EBS Admin Console Crashes with System.Xml.XmlException: '', hexadecimal value 0x01, is an invalid character.
[Today’s post comes to us courtesy of Justin Crosby and Mark Stanfill]
Symptoms
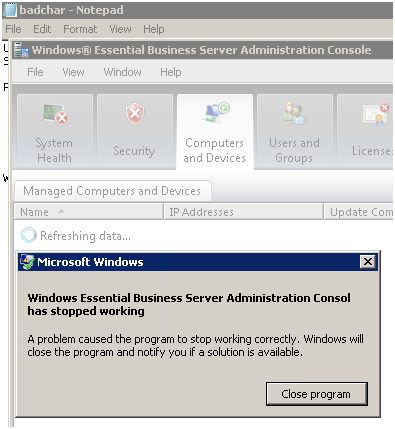
The EBS Administration Console may crash if illegal characters are present in devices reported back to WSUS and SCE. The symptoms are that the console will fail to launch, and C:\Program Files\Windows Essential Business Server\logs\AdminConsole.log will have a line similar to “System.Xml.XmlException: '', hexadecimal value 0x01, is an invalid character”. (If you don’t see this exception, this article does not apply).
C:\Program Files\Windows Essential Business Server\logs\AdminConsole.log will show an error like the following (scroll to the bottom and search up):
[16600],"2009/05/29 08:03:52.981","AdminConsole","Error","!!!!FATAL: Console shutting down due to unhandled exception: There is an error in XML document (1, 91809)."
[16600],"2009/05/29 08:03:53.022","AdminConsole","Error","System.InvalidOperationException: There is an error in XML document (1, 91809). ---> System.Xml.XmlException: '', hexadecimal value 0x01, is an invalid character. Line 1, position 91809.
at System.Xml.XmlTextReaderImpl.Throw(Exception e)
at System.Xml.XmlTextReaderImpl.ThrowInvalidChar(Int32 pos, Char invChar)
at System.Xml.XmlTextReaderImpl.ParseNumericCharRefInline(Int32 startPos, Boolean expand, BufferBuilder internalSubsetBuilder, Int32& charCount, EntityType& entityType)
at System.Xml.XmlTextReaderImpl.ParseCharRefInline(Int32 startPos, Int32& charCount, EntityType& entityType)
at System.Xml.XmlTextReaderImpl.ParseText(Int32& startPos, Int32& endPos, Int32& outOrChars)
at System.Xml.XmlTextReaderImpl.ParseText()
at System.Xml.XmlTextReaderImpl.ParseElementContent()
at System.Xml.XmlReader.ReadStartElement()
at System.Xml.Serialization.XmlSerializationReader.ReadStringValue()
at System.Xml.Serialization.XmlSerializationReader.ReadTypedPrimitive(XmlQualifiedName type, Boolean elementCanBeType)
at Microsoft.Xml.Serialization.GeneratedAssembly.XmlSerializationReaderApiRemotingCompressionProxy.Read1_Object(Boolean isNullable, Boolean checkType)
at Microsoft.Xml.Serialization.GeneratedAssembly.XmlSerializationReaderApiRemotingCompressionProxy.Read2_GenericReadableRow(Boolean isNullable, Boolean checkType)
at Microsoft.Xml.Serialization.GeneratedAssembly.XmlSerializationReaderApiRemotingCompressionProxy.Read137_Item()
at Microsoft.Xml.Serialization.GeneratedAssembly.ArrayOfObjectSerializer204.Deserialize(XmlSerializationReader reader)
at System.Xml.Serialization.XmlSerializer.Deserialize(XmlReader xmlReader, String encodingStyle, XmlDeserializationEvents events)
--- End of inner exception stack trace ---
Cause
This exception happens when a client computer reports its inventory to WSUS, and an illegal character is present in part of the data returned to WSUS. SCE in turn synchronizes this data to its database, which is queried by the console. The cases we have seen have all involved printer location strings.
Resolution
To allow the console to load properly, it is necessary to identify the problem machines, edit the bad value, and then report back to WSUS.
Identifying the problem machine
Obtain the hex code of the number from the AdminConsole.log. In the example above, it is 0x1:
System.Xml.XmlException: '', hexadecimal value 0x01, is an invalid character
Save the code below as “badchar.sql”. If your hex number is other than 0x1, determine the decimal value and substitute it for CHAR(1) in the last line of the script.
USE SUSDB
SELECT tbInventoryProperty.Name AS Field, tbInventoryClassInstance.KeyValue AS Object, tbInventoryPropertyInstance.Value AS [Bad Character],
tbComputerTarget.FullDomainName
FROM tbTarget INNER JOIN
tbInventoryClassInstance ON tbTarget.TargetID = tbInventoryClassInstance.TargetID INNER JOIN
tbInventoryPropertyInstance ON tbInventoryClassInstance.ClassInstanceID = tbInventoryPropertyInstance.ClassInstanceID INNER JOIN
tbComputerTarget ON tbTarget.TargetID = tbComputerTarget.TargetID AND tbInventoryClassInstance.TargetID = tbComputerTarget.TargetID INNER JOIN
tbComputerTargetDetail ON tbTarget.TargetID = tbComputerTargetDetail.TargetID INNER JOIN
tbInventoryProperty ON tbInventoryPropertyInstance.PropertyID = tbInventoryProperty.PropertyID INNER JOIN
tbInventoryClass ON tbInventoryClassInstance.ClassID = tbInventoryClass.ClassID AND tbInventoryProperty.ClassID = tbInventoryClass.ClassID
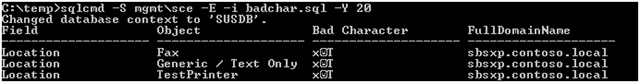
WHERE (tbInventoryPropertyInstance.Value LIKE '%' + CHAR(1) + '%')
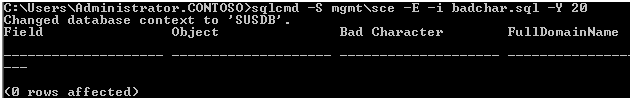
Save the script on the Management Server and run the following command:
sqlcmd -S mgmt\sce -E -i badchar.sql –Y 20
Note the value of the field, object, and bad character. Field will correspond to a registry value, object will correspond to a registry key, and bad character will correspond to the data.
Edit the bad value
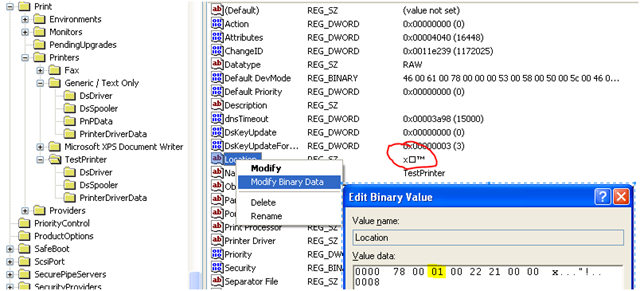
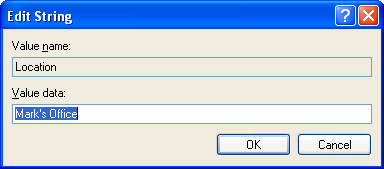
On the affected client machine, open Regedit. Export the affected key to make a backup. Locate the corresponding registry value and verify the bad character by right-clicking and choosing ‘Modify Binary Data’. The hex character should be present in the output. Cancel the edit binary value window and right-click the value to choose ‘Modify’. Enter any generic text (i.e. “Home office”). and choose OK to save.
Change to a standard string using Modify:
Report back to WSUS
On the affected client machine, run the command “wuauclt /reportnow” to update the client’s inventory. Note: It may take several hours for the values to update.
You will know that the issue is resolved when the SQL script returns zero rows.
Comments
Anonymous
January 01, 2003
242 Microsoft Team blogs searched, 98 blogs have new articles in the past 7 days. 254 new articles foundAnonymous
January 01, 2003
The comment has been removed