Application Portfolio Management (APM)
Vineet Batta here….This is a short introduction to the Application Portfolio Management (APM) component of the Connected Information Security Framework or CISF that we hope to reach the CTP milestone in next 2-3 weeks. The APM component is designed to let you couple this lightweight application portfolio management system with your exiting development processes so you can track applications as they move through various life cycle stages of security reviews in your organization. With the plan to release it as an open source component organizations using it can extend it by themselves as required to meet their exact needs and tightly integrate it into their process.
At high level the feature set consists of the following:
Application Entry\View\Edit
The Application Portfolio Management (APM) tool allows you to enter metadata for new and existing applications. This metadata defines the application name, organization type, version, start and completion dates, extended properties, and who to contact for the application.
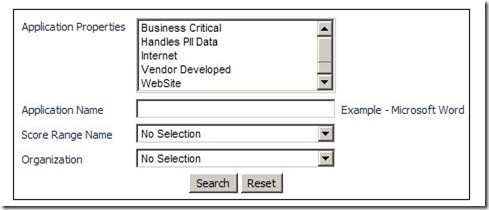
Advance Search
The Application Portfolio Management (APM) tool Advanced Search allows you to search by application properties, application name, score range, and organization. Once the tool has completed the search, you can click the application ID to view the application's ‘Application Entry’.
Workflow\Tasks
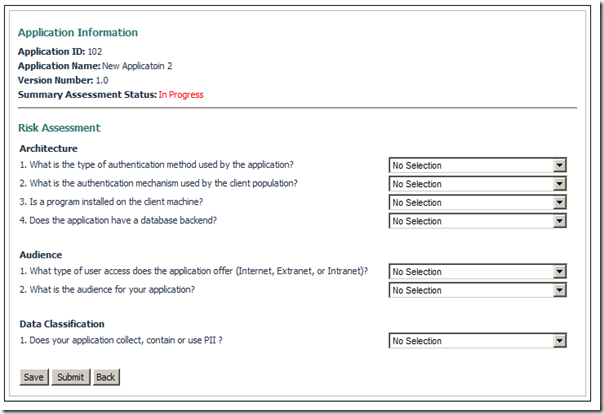
The Risk Impact Assessment (RIA) lets you categorize the application, depending on the answers the user gives in the assessment. Based on the assessment answers the list of task is generated automatically for you.
Sample questionnaire which can be changed latter -
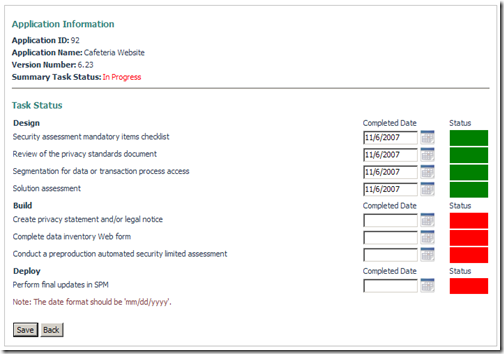
Update Task Status
The users can also update the task completion dates in the system. The Update Task Status page displays the status and details of an application's Task Risk Impact Assessment (RIA). A status display of GREEN indicates tasks that you have completed; a status display of RED indicates tasks you still need to complete.
Sample:
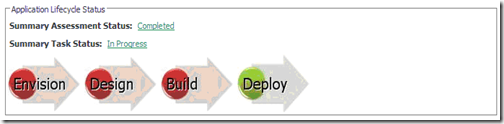
Tracking
The tool helps you to track the progress of the application through Application Lifecycle Stages as below.
More details on other features coming soon including how to integrate threat models into the APM. Stay tuned…
Vineet Batta