Effective Rights - What can users do?
I guess I'm not the only one that have been sitting and wondering .. Hmm.. What permissions does these users got in Active Directory actually? I can see a lot of groups in the access control list but how do I relate that to a certain user.
Ok, we got the Effective Rights tab under Advanced Security. But it does not show everything I expect it to do.
https://support.microsoft.com/kb/933071/en-us
I have used it from time to time and it has been a nice complement to investigating the actual permissions.
But it's hard to get a good overview of permissions, since you can't export the result or do more than one object at a time.
To address this problem I have added more functionality to the AD ACL Scanner tool.
https://adaclscan.codeplex.com/
How to scan effective rights for a user with AD ACL Scanner:
- Download and launch the script in Powershell.
- Click Connect or List Domains if you would like to select and connect to another domain then you default.
- Browse to the object you would like to scan for effective rights and select it.
- Click on the Effective Rights tab and check "Enable Effective Rights".
- Type the samAccountName of the user/Group or computer in the textbox. You could choose an object from a trusted domain if you first click Locations... And select the domain name.
- Click Get Account and the Selected Security Principal field should be filled in. If you like you can take a look at all contributing memberships this account got by clicking View Account.
- Press Run Scan to generate the report.
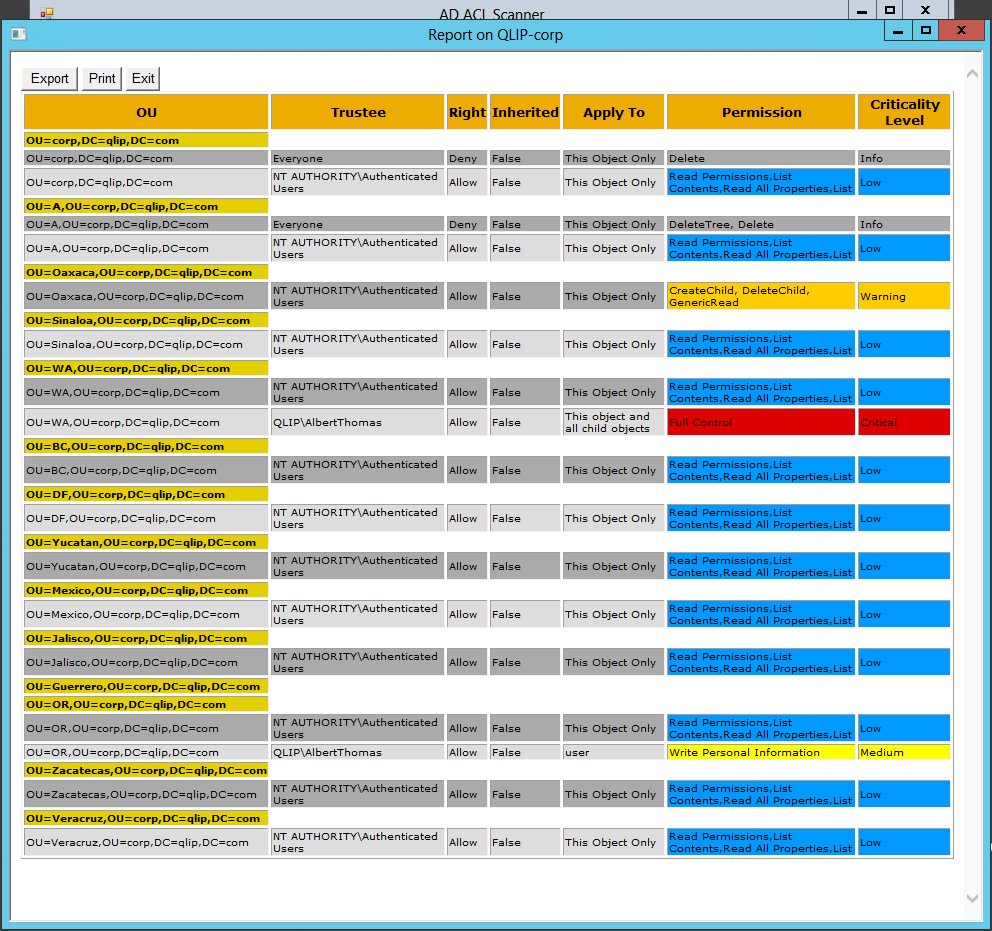
The result will show all permissions this account is granted through its memberships.
Why will not all Well-known SIDs be evaluated?
There are several Well-known security identifiers (SIDs) you should not expect the report to match against.
Well-known SIDs https://msdn.microsoft.com/en-us/library/windows/desktop/aa379649(v=vs.85).aspx
2.4.2.4 Well-Known SID Structures https://msdn.microsoft.com/en-us/library/cc980032.aspx
Why is this not in the tool?
Because first of all the account to be evaluated has to logon or be impersonated through all these scenarios to get these SIDs.
The second reason is that they are relative self explanatory. If I have granted users permissions to create group objects as a member of INTERACTIVE, they need to logon interactively
on a DC and make sure they point the tool or LDAP operation to the local machine to be able to create a group.
Well-known security identifiers (SIDs) generated at logon that is evaluated
- Everyone
- Authenticated Users
- This Organization (All accounts in all trusted forests)
- Other Organization (Accounts from an incoming domain or forest trust with Selective Authentication )
If you really would like to know if a user with the Well-knonw SID INTERACTIVE have permissions in AD you could use the filter function in AD ACL Scanner and filter for "NT AUTHORITY\INTERACTIVE" as Trustee
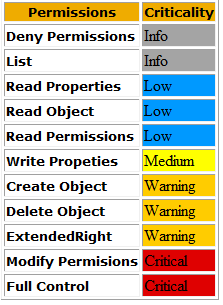
How to quickly determine the degree of permissions in the report?
To do that I have added a function that will mark the permissions with color codes based on the criticality of the permissions according to this table:
All you have to do is check the box "Show color coded criticality" and run a scan.
Works only for Effective Rights reports.
This is not optimal but I hope it will give you a hint on accounts with high privileges.
You have probably another view on what is critical or not depending on the situation you have.
For example I think it is more critical to create user objects than shared folder objects, since user objects are security principals.
For example I think Write Properties permissions to the Personal-Information property set would not be considered as Medium while Write Properties to pwdLastSet on user objects could be considered as critical.
I suggest all of you to create an administrtive model using Roles-Based Approach with the principle of least privilege in assigning rights and permissions.
Hopefully this tool simplify the work of building an administrative model.
Download tool from here: AD ACL Scanner https://github.com/canix1/ADACLScanner
Suggested reading Best Practices for Securing Active Directory
Comments
- Anonymous
January 01, 2003
thank you