Windows Enterprise Client Boot and Logon Optimization – Part 8, Code Integrity Checking
This post continues the series that started here.
Today I’m going to discuss another activity that occurs across boot phases – Code Integrity checking.
Code Integrity validates driver signatures. Driver signatures may be self-contained within the driver binary – embedded-signed, or they may be stored in catalog files elsewhere on disk. Code Integrity checking is mostly associated with delays in the early stages of boot but does occasionally surface in later phases also.
When loading a driver that is not embedded-signed, Code Integrity scans all catalog files on the system, trying to locate the signature. This operation delays validation of the driver and slows down the associated boot phase which is particularly problematic for BOOT_START drivers.
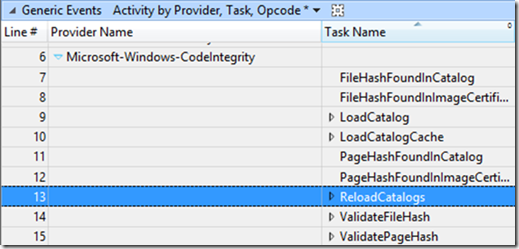
Windows Performance Analyzer (WPA) shows catalog reload events in the System Activity –> Generic Events table. Moving the Provider Name and Task Name columns to the very left provide the following view
If you see ReloadCatalogs in the Task Name column after expanding the Microsoft-Windows-CodeIntegrity provider, there’s a non-embedded-signed driver loading on the system.
How Do I Find an Offending BOOT_START Driver?
In order to find non-embedded-signed BOOT_START driver/s, you’ll need signtool.exe which is available as part of the Windows SDK. To download the latest Windows SDK, go here. After starting the installation wizard, the only option you need to check is
I recommend installing the SDK on your analysis system and if you need to validate driver signatures on a production system, flat-copy the entire signtool.exe directory from C:\Program Files (x86)\Windows Kits\8.1\bin\<architecture> .
Once you have signtool.exe in place, you can check BOOT_START drivers by first parsing a boot trace with
xperf -i trace.etl -o trace.txt -a dumper
findstr /C:"I-DCStart" trace.txt > trace.csv
Secondly, use PowerShell to read through trace.csv and execute signtool.exe against each BOOT_START driver -
$Drvrs = Import-Csv -Path .\trace.csv
ForEach ($Drvr in $Drvrs) {&'Signtool.exe' verify /v $Drvr.FileName}
Examine any errors in the output for non-embedded-signed BOOT_START drivers and contact the driver vendor in hope of an update.
Next Up
Comments
- Anonymous
August 05, 2015
The comment has been removed