Notes
L’accès à cette page nécessite une autorisation. Vous pouvez essayer de vous connecter ou de modifier des répertoires.
L’accès à cette page nécessite une autorisation. Vous pouvez essayer de modifier des répertoires.
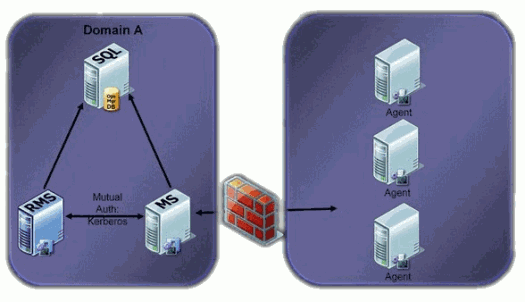
 System Center Operations Manager 2007 uses mutual authentication to communication with the agents. First the agent will try to communicate with Kerberos and when this is not possible certificates will be used for the secure communication. If you happen to have agents that lie outside of your domain, such as in a DMZ, you’ll want to use certificates for agent to server communication
System Center Operations Manager 2007 uses mutual authentication to communication with the agents. First the agent will try to communicate with Kerberos and when this is not possible certificates will be used for the secure communication. If you happen to have agents that lie outside of your domain, such as in a DMZ, you’ll want to use certificates for agent to server communication
In order to configure certificates for this communication you will need to complete the steps below:
- Importing Trusted Root certificate - all servers
- Creating and installing Server (Client, Server) Certificates - OpsMgr servers
- Creating and installing Server (Client, Server) Certificates – Workgroup and/or DMZ servers
- Export the Server (Client, Server) Certificate
- Allow manual agent installation.
- Manual OpsMgr 2007 agent installation
- Running MOMcertimport on the servers - all servers
- Approve agent
- Create Run As Account
- Change default Action Account Run As profile
Additional steps:
- Issue new certificates from the Standalone Root CA
1. Importing Trusted Root certificate.
On all servers (RMS, Management server and all Workgroup servers):
- Logon to the Root Management Server with administrative privileges and navigate to the certificate server web site with https://standaloneCAroot/cersrv
- Click on “Download a CA certificate, certificate chain or CRL”
- Click on “Download Ca certificate chain”
- Save the “certnew.p7b” to the “c:\” (or some place you want)
- Click start run “MMC” and from the file menu “Add/remove Snap-in..” select
- Click “Add”
- Select “Certificates”
- Click “Add”
- Select “Computer account”
- Click “Next”
- Select “local computer”
- Click “Finish”
- Click “Close” and “Ok” to access the Certificates console.
- Navigate to the folder “Trusted Root Certification Authorities”
- Right kill the “Certificates” folder and select “All Tasks” and “Import”
- In the wizard kill “Next”
- Click “Browse” and browse to the “certnew.p7b” on the “c:\” (or some place you put it)
- Click “Next”
- Select “Place all certificates in the following store” and make sure the Certificate store is “Root Certification Authorities” and kill “Next”
- Click “Finish” to complete the import.
- Delete the “certnew.p7b”
- The import of the trusted root certificate is finished
2. Creating and installing Server (Client, Server) Certificates
For the root management server(RMS) and management server(MS):
- Logon to the Root Management Server with administrative privileges and navigate to the certificate CA server web site with https://standaloneCAroot/cersrv
- Click “Request a certificate”
- Click “advanced certificate request”
- Click “Create and submit a request to this CA”
- Use the following for the certification request:
- Name: Managementserver.domain.com
- Type: Other
- OID: 1.3.6.1.5.5.7.3.1, 1.3.6.1.5.5.7.3.2
- Select: Mark key as exportable
- Select: Store certificate in the local computer certificate store
- Friendly name: Managementserver.domain.com
- Click “Submit”
- Close Internet explorer
- Let the certificate be issued on the Standalone Root CA (see how to: 1. Issue new certificates from the Standalone Root CA).
- Navigate to https://standaloneCAroot/cersrv
- Click “View status of a pending certificate request”
- Click the Issued certificate
- Install the issued certificate
3. Creating an installing Server (Client, Server) Certificates
For workgroup and/or DMZ server:
- Logon to the workgroup server with administrative privileges and navigate to the certificate CA server web site with https://servername/certsrv
- Click “Request a certificate”
- Click “advanced certificate request”
- Click “Create and submit a request to this CA”
- Use the following for the certification request:
- Name: Server name
- Type: Other
- OID: 1.3.6.1.5.5.7.3.1, 1.3.6.1.5.5.7.3.2
- Select: Mark key as exportable
- Select: Store certificate in the local computer certificate store
- Friendly name: Server name
- Let the certificate be issued on the Standalone Root CA (see how to issue a certificate from a standalone Root CA).
- Navigate to https://standaloneCAroot/cersrv
- Click “View status of a pending certificate request”
- Click the Issued certificate
- Install the issued certificate
4. Export the Server (Client, Server) Certificate
This must be done on all Workgroup/DMZ servers, root management server(RMS) and management servers (MS):
- Logon to the Server with administrative privileges
- Click “Start => Run” “MMC” and from the file menu “Add/remove Snap-in..” select
- Click “Add”
- Select “Certificates”
- Click “Add”
- Select “Computer account”
- Click “Next”
- Select “local computer”
- Click “Finish”
- Click “Close” and “Ok” to access the Certificates console.
- Navigate to the folder “Certificates (Local Computer)\personal\Certificates”
- Select the new installed Client, Server certificate and right kill “All tasks => Export”
- In the new wizard kill “Next”
- Select “Yes , Export the private key”
- Click “Next”
- Select “Personal Information Exchange – PKCS #12 Certificates (PFX)”
- Select “Enable Strong protection (requires IE5.0, NT4 SP4 or above)”
- Click “Next”
- Type a password for the certificate twice and kill “Next”
- Select “Browse” c:\serverFQDN.pfx”
- Click “Next”
- Check the export information and if correct kill “Finish”
- Click “OK” to finish the export
- Close the MMC
5. Allow manual agent installation.
Before the first manual agent installation, the global setting must be changed from reject to “Review new manual agent installation in pending management view” in the operations console of OpsMgr 2007:
- Open a Operations Console with OpsMgr administrative privileges
- Navigate to “Administration => Settings => Server”
- In the right pane click “Security”
- On the “General” tab select “Review new manual agent installation in pending management view”
- Click “OK” to finish
6. Manual OpsMgr 2007 agent installation
On the workgroup and/or DMZ servers:
- Logon to the Server with administrative privileges
- On the Operations Manager 2007 installation media, double-click the SetupOM.exe file.
- On the Start page, select Install Operations Manager 2007 Agent.
- On the Welcome page, click “Next”.
- On the Destination Folder page leave the installation folder set to the default click “Next”.
- On the Management Group Configuration page leave the Specify Management Group information check box selected, and then click “Next”.
- On the Management Group Configuration page, do the following:
- Type the Management Group Name
- Type the Management Server name.
- Leave the default 5273.
- Click Next.
- When the Agent Action Account page displays leave it set to the default of Local System and then click Next.
- On the Ready to Install page, review the settings and then click Install to display the Installing Systems Center Operations Manager Agent page.
- When the Completing the Systems Center Operations Manager Agent Setup Wizard page displays, click Finish.
7. Running MOMcertimport.exe on the servers.
This must be done on all servers. Also make sure the exe which you use is of the same version (for 32-bit and 64 bit we have separate exe’s) and also make sure the files from the same version dump of the SCOM server \ agent you are running on the system):
- On the start menu kill “Start” and “Run”
- Type “cmd”
- Navigate to > cd “program files\System Center Operations Manager 2007\Supportools\i386”
- Type >MOMcertimport.exe “c\:servername.domain.com.pfx” or “c:\servername.pfx”
- Type the asked password for the certificate import and press “Enter”.
- The certificate is now imported in OpsMgr 2007.
- Restart the “OpsMgr Health Service” on the server.
8. Approve agent
In the System Center Operations Manager Console, after every manual agent installation the new agent must be approved in the operations Console of OpsMgr 2007:
- Open the Operations console as an OpsMgr Admin member.
- Navigate to “Administration => Pending Management”
- Right-click “Approve”
- Click “Approve”
To check if the agent is successfully approved look in the “Agent Managed” folder for the approved agent to see if the agent is there.
9. Create Run As Account
In the System Center Operations Manager Console:
- Open a Operations Console with OpsMgr administrative privileges
- Navigate to “Administration => Security => Run As Account”
- Right-click “Run As Account” and select create run as account
- In the Create Run As Account Wizard click “Next”.
- Select “Action account” in the Run As Account type list
- Type a display name in the Display Name text box
- Click Next
- On the Account page, type:
- Server name\username
- Password
- The domain should be grayed out (Local machine account).
- Click Create to finish
- Change default Action Account Run As profile
10. Change default Action Account Run As profile
In the System Center Operations Manager Console:
- Open a Operations Console with OpsMgr administrative privileges
- Navigate to “Administration => Security => Run As Profiles”
- In the right pane double click the “Default Action Account”
- Click on the “Run As Account” tab
- Select “Run As Account: “dropdown menu and select the workgroup server local account
- Click “OK” and click “OK
That should be it, but in case you need more information please see Authentication and Data Encryption for Windows Computers in Operations Manager 2007.
Hope this helps,
Sudheesh Narayanaswamy | Operations Manager Support Engineer
Comments
Anonymous
January 01, 2003
what is meant here by all servers is teh RMSMSGateway and the clients ...Not all servers on your network.Anonymous
January 01, 2003
Step 2.5.e which asks you to select the local computer store is not available. Is it because of the CA type? I am using Server 2008 R2 SP1.Anonymous
January 01, 2003
Does this procedure also work in OpsMgr 2012?Anonymous
January 01, 2003
HI, I have this issue I have issue the certficate for non-domain server signed my AD CA, placed in local-personal folder. This cert have private key included. When I start MOMCertImport /SubjectName server.domain.local, in Local-Operation Manager folder i receive selfsigned certificate server.domain.local. There is no signed with ma AD CA :-(Anonymous
July 20, 2010
The comment has been removedAnonymous
June 22, 2011
Thanks for this! Why does step 7 have to be done all servers? I just want 1-3 servers outside our domain for monitoring our hosted URLs, but I am not sure I follow why we have to touch all server within our network to do this.Anonymous
May 17, 2012
The comment has been removedAnonymous
May 30, 2012
The comment has been removedAnonymous
December 15, 2013
The port in the step 6 is wrong, it should be 5723Anonymous
December 15, 2013
Another bit. In the steps 3.a and 3.f, it should be "full computer name", as I've just spent hours playing with a Lync edge server which has a computer name: servername and a full computer name: servername.domain.com. You guess, creating a cert and entering only the computer name didn't work, so I had to recreate it with the full comp name (servername.domain.com), even though the server is in a workgroup, and reimport the cert, and then it worked.Anonymous
December 15, 2013
The correct steps mentioned above are 3.5.a and 3.5.f.Anonymous
August 28, 2014
how to renew the Trusted Root certificate when it going to expired.Anonymous
December 03, 2015
The comment has been removed