehow its not working on my machine I tried all the steps however I am still getting the "Forbidden Error" Get-AzureDeployment : ForbiddenError: The server failed to authenticate the request. Verify that the certificate is valid and is associated with this subscription.
- Get-AzureDeployment $serviceName
-
+ CategoryInfo : CloseError: (:) [Get-AzureDeployment], CloudException + FullyQualifiedErrorId : Microsoft.WindowsAzure.Commands.ServiceManagement.HostedServices.GetAzureDeploymentCommand The fiddler version is 4.5 OS: Windows server 2008 R2 I am presuming that fiddler is unable to find the ClientCertificate.cer Any help will be appreciable. Thanks in Advance